Websense Triton Security Gateway Anywhere review
Websense's TSGA claims to be the first unified solution for web, mail and data security that doesn’t rely on any third party components. It goes even further by amalgamating on-premises and cloud scanning in the same product, but is it too good to be true? Dave Mitchell finds out in our review.
Mid-sized business and enterprises looking for a single appliance to take care of all their network security needs will find Websense’s TSGA ideal as it combines a remarkable range of web, mail and data security features with excellent performance. Websense’s TruHybrid is compelling with both the on-premises and SaaS cloud services seamlessly integrated into the well designed central management console.

Security policies for web access can be applied to a range of criteria including AD users and groups, IP address ranges and individual machines. Websense provides a remarkable choice of categories where you can block or allow certain keyword searches and file types as well as apply quotas that restrict browsing time.
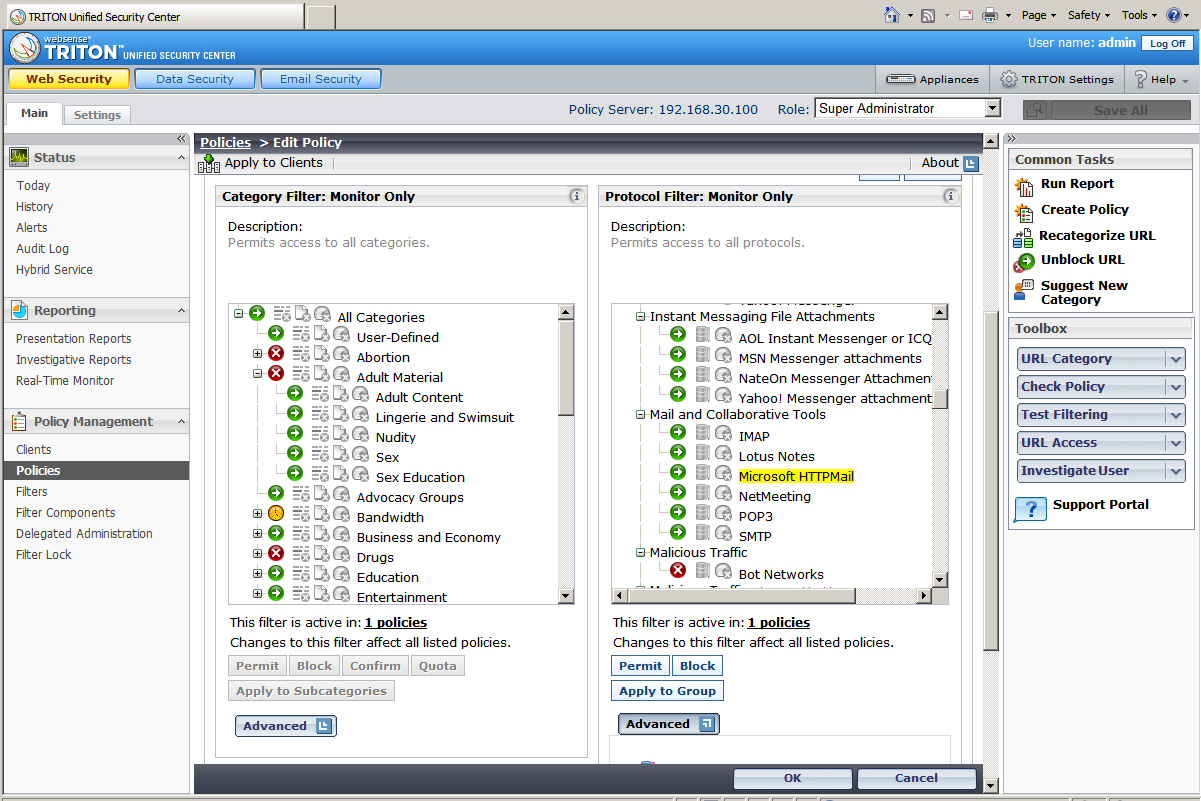
Websense provides comprehensive lists of web categories and protocols which can be combined in the same security policy.
This section also includes a comprehensive range of protocol filters so the same policy can be used to control apps such as IM and P2P, file transfer tools and web mail. There's even a bandwidth optimiser that can be applied to individual web categories and protocols within a policy where they will be blocked if usage goes above a set percentage of bandwidth.
Default policies for inbound and outbound mail are ready to use and messages are subjected to a barrage of tests. TSGA scans the message body, runs heuristics and applies its LexiRule scanner which looks for specific word patterns. It'll also classify any URLs in the message and calculates a message fingerprint which it compares to its spam database.
The TruHybrid portion is easy to configure and for the web component you decide which locations, based on IP addresses and subnets, are to be filtered using the cloud service. Policies created locally can be applied to remote sites and workers and, as TSGA can identify their physical location, it can apply different policies based on whether they are on-site or off-site.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 Cybersecurity experts face 20 years in prison following ransomware campaign
Cybersecurity experts face 20 years in prison following ransomware campaignTwo men used their tech expertise to carry out ALPHV BlackCat ransomware attacks
By Emma Woollacott Published
-
 UK firms aim for growth through AI investment but lack of talent is a concern
UK firms aim for growth through AI investment but lack of talent is a concernTech training and upskilling will be a major focus in 2026
By Emma Woollacott Published
-
 Samsung unveils plan for AI transformation across all devices
Samsung unveils plan for AI transformation across all devicesBoth the DS and DX divisions of the business are profiting from the AI boom
By Jane McCallion Published
