iAnywhere Afaria
Managing mobile devices and the flow of mobile data remains one of the most daunting tasks for the network manager. IT PRO shows you how you can use Afaria from iAnywhere to simplify the process.

Step 1: Understanding the handset client
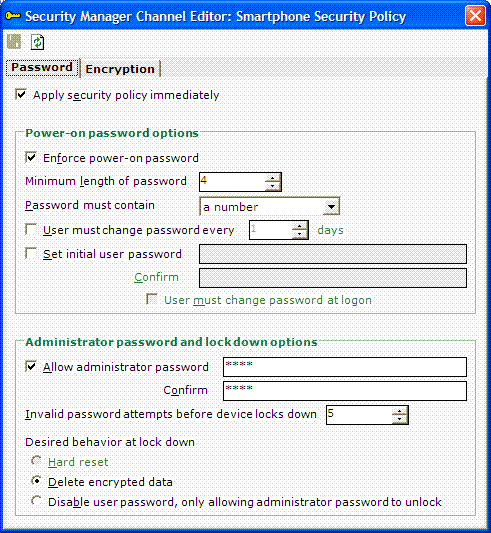
Step 2: Security policies
Step 3: Orientation settings
Step 4: Understanding device and language support
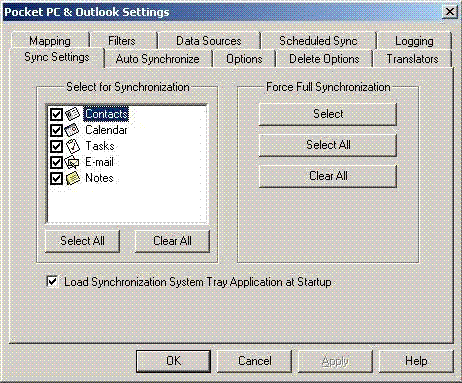
Step 5: Controlling data syncing
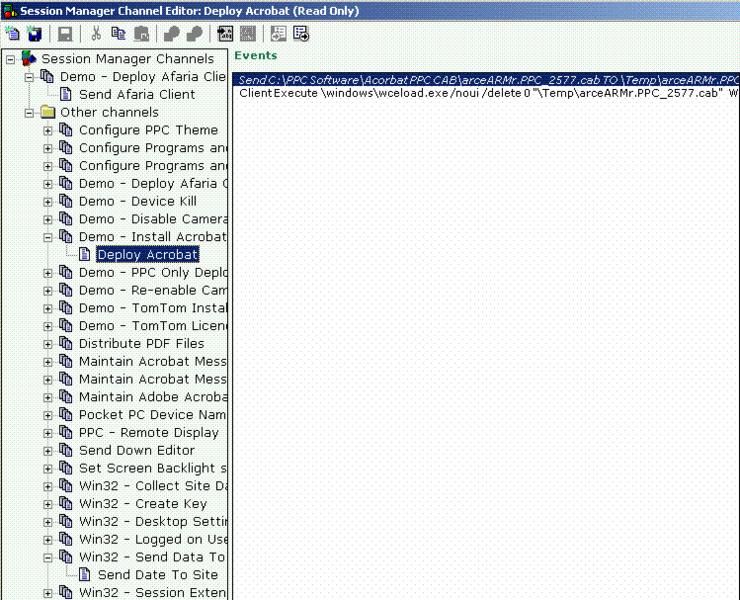
Step 6: Manipulating files and registry
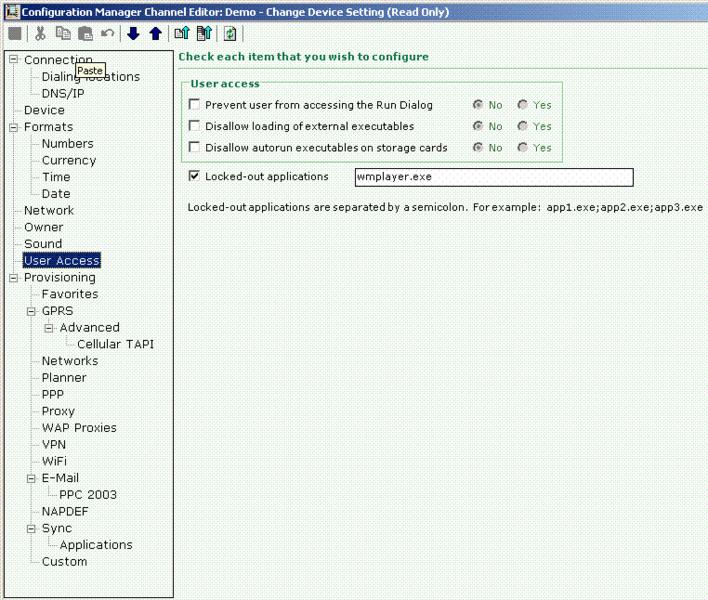
Step 7: Controlling device settings
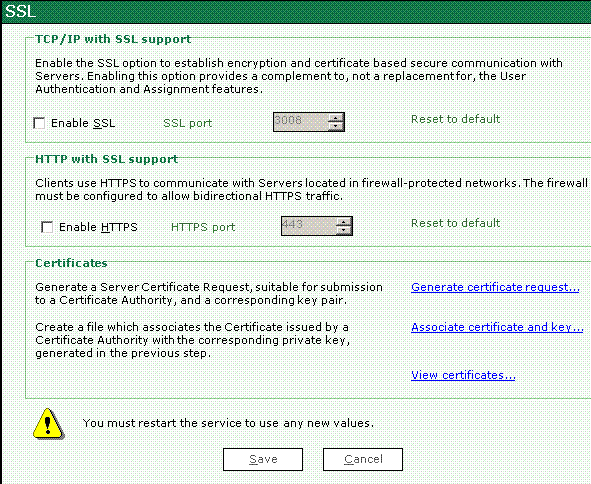
Step 8: Security options
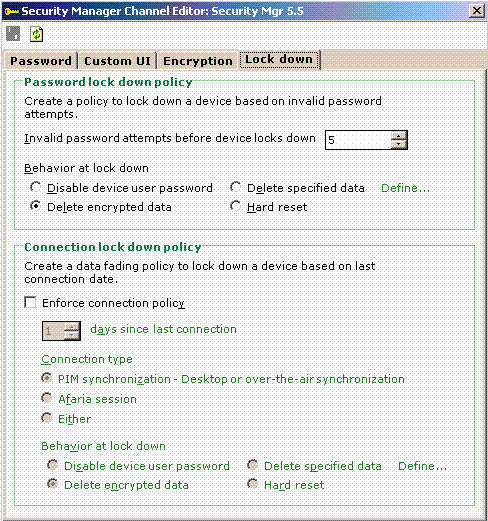
Step 9: Lock down policy
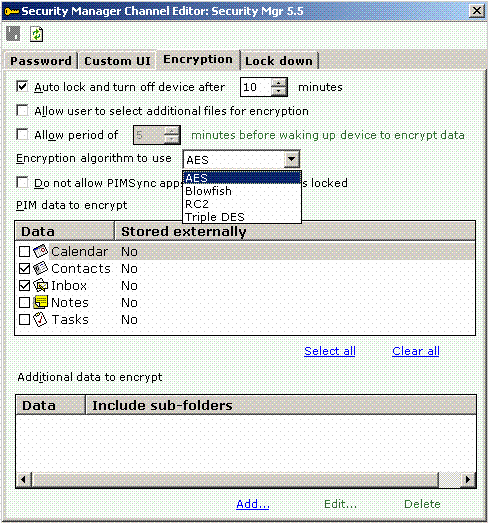
Step 10: Using encryption
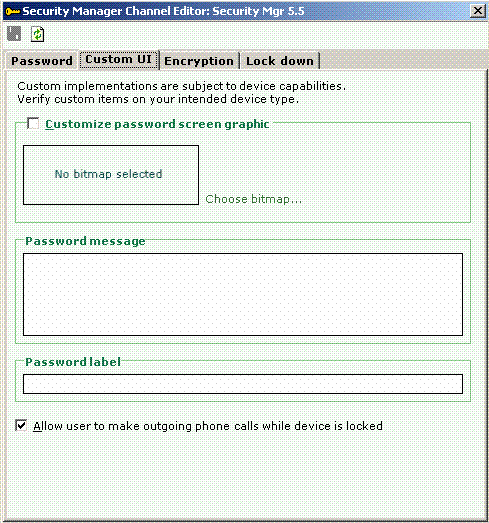
Step 11: Customise the user interface
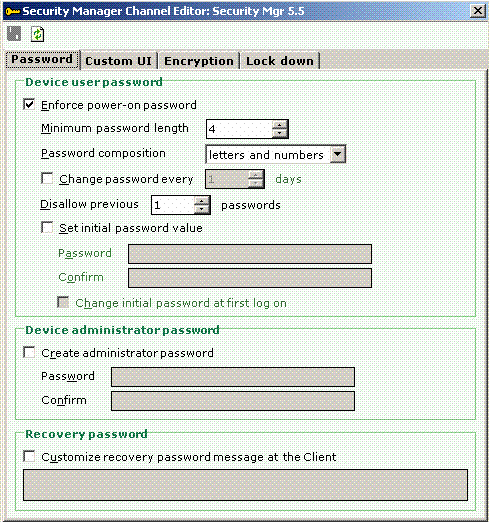
Step 12: Setting passwords
Managing mobile devices and mobile data remains one of toughest tasks for the network manager, despite the increasing number of tools on the market that promise to make it easier. As a subset of the overall management task, security probably figures large in the concerns of most managers. iAnywhere, a subsidiary of database vendor Sybase, has developed a number of software products for the management of corporate mobility. One of these is Afaria, which has security concerns at its heart.
iAnywhere says Afaria lets network managers proactively manage all the devices, applications, data and communications critical to frontline mobile working. It says the software allows central control of mobile sales people, field service engineers, workers in remote offices and retail sites, while giving control and visibility of the devices used by these workers to corporate headquarters.
Afaria works via a Microsoft .Net-based console, letting managers control activities from a browser, through a number of system components. Here we show how Afaria delivers this control through those components, and how it can be configured for maximum effectiveness.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives