Is the password ill-equipped for the modern world?
It’s been around since pretty much the dawn of computing, but can the humble password ever again be regarded as secure?

IT departments the world over would no doubt share in the feeling that no matter how much time and effort you put into an IT infrastructure, there's little you can do to legislate against human beings.
More specifically, the actions of users who have an unmatched ability to put the best laid plans to waste. We've seen it several times of late, with Government officials losing memory sticks, discs going walkabout in the post, and confidential data appearing on the streets seemingly like chewing gum gets attracted to a pavement. And that's just the stuff they tell us about.
Yet, while usually generating less headlines, an increasing number of IT workers are citing the humble password as one of the biggest security threats that they face. And you can't help but see their point. After all, a word that can be as short as six characters long is often the only real line of defence between an organisation's network and the outside world.
And unsurprisingly, that's simply not being seen as enough.
The issues
The password has ridden on the back of the computer revolution of the past few decades, and has arguably become the one facet of security that users have the most trouble with. Not because they're unable to come up with a password, or anything of that ilk. No, the problems run deeper than that.
For this word, that is a key of sorts to a company's technological infrastructure, is either easy to guess, frivolously given out, or worst of all stuck to the monitor on a Post-It note. DTI research in 2007, that we previously reported on, found that over a third of users recorded their password somewhere close to their terminal.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Furthermore, researchers in the past have even found that brazenly walking up to strangers on the street and asking people their password has a higher than expected success rate, thus immediately rendering moot whatever security infrastructure has been put in place. If people will tell a password to strangers, how more likely are they to blab it to people that they do know?
Yet no matter what level of business people operate at, it seems that passwords have rarely been more compromised. And what's more, it's not just the passwords themselves that are the problem, but the follow-up level of security that's been put in place to protect them. After all, most of us have forgotten a password at some point in our life, or needed it to be reset. But the process of doing just that can be equally fraught with holes.
Presidential passwork cracking
The most obvious high-level example in recently was Republican nominee for the US Vice-Presidency, Sarah Palin. Her Yahoo email password was quickly and easily beaten by a sole hacker. In under an hour, potentially one of the most powerful politicians in the world had found her e-mail account accessed, and select details leaked onto the web.
How was this achieved? Simple. The hacker in question worked out the relatively easy to discover answers to Palin's security questions and these tend to vary between memorable places, names of pets and such like (information that's often freely given away on social networking sites) and managed to get her password reset. Through a simple Forgotten Your Password?' link lay the tools to access someone's entire e-mail account.
Now granted, the protection afforded to webmail doesn't tend to equal that of a proper company infrastructure, but how many employees of big companies don't have a webmail account? And how many can say they do no confidential work business whatsoever through a webmail service? Not for nothing are such services the bane of an IT department's life.
-
 Should AI PCs be part of your next hardware refresh?
Should AI PCs be part of your next hardware refresh?AI PCs are fast becoming a business staple and a surefire way to future-proof your business
By Bobby Hellard
-
 Westcon-Comstor and Vectra AI launch brace of new channel initiatives
Westcon-Comstor and Vectra AI launch brace of new channel initiativesNews Westcon-Comstor and Vectra AI have announced the launch of two new channel growth initiatives focused on the managed security service provider (MSSP) space and AWS Marketplace.
By Daniel Todd
-
 Iranian hackers targeted nuclear expert, ported Windows infection chain to Mac in a week
Iranian hackers targeted nuclear expert, ported Windows infection chain to Mac in a weekNews Fresh research demonstrates the sophistication and capability of state-sponsored threat actors to compromise diverse targets
By Richard Speed
-
 The top malware and ransomware threats for April 2023
The top malware and ransomware threats for April 2023News New ransomware gangs and malware abound as hackers continue to evolve their tactics
By Connor Jones
-
 How we test security software
How we test security softwareReviews Everything you need to know about our benchmarking process for antivirus products
By IT Pro
-
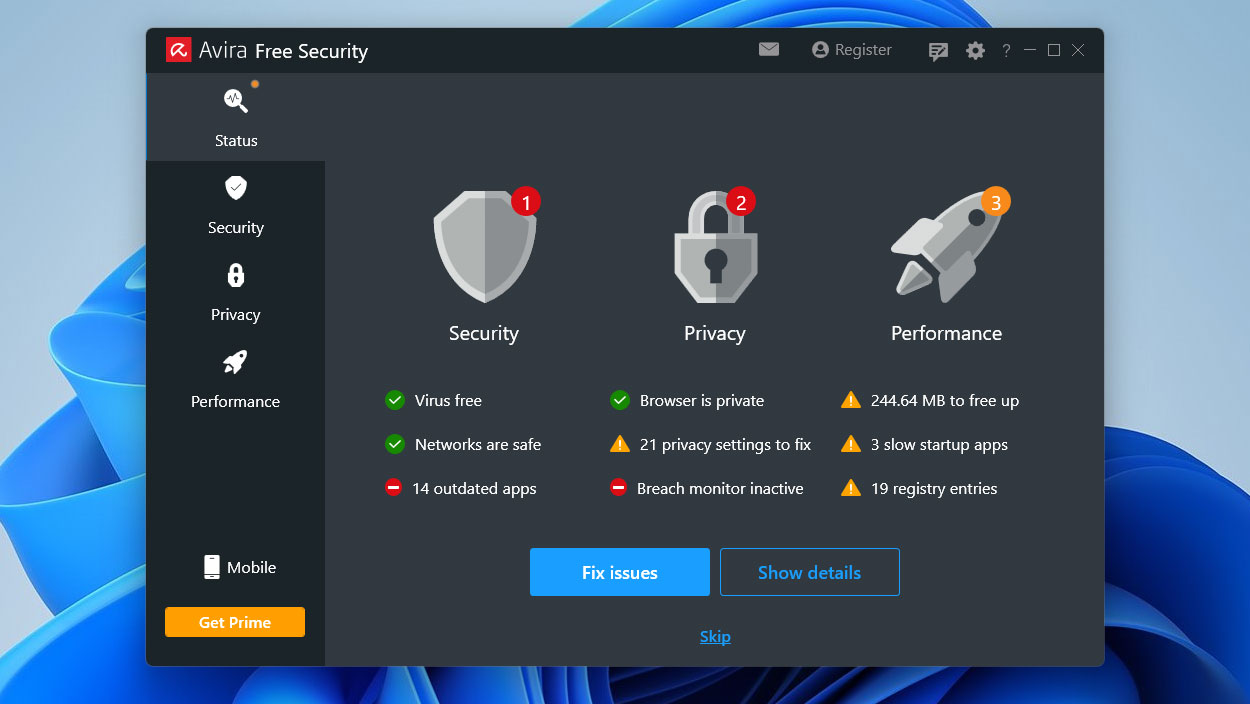 Avira Free Security review: An effective antimalware suite, but heavy on the marketing
Avira Free Security review: An effective antimalware suite, but heavy on the marketingReviews It’s hard to fully appreciate Avira’s malware protection when the packaging feels so manipulative
By Darien Graham-Smith
-
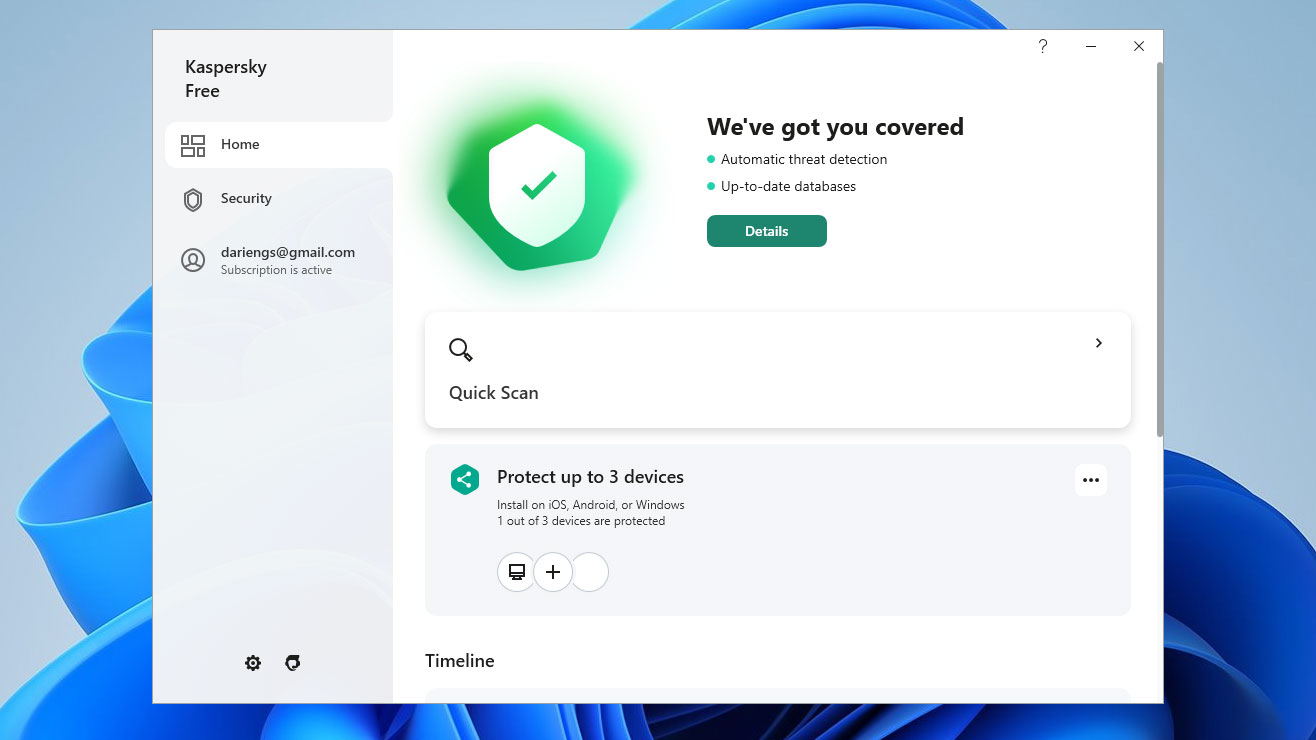 Kaspersky Free review: Effective and lightweight – everything you want from a free antivirus solution
Kaspersky Free review: Effective and lightweight – everything you want from a free antivirus solutionReviews It’ll be a real shame if politics means people missing out on this top-class security tool
By Darien Graham-Smith
-
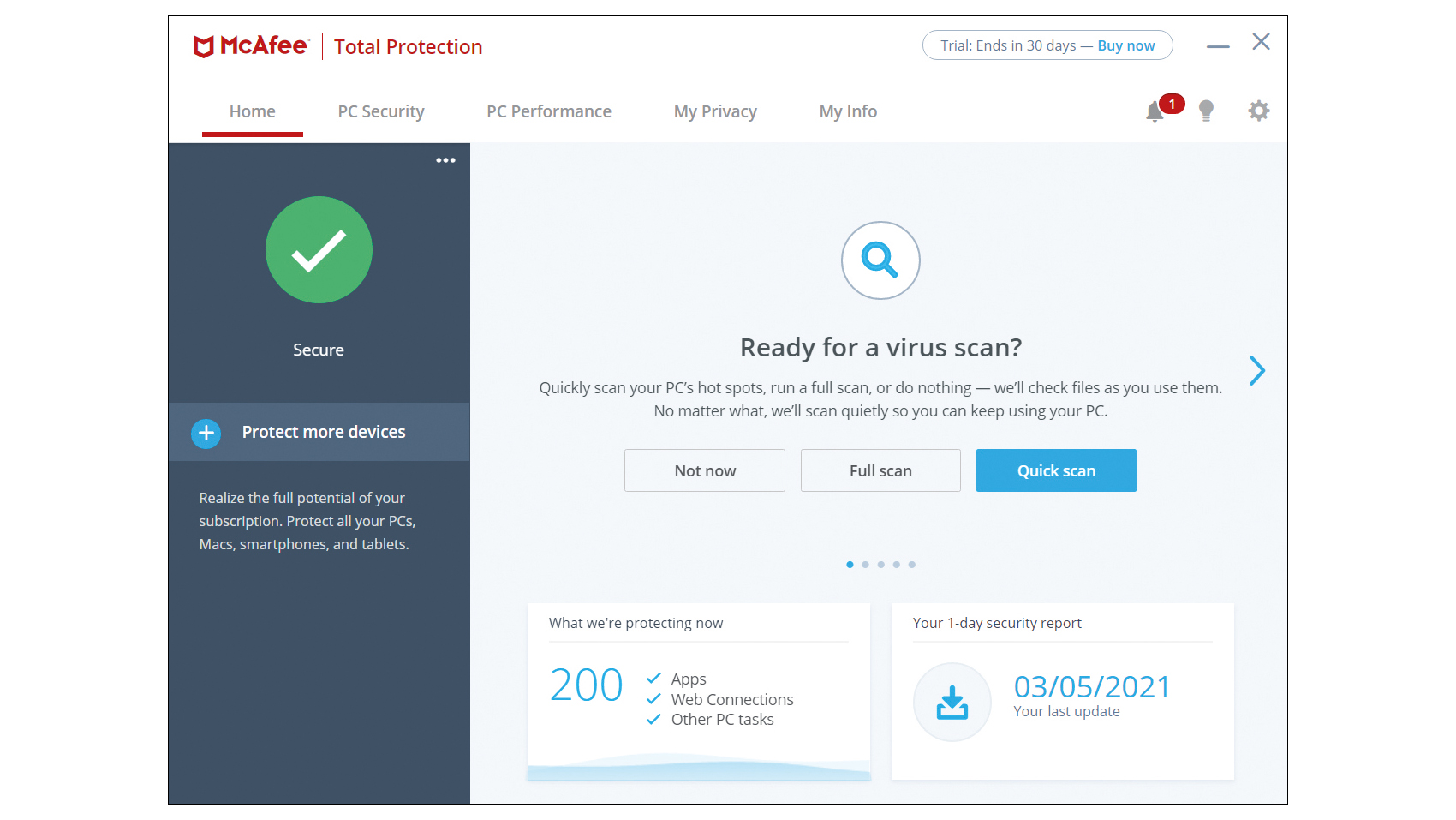 McAfee Total Protection review: Quick, effective and affordable
McAfee Total Protection review: Quick, effective and affordableReviews A solid security choice, with perfect malware protection, a fully functional VPN and more
By ITPro
-
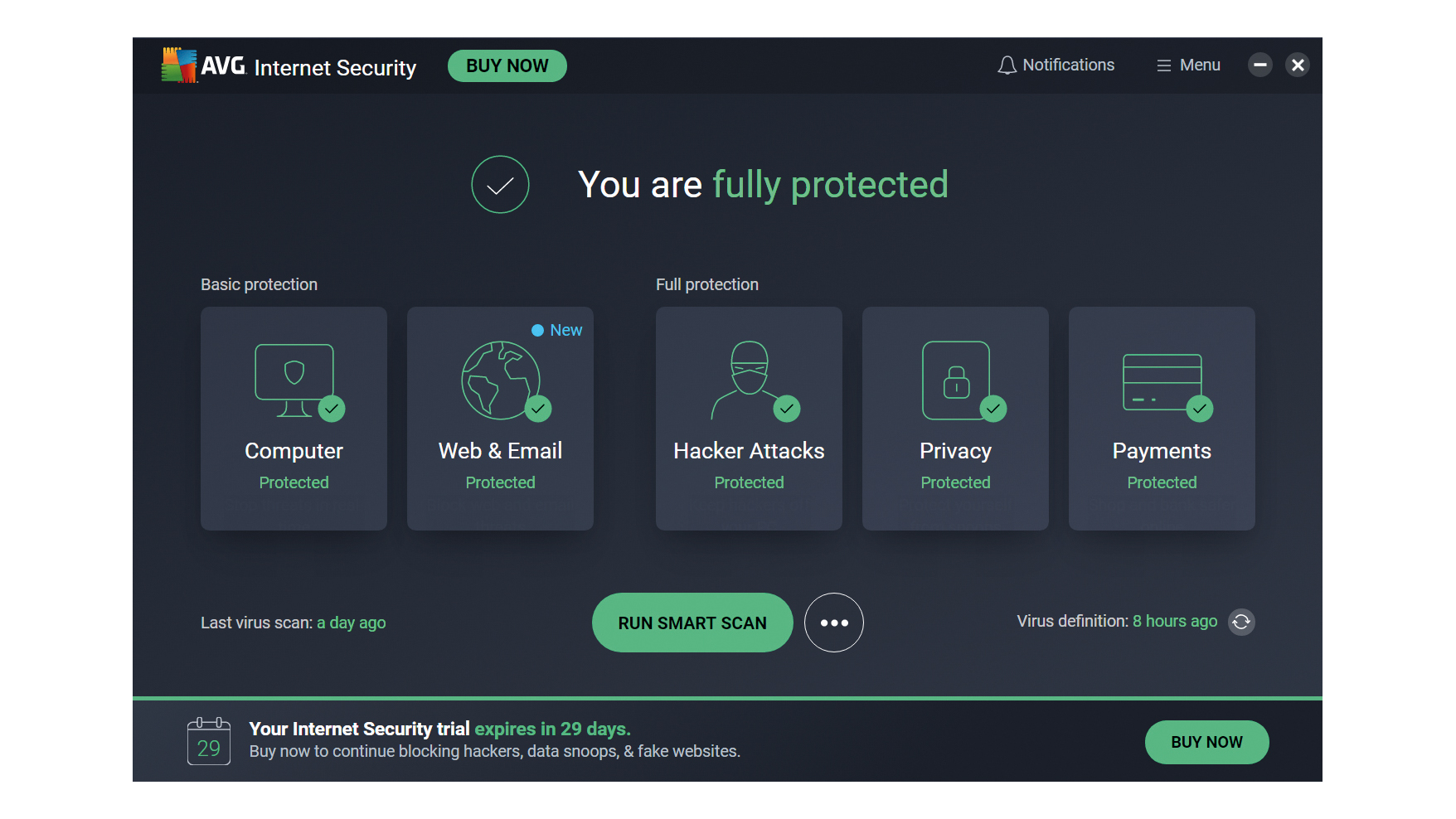 AVG Internet Security review: Money for nothing
AVG Internet Security review: Money for nothingReviews An ostensible upgrade from the free Avast package – but there’s very little here to justify the cost
By Darien Graham-Smith
-
 Avira Antivirus Pro review: Obnoxious and annoying
Avira Antivirus Pro review: Obnoxious and annoyingReviews This antivirus tool does the job, but it’s expensive – and the in-app advertising really sticks in the throat
By Darien Graham-Smith