Creating a mobile data management policy
The take-up of smartphones are in the mass market means enterprises are having to cope with everything from 3G cards to Sidekicks.


Which platform is right for the enterprise?Linux handhelds are not yet common but many enterprises will need to support BlackBerry devices as well as Windows Mobile or Symbian (as Nokia brings out more enterprise E series models).
RIM provides strong security and management options in BES and Microsoft is moving towards the same OMA-DM provisioning and management standards that Symbian supports for newer devices, but third-party products like HP's Bitfone Enterprise Mobility Suite can manage multiple mobile operating systems. Consider middleware and device management software that can translate applications for multiple platforms rather than rewriting them individually. Make it clear which versions you support; Windows Mobile 5 and 6 have better security and manageability than earlier versions and while Nokia N series devices can run Mail 4 Exchange they won't receive messages unless you turn off device security on your server because the hardware doesn't support the necessary encryption.
Draw a distinction between devices you will allow to connect and those you will support fully. Your policy should ban devices that have not been registered with or certified by the IT department from connecting to the enterprise network, but banning the latest gadgets will cause complaints and attempts to work around your security (such as forwarding email to open-access Webmail systems). Avoid this by allowing users to register all suitable devices with the IT department for email connectivity but make it clear they'll get limited support with problems and devices will be restored to the default configuration when the employee leaves the company. Apply the same Web content filtering to mobile devices as to PCs and tell users how much memory needs to be left free for updates and adequate performance of your line of business applications. Decide whether you will back up personal devices in the same way you do issued devices, make it clear what applications can and can't be installed- and what costs can be expensed. Adult content is inappropriate on a personal device connecting to the corporate network, but you may be less concerned about users installing games than how much they spend calling or texting overseas numbers.
Currently the majority of enterprises pay for connectivity directly, according to Forrester; around a quarter allow employees to claim the cost a connection on expenses, but almost as many have no set policy. But mobile contracts and data tariffs continue to be confusing according to Gartner's research vice president Martin Gutberlet. Where you're rolling out your own devices or managing contracts yourself, look for flexible tariffs, clear reporting and service level agreements covering support as well as connection performance. Operators think in terms of SIMs and a discount on total usage, but you should be able to share a pool of bandwidth among users; if one user exceeds their bandwidth limit and another is well under it, you should be able to offset the lower usage to avoid paying for the higher usage. Mobile devices don't stay in use as long as desktops and notebooks; expect to have to replace them every 12 months and consider contracts that refresh devices as new models come out.
Operator-run web sites allowing end users to disable lost and stolen handsets are increasingly common and some operators have agreements enabling multiple connections for a single price; Orange Business Everywhere v6 incorporates the iPass client so users get seamless access via 3G, Wi-Fi, EDGE, dial-up, home DSL or any other connection that's available. The iPass service is available directly if you use another operator, and Fiberlink offers similar features. Both include device management and remote termination as well as reducing costs; you'll pay for a local 3G connection rather than roaming costs when users connect from abroad, for instance, and hotspot access is included in a single fee so you don't have to deal with individual hotel bills and expense claims. If you don't choose a unified access provider, set firm limits for what expenses are allowable for voice, data, Wi-Fi and home broadband usage and how this needs to be documented. Profile different user groups; limits may need to be different for international travellers and heavy data users who don't leave the country.
Securing the mobile deviceSecurity starts with device passwords. According to Microsoft, only a quarter of users lock their mobile devices with a PIN or password currently. Enforce password changes at the same frequency as you do for PCs, lock devices if the password is entered incorrectly three times in a row and require passwords to be re-entered regularly. Force encryption of removable media and turn off Bluetooth to avoid attacks unless you use specific hardware like GPS receivers. Protect data that could be copied or sent to phones at the source by enforcing rights management or blocking email redirection.
Don't just think about spiraling costs or the risk of losing data when you put your policy together; you want an approach that takes advantage of the productivity opportunities mobile devices can bring, so think about appropriate access rather than just locking things down. "We need to stop fighting technology wars and start fighting business wars," cautions Lopez; "mobility is an extension of what you already do". And the ROI on mobile projects is going to be even better if you can incorporate personal devices that you don't have to pay for, so it's worth dealing with the complexity of managing them.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
There are even solutions for the notoriously enterprise-unfriendly iPhone. WebEx PCNow 3 lets iPhone users check Outlook email or view files by remoting into their Windows PC and Visto Mobile gives users access to corporate email, including Word and Excel attachments, without changing the security settings on your mail server or firewall.
Mary is a freelance business technology journalist who has written for the likes of ITPro, CIO, ZDNet, TechRepublic, The New Stack, The Register, and many other online titles, as well as national publications like the Guardian and Financial Times. She has also held editor positions at AOL’s online technology channel, PC Plus, IT Expert, and Program Now. In her career spanning more than three decades, the Oxford University-educated journalist has seen and covered the development of the technology industry through many of its most significant stages.
Mary has experience in almost all areas of technology but specialises in all things Microsoft and has written two books on Windows 8. She also has extensive expertise in consumer hardware and cloud services - mobile phones to mainframes. Aside from reporting on the latest technology news and trends, and developing whitepapers for a range of industry clients, Mary also writes short technology mysteries and publishes them through Amazon.
-
 Why keeping track of AI assistants can be a tricky business
Why keeping track of AI assistants can be a tricky businessColumn Making the most of AI assistants means understanding what they can do – and what the workforce wants from them
By Stephen Pritchard
-
 Nvidia braces for a $5.5 billion hit as tariffs reach the semiconductor industry
Nvidia braces for a $5.5 billion hit as tariffs reach the semiconductor industryNews The chipmaker says its H20 chips need a special license as its share price plummets
By Bobby Hellard
-
 Microsoft is ending support for the Remote Desktop app – here are three alternatives you can try instead
Microsoft is ending support for the Remote Desktop app – here are three alternatives you can try insteadNews Microsoft has announced plans to end support for its Remote Desktop application in just over two months.
By George Fitzmaurice
-
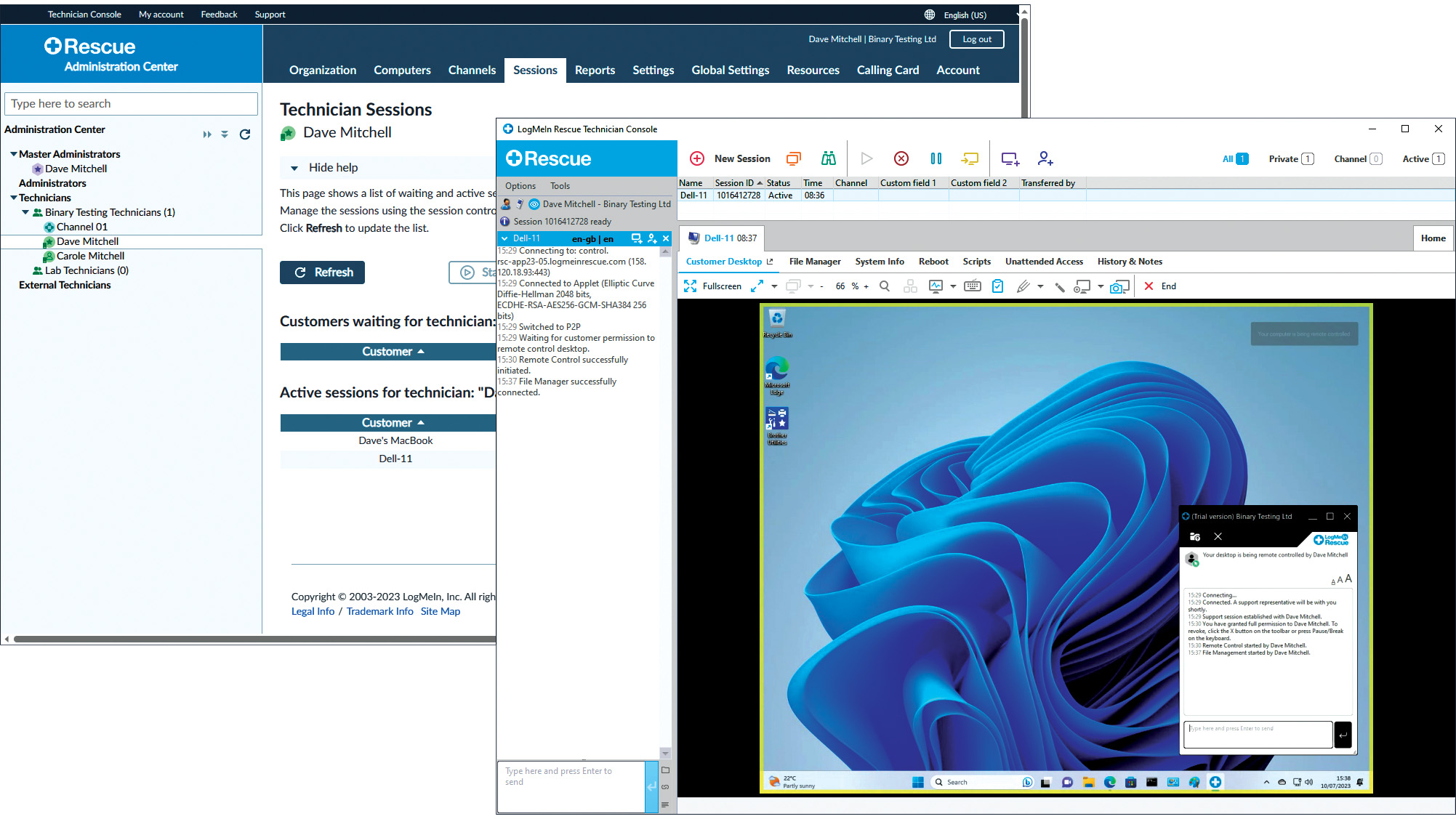 LogMeIn Rescue review: For those who want the strictest access security for their remote support services
LogMeIn Rescue review: For those who want the strictest access security for their remote support servicesReviews LogMeIn Rescue delivers an easily deployed cloud-hosted support solution with top-notch access security
By Dave Mitchell
-
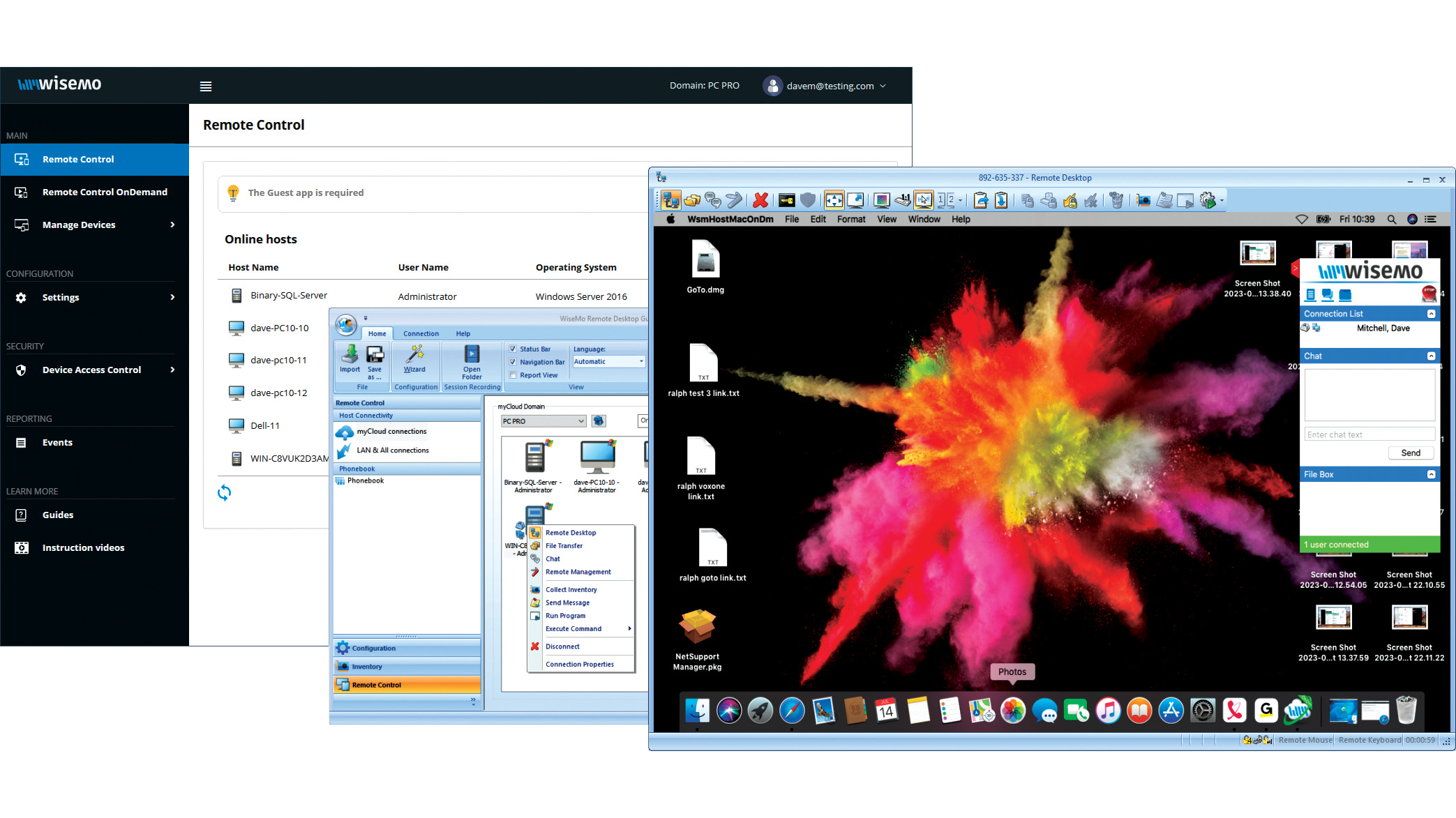 Wisemo Remote Control review: Ideal for businesses that want versatile connection options
Wisemo Remote Control review: Ideal for businesses that want versatile connection optionsReviews A smart hybrid support solution with great access security and a connection for every occasion
By Dave Mitchell
-
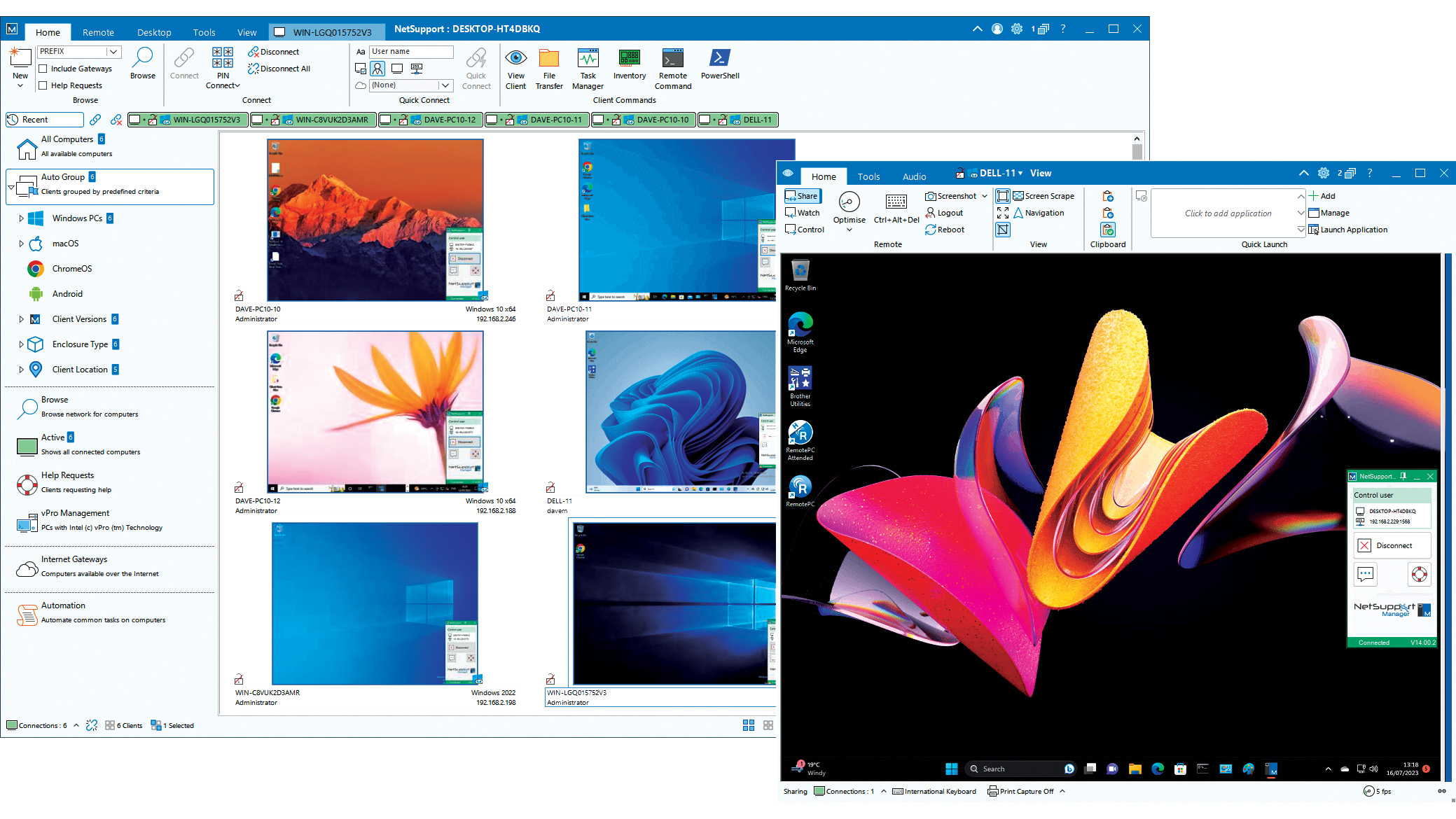 NetSupport Manager 14 review: Delivers a wealth of support tools
NetSupport Manager 14 review: Delivers a wealth of support toolsReviews The perfect on-premises support solution with a wealth of valuable features and simple licensing
By Dave Mitchell
-
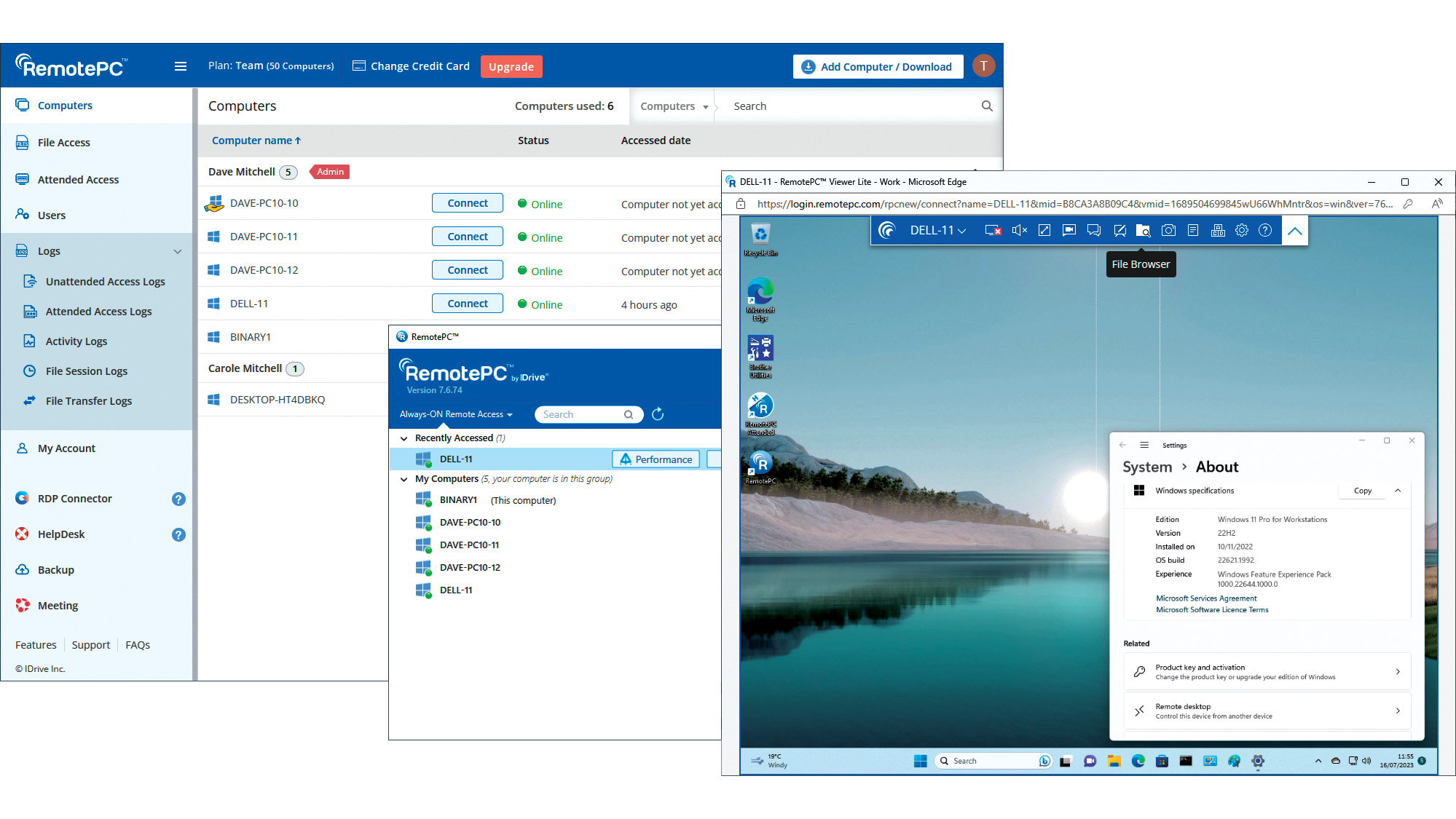 IDrive RemotePC Team (2023) review: Affordable cloud-hosted remote support
IDrive RemotePC Team (2023) review: Affordable cloud-hosted remote supportReviews Secure cloud-hosted remote support that's easy to use, rich in features and exceptional value for SMBs
By Dave Mitchell
-
 ZTNA vs on-premises VPN
ZTNA vs on-premises VPNWhitepaper How ZTNA wins the network security game
By ITPro
-
 Getting the best value from your remote support software
Getting the best value from your remote support softwareAdvertisement Feature Value is about much more than just the initial costs involved, so careful consideration must be given to any purchase
By Jane McCallion
-
 Why you need a cloud solution for your remote support
Why you need a cloud solution for your remote supportAdvertisement Feature With distributed workforces and a broad user base, modern businesses are looking for modern software
By Jane McCallion