DeviceLock 7 review
Accidental or deliberate data leakage is now a major security headache for businesses. Dave Mitchell takes a look at DeviceLock 7 to see if it plugs those holes that others leave behind.
DeviceLock provides some of the best controls for ensuring that sensitive data doesn’t get into the wrong hands. The new NetworkLock and ContentLock options are well worth considering as they add extra levels of security for protocols and applications but they are expensive for SMBs. We also think it’s about time DeviceLock simplified management by amalgamating all the different consoles into just one which would make it easier to use.

Network perimeter security is no longer enough to prevent data leakage as the enemy is probably already inside the gates. The number of communications methods and removable storage devices available to your users makes it all too easy to accidentally take sensitive data off premises or steal it.
We've always been impressed with DeviceLock's solution to this problem and this latest version adds stronger access security at the network protocol level. It also has greater content awareness allowing it to apply access policies based on file content as well as file type. This ContentLock feature works by recognising keywords and patterns within file contents.
At its foundation, DeviceLock provides controls for managing access to every conceivable workstation port and removable storage device. The latest iPads and iPhones are recognised so it can control data transfers between these types of devices and manage access to functions such as calendars, contacts and email.
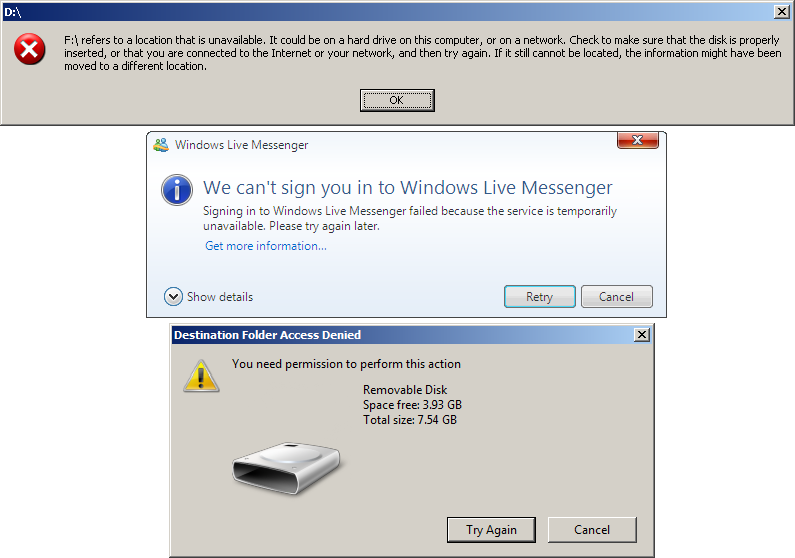
These are some of the messages users will see if they try to access devices or services they do not have permission for.
DeviceLock 7 introduces the optional NetworkLock component which takes access control up to the network protocol level. For SMTP you can control connections to a mail server, the sending of emails and whether attachments are permitted.
HTTP policies determine whether you can post content to web forms, upload files to a web server or whether you are allowed any web browser access at all. For social networking sites you can control basic access, permit users to post comments and messages and allow or deny uploading content.
Installation on a Windows Server 2008 R2 64-bit system was easy enough, although DeviceLock really needs to integrate everything into a single console. At present, you have to juggle three different consoles. One works with the standard MMC console integrating with Active Directory so access policies can be enforced at the user and group level.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 Cleo attack victim list grows as Hertz confirms customer data stolen – and security experts say it won't be the last
Cleo attack victim list grows as Hertz confirms customer data stolen – and security experts say it won't be the lastNews Hertz has confirmed it suffered a data breach as a result of the Cleo zero-day vulnerability in late 2024, with the car rental giant warning that customer data was stolen.
By Ross Kelly Published
-
 Women show more team spirit when it comes to cybersecurity, yet they're still missing out on opportunities
Women show more team spirit when it comes to cybersecurity, yet they're still missing out on opportunitiesNews While they're more likely to believe that responsibility should be shared, women are less likely to get the necessary training
By Emma Woollacott Published
-
 OpenAI wants developers using its new GPT-4.1 models – but how do they compare to Claude and Gemini on coding tasks?
OpenAI wants developers using its new GPT-4.1 models – but how do they compare to Claude and Gemini on coding tasks?News OpenAI says its GPT-4.1 model family offers sizable improvements for coding, but tests show competitors still outperform it in key areas.
By Ross Kelly Published