Who should take ownership of your cyber security strategy?
We explore the options of who should be in charge of this increasingly important area


It's no secret that ensuring cyber security resilience is one of the most onerous tasks a modern organisation must tackle in today's world. It's arguably the most important too: With such catastrophic fines such as those dished out under GDPR being issued for security malpractice, businesses can no longer see cyber security as an afterthought.
Unfortunately, even when businesses think they're taking all the necessary steps to secure themselves and the data they house, it sometimes isn't enough to keep the bad guys out. According to the UK government's latest Cyber Security Breaches Survey, 32% of businesses have suffered a data breach or cyber attack in the past 12 months and while this figure is down from previous years it indicates security must still be taken more seriously.
If people's data and the threat of crippling fines weren't enough motivation, the cost of security incidents is rising too. Businesses affected by a cyber incident in 2017 paid out 2,450 on average whereas two years later, this has risen to 4,180.
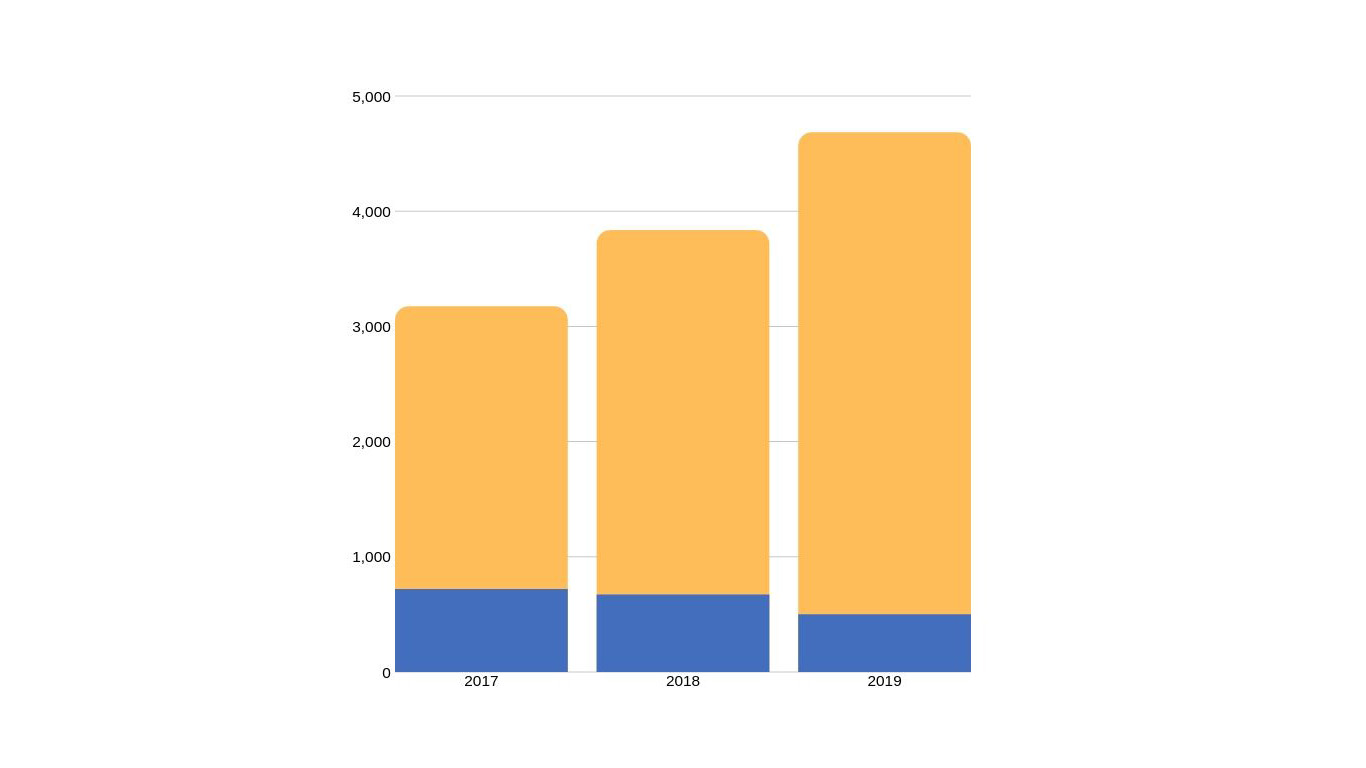
UK data breaches vs financial impact
So, the stakes are high and the pressure is on, but the question of who to turn to when it's time to devise a robust cyber security strategy is one that sometimes goes unanswered in businesses. The task could potentially fall under the remit of a range of people in the organisation the CTO, CSO, CISO, CEO and the IT team could be seen as the first port of call and it's important to nail-down who that should be.
Whether it's checking that your existing strategy is up to scratch or implementing one for the first time, here's who to turn to.
A question of responsibility
You can't start work on a cyber security strategy until you have sorted out leadership and operational responsibilities, and the role of the board. Cyber threats are no longer 'just an IT problem', with a recent survey by the Enterprise Strategy Group showing that 40% of executives and directors want regular security status reports for cyber risk associated with end-to-end business process.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
RELATED RESOURCE

Four cybersecurity essentials that your board of directors wants to know
The insights to help you deliver what they need
FREE DOWNLOAD
The map of responsibilities will depend to some extent on the nature of the organisation including its size, whether it is single or multi-site, and the nature of its technology setup. It won't be enough just to say the chief technology officer (CTO) leads on implementation and the chief executive takes leadership responsibility. The reality is much more nuanced.
Where there is a chief information security officer (CISO) they should take the lead. Kevin Curran, professor of cyber security at Ulster University and a senior member of professional body IEEE, is emphatic about this, telling IT Pro: "That is why they are employed. Of course it is crucial that they have awareness of the business needs, as well as the technical needs of the organisation but they should be the person who has the requisite knowledge to identify the areas of risk and drive the resources to those areas."
Not every organisation has a CISO, however, and in this case it will be important to define a role that fills the gap. This may well be the IT team lead or, where there is a separate data security team, its lead. It's important that the person is senior enough to have real authority to make decisions, get them implemented, and be able to speak on level terms to the board.
Sharing the load
Wherever in the technology team the lead operational responsibility sits, it will be vital to ensure buy-in from other parts of the organisation. Talal Rajab, head of programme cyber at industry body techUK says other teams that will need to get involved include "the communications team to communicate internally and externally as well as other senior leadership personnel."
In the best case every section head and every director level postholder should be involved to some degree. Of course they won't all have technology skills. Their roles will focus on keeping policies and processes practical for their teams, driving awareness and securing buy-in.
If an organisation chooses to share the responsibility of the cyber security strategy, it's also important to have an iron-clad communications strategy to ensure everyone involved is well-informed on the matter and also to make sure action can be taken in the very worst circumstances.
Taking the oft-cited example of Maersk for instance, after the company was hit hard like a sledgehammer to a toothpick by the brutal NotPetya worm in 2017, it was reduced to creative communication strategies. This was a worst-case scenario, but the lesson should still be heeded by even the smallest businesses. In cases where normal communication channels aren't an option, implement a fail-safe strategy so everyone involved in the cyber security of the organisation can give and receive orders, ensuring rapid restoration of systems following a cyber attack.
The role of the board
Cyber security vulnerabilities don't start with IT systems, but originate from leaderships attitudes and priorities.
With a cyber security strategy, leadership has to come right from the top, which is to say the board. As Rajab puts it: "The days of relegating cyber security to the IT department are long gone. In order to instigate meaningful, long term change it needs to be treated as an enterprise risk and that therefore requires the board to take control of the situation."
Ensuring that the board thoroughly understands the threat level can also be pivotal to initially gaining the resources necessary to construct and implement an effective strategy. For their own sake, leadership must be made aware, and business repercussions of attacks demonstrated.
RELATED RESOURCE

Four cybersecurity essentials that your board of directors wants to know
The insights to help you deliver what they need
FREE DOWNLOAD
Rajab adds: "All members of the board should educate themselves on cyber security, as they will ultimately be accountable. All members need to ask for regular updates on their company's cyber posture, agree to investment and ensure processes are in place. If this is all left to one board member, there is a danger that issues might be missed or overlooked. It is about developing a company-wide culture."
For the CISOs, IT and security professionals who deliver reports to the board, it will help to focus on the risk represented by cyber security vulnerabilities and attacks, rather than lengthy technical details. Aligning cyber security risks with the overall business strategy and key assets is a good place to start, as understanding what is most critical to protect makes it much easier to identify coverage gaps.
Ready for the off
But it isn't enough to devote ownership to only boardrooms and IT teams. It is employees on the ground, on the front-line who are most likely to encounter a cyberattack (in whatever form it appears), as simply, lower-level staff outnumber C-levels.
Leadership and IT teams do take responsibility for creating and deploying a strategy, but regular employees must also feel comfortable to contribute. Feedback must be gathered about what types of threat they experience day-to-day, and a strategy can be tailored to suit.
For employees who are unengaged, demonstrate the threat-level and repercussions, and offer incentivised security awareness training.
Clarity about responsibilities for both implementation and leadership should enable implementation of a strong cyber security strategy with buy-in across the organisation. That way it won't be seen as something done 'to' and organisation by the IT team, but something done "for, with and by" the organisation. This approach will help it gain support in both word and deed right from the get-go.
If there's one thing that's certain about a cyber security strategy, it's that without the entire organisation buying-in to form a united front, chances of successfully blocking ever-evolving attacks are limited.

Sandra Vogel is a freelance journalist with decades of experience in long-form and explainer content, research papers, case studies, white papers, blogs, books, and hardware reviews. She has contributed to ZDNet, national newspapers and many of the best known technology web sites.
At ITPro, Sandra has contributed articles on artificial intelligence (AI), measures that can be taken to cope with inflation, the telecoms industry, risk management, and C-suite strategies. In the past, Sandra also contributed handset reviews for ITPro and has written for the brand for more than 13 years in total.
-
 DocuWare CEO Michael Berger on the company’s rapid growth
DocuWare CEO Michael Berger on the company’s rapid growthNews ChannelPro sat down with DocuWare CEO Michael Berger to discuss the company's rapid growth and channel strategy.
By Bobby Hellard Published
-
 Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up sting
Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up stingNews Europol has detained several people believed to be involved in a botnet operation as part of a follow-up to a major takedown last year.
By Emma Woollacott Published
-
 "Thinly spread": Questions raised over UK government’s latest cyber funding scheme
"Thinly spread": Questions raised over UK government’s latest cyber funding schemeThe funding will go towards bolstering cyber skills, though some industry experts have questioned the size of the price tag
By George Fitzmaurice Published
-
 Modern enterprise cybersecurity
Modern enterprise cybersecuritywhitepaper Cultivating resilience with reduced detection and response times
By ITPro Published
-
 IDC InfoBrief: How CIOs can achieve the promised benefits of sustainability
IDC InfoBrief: How CIOs can achieve the promised benefits of sustainabilitywhitepaper CIOs are facing two conflicting strategic imperatives
By ITPro Published
-
 The complete guide to the NIST cybersecurity framework
The complete guide to the NIST cybersecurity frameworkWhitepaper Find out how the NIST Cybersecurity framework is evolving
By ITPro Published
-
 Are you prepared for the next attack? The state of application security in 2024
Are you prepared for the next attack? The state of application security in 2024Webinar Aligning to NIS2 cybersecurity risk-management obligations in the EU
By ITPro Published
-
 The economics of penetration testing for web application security
The economics of penetration testing for web application securitywhitepaper Get the most value from your security solution
By ITPro Published
-
 How to extend zero trust to your cloud workloads
How to extend zero trust to your cloud workloadsWhitepaper Implement zero trust-based security across your entire ecosystem
By ITPro Published
-
 Four requirements for a zero trust branch
Four requirements for a zero trust branchWhitepaper Effectively navigate the complex and ever-changing demands of security and network connectivity
By ITPro Published