BlackBerry Z10 security flaw too fiddly to exploit
BlackBerry claims hackers would need significant access to device and user to exploit BB10 software vulnerability.

A flaw in the BlackBerry Z10 smartphone, which could potentially allow hackers to gain root-level access to the device has been played down by a security expert who deems it too fiddly to exploit.
BlackBerry alerted Z10 users several days ago to the security flaw on its Knowledge Base blog, and explained that Q10 users and people running the latest version of the software should not be affected.
The vulnerability could potentially allow hackers to gain access to resources that are usually reserved for senior management, or to permit applications to carry out unauthorised actions.
However, the blog post said the steps needed to exploit the vulnerability require a high degree of user interaction and physical access to the device.
"Successful exploitation requires not only that a customer enable Blackberry Protect, use the feature to reset the device password, and download a specifically crafted malicious app, but an attacker [would also need to] gain physical access to the device," the blog post explained.
"If all of the requirements are met for exploitation, an attacker could potentially access or modify data on the device," it added.
BlackBerry Protect is an optional feature in BB10 that allows Q10 and Z10 users to remotely track, lock, wipe and display a message on the device by logging into an online portal.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
At the moment, the smartphone maker said it is not aware of any examples where the vulnerability had been exploited.
Given the number of steps and proximity to the device hackers would need to have, Michael Sutton, vice president of security research at vendor Zscaler, said exploitation is unlikely.
"BlackBerry has historically had a strong reputation for building a secure operating system, making it a popular choice for security conscious enterprises, even as Apple and Google have dramatically eaten away at their overall market share," said Sutton.
"Fortunately, the vulnerability affects a relatively narrow scope of devices and would require a fairly specific chain of events to achieve successful exploitation."
-
 The Race Is On for Higher Ed to Adapt: Equity in Hyflex Learning
The Race Is On for Higher Ed to Adapt: Equity in Hyflex LearningBy ITPro
-
 Google faces 'first of its kind' class action for search ads overcharging in UK
Google faces 'first of its kind' class action for search ads overcharging in UKNews Google faces a "first of its kind" £5 billion lawsuit in the UK over accusations it has a monopoly in digital advertising that allows it to overcharge customers.
By Nicole Kobie
-
 Blackberry revenue falls by 4% as cyber security division takes hit
Blackberry revenue falls by 4% as cyber security division takes hitNews Despite this, the company’s Internet of Things (IoT) division increased its revenue by 28% as it attracted new customers from the automotive sector
By Zach Marzouk
-
 BlackBerry revival is officially dead as OnwardMobility shuts down
BlackBerry revival is officially dead as OnwardMobility shuts downNews The Texas-based startup is mysteriously shutting down and taking its ultra-secure 5G BlackBerry with it
By Bobby Hellard
-
 BlackBerry and AWS are developing a standardized vehicle data platform
BlackBerry and AWS are developing a standardized vehicle data platformNews Platform will give automakers a standardized way to process data from vehicle sensors in the cloud
By Rene Millman
-
 BlackBerry thwarts mobile phishing attacks with new AI tools
BlackBerry thwarts mobile phishing attacks with new AI toolsNews The company's Protect Mobile platform alerts users to potential malware before a link is clicked
By Tyler Omoth
-
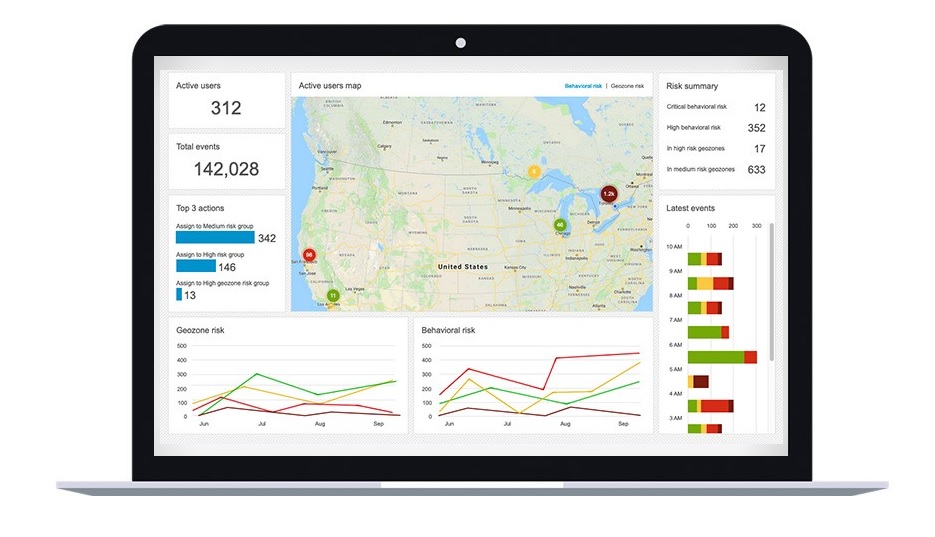 BlackBerry Persona Desktop delivers zero-trust security at the endpoint
BlackBerry Persona Desktop delivers zero-trust security at the endpointNews New security solution learns user behavior and can take action if there’s an abnormality
By Justin Cupler
-
 A 5G BlackBerry phone with physical keyboard is coming in 2021
A 5G BlackBerry phone with physical keyboard is coming in 2021News The business phone to be resurrected with OnwardMobility and FIH Mobile planning a security-savvy enterprise handset
By Bobby Hellard
-
 The business smartphone is dead
The business smartphone is deadIn-depth BlackBerry’s demise signals the end of the business-first handset
By Carly Page
-
 BlackBerry Key2 review: The best physical keyboard no one asked for
BlackBerry Key2 review: The best physical keyboard no one asked forReviews Despite the improvements, the flaws of BlackBerry’s Key range are still front and centre
By Bobby Hellard