Welcome to CPX 2024, live from Vienna. We're on the ground at Check Point's annual flagship European event to bring you all the latest news and updates from the morning keynotes.
In today's session, we'll hear from a host of senior Check Point figures including CEO and founder Gil Shwed, Eyal Manor, VP of product management, and Check Point president Rupal Hollenbeck.
Guten Morgen from Vienna! The Messe Wien exhibition center is filling up in preparation for the opening keynote.

We are just waiting to be let into the keynote theater as the excitement builds.
The doors are open and people are flooding into the theatre to snap up the good seats.

While we wait, why not check out some of ITPro's previous coverage of the security specialist's recent activity:
– Check Point targets partner growth with MSSP program revamp
– Check Point acquires Perimeter 81 in push to meet SASE demand
– Check Point Software snaps up former TD Synnex boss to lead channel efforts
A tannoy announces the keynote will begin shortly as the theater as Beyonce blares over the PA system.
First up we are expecting Check Point's president Rupal Hollenbeck to talk with Jason Teoh, CIO at University Hospital Southampton about the changing role of the security executive.
The lights are dipped, and the presentation begins with some very dramatic video footage talking about Check Point's role in counteracting threats and mitigating risks where "every second counts".
Of course, AI is mentioned, as the tag line "security in action" rolls onto screen.
First out is the MC for the morning, VP of technical sales and customer success, Avi Renbaum, who is welcoming all attendees and walking through through some general housekeeping for the conference.

And Renbaum is quick to introduce Rupal Hollenbeck, who starts by outlining the values of Check Point Experience in prioritizing customer experience, and so who better to talk to than a customer?
Up comes HPE's SVP and chief security officer Bobby Ford to talk about how the job of the security exec has changed over the previous year.
Hollenbeck's first question for Ford is how HPE is leveraging generative AI in their approach to security.
Ford explains how HPE provides products and infrastructure to deploy LLMs, as well as how research into how their business units and functions can use AI effectively.
Ford explains in terms of security they are focusing on these key aspects of how AI will change security strategy within businesses.
– Speeding processes within enterprises
– Equipping cyber professionals to leverage AI more effectively
– Leveraging AI for policy and management
Now the pair are discussing the sprawling attack surface in 2024, and what HPE is doing to address this.
Ford explains that in the growth of devices connected to the internet has exploded, as has the amount of data.
To secure this, businesses need to identify what is critical in their operations and protect these areas first.
Next is an elastic approach to security, where a companies cyber posture expands and contracts according to where the threats are coming from
Now we are talking about skills gaps. Ford explains he doesn't see it as a talent shortage but an experience shortage, and so his approach is looking within the organization to build skills within an enterprise.
Ford says he's focusing on being 'talent makers' rather than 'talent takers'.
Hollenbeck comes back to the role of the security officer. Asking how this role has shifted from being operational and techincal to a more strategic focus.
Ford refers to the regulatory landscape that is tightening for CISOs all over the world. He describes it as quite 'scary' as a CISO, who now has to wear many different hats to ensure their organisation has a mature approach to security.
Ford leaves with a his primary focus at HPE, providing elastic and intelligent solutions that grow with the business without requiring a constant back and forth between vendor and customer.

And with that Bobby Ford takes his leave to a round of applause, next up Hollenbeck welcomes Check Point founder and CEO Gil Shwed.
Shwed will be outlining what Check Point want to do in 2024, but first he touches on some of the progress the company has made in recent years.

Shwed now says he wants to introduce what Check Point is going to launch this year to bolster enterprise security across industries.
He rolls some video footage with Check Point's AI assistant Amy explaining that 2024 will be a turning point for cyber security, where a AI-powered and cloud-delivered platform is foundational.

Shwed says last year we saw an explosion in what Check Point describe as Gen V ransomware attacks that have a sophisticated understanding of the target network, using elevated detection evasion, malware injection, and multiple layers of extortion.

Shwed argues business cannot just treat these attacks as inevitable and focus on mitigation, they need to actually try and stop the attacks at source.
To do this companies will need a unified security platform that can provide protection across endpoints, again reaffirming Check Point's ambition to provide an ai-powered, cloud-delivered security platform that importantly emphasizes collaboration as integral to dealing with elevated threat levels.
Shwed says Check Point were able to prevent over 3 billion attacks with the implementation of AI tools in the backbone of their security system.
To complement this, Check Point will also be bringing AI to the front end of their security platform, which will give cyber professionals access to AI across their suite.
Shwed shows a demo of Check Point's AI Copilot helping security admins with documentation, logs, configuration, policy, and troubleshooting.
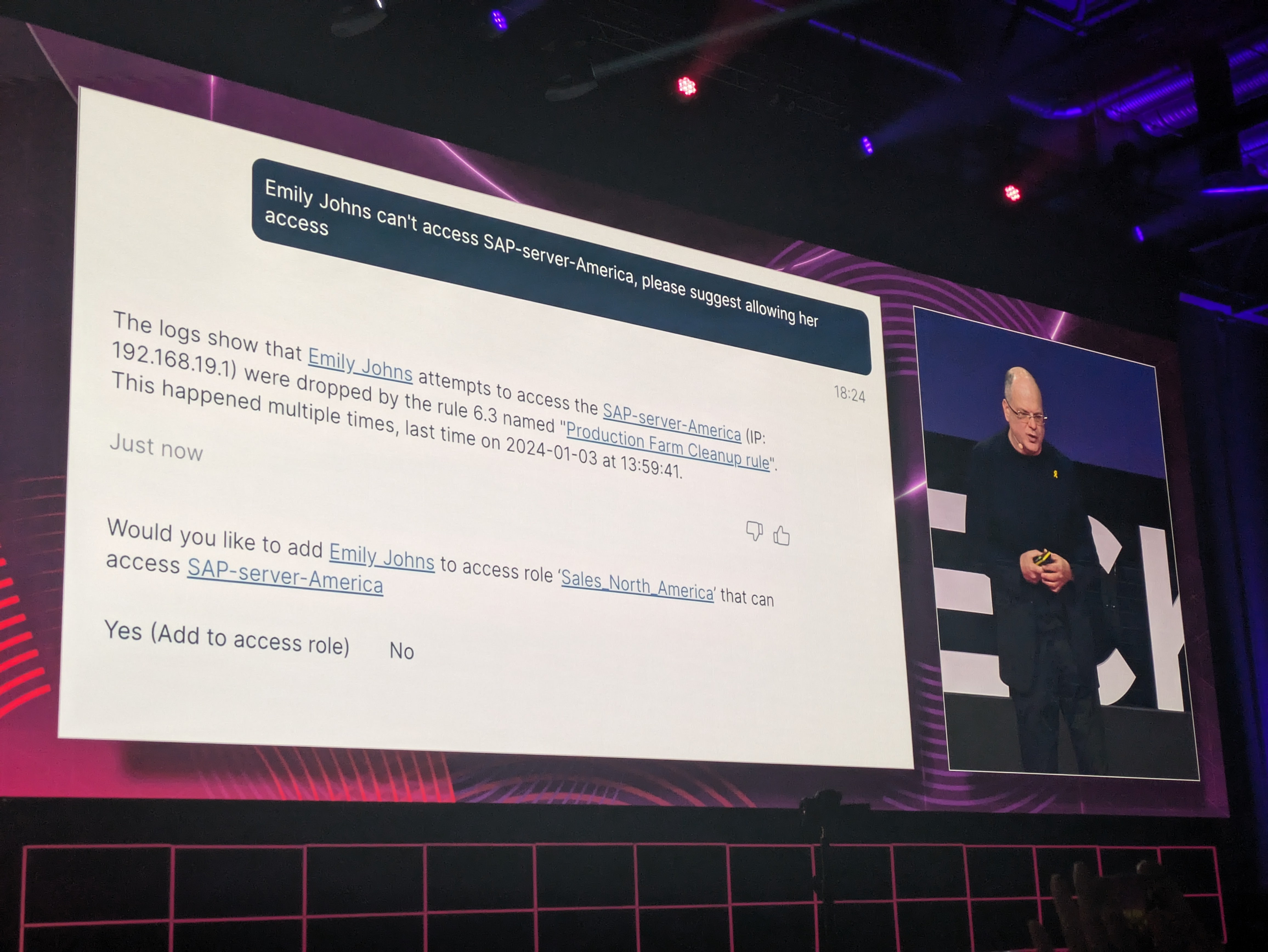
The AI Copilot is available today, and businesses will be able to use it on-premises as of next quarter.
Next up is the cloud-delivered aspect of this solution. Shwed explains this is doesn't mean sending all of your data to one location in the cloud. One entity having sole access to your data is not security according to Shwed.
The answer, according to Shwed, is a hybrid architecture, across which Check Point will bring their security gateways.
Shwed says 80% of Check Point's security gatweays are available across the platform, as well as 100% of their email endpoint mobile cloud workloads.
Today Check Point are launching Quantum Force to maximize the power of their cloud and AI offerings.
The offering will come in three different tiers according to the size of the customer, including the series 900, 1900, and 2900 which offers the best prevention rate in the industry, according to Schwed, and are available today.

Shwed asks, what makes Check Point's solutions a 'true platform' which he says is collaboration.
"The only way to take advantage of all the industry in the industry is to make all of these technologies work together for you".
Tool sprawl is a growing problem as new threats bring a slew of new products to dealt with them.
Shwed says Check Point are working to solve this problem by ensuring their security products can work together.
Part of making security collaborative is Check Point's Playblocks system that provides automatic mitigation and response for both Check Point and third party products.
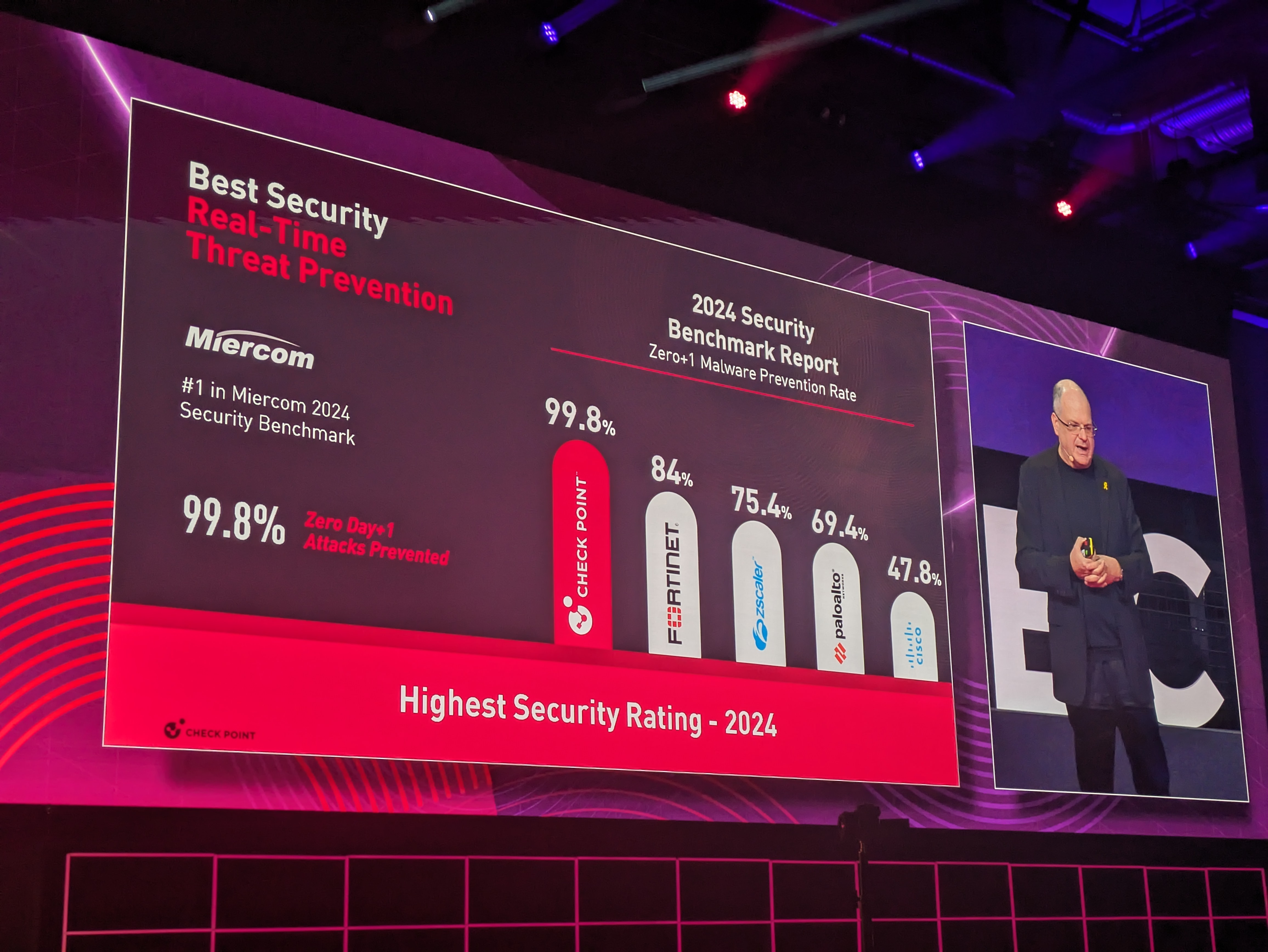
Now we are getting a look at Check Point's 2024 Security Benchmark Report, and Shwed says the numbers speak for themselves.
Shwed is now setting the stage to introduce Nataly Kramer, Check Point's chief product officer, who will talk a little more about the specific products that are making this unified platform a possibility.
Nataly says she wants to talk about what makes Check Point's Infinity Platform comprehensive.
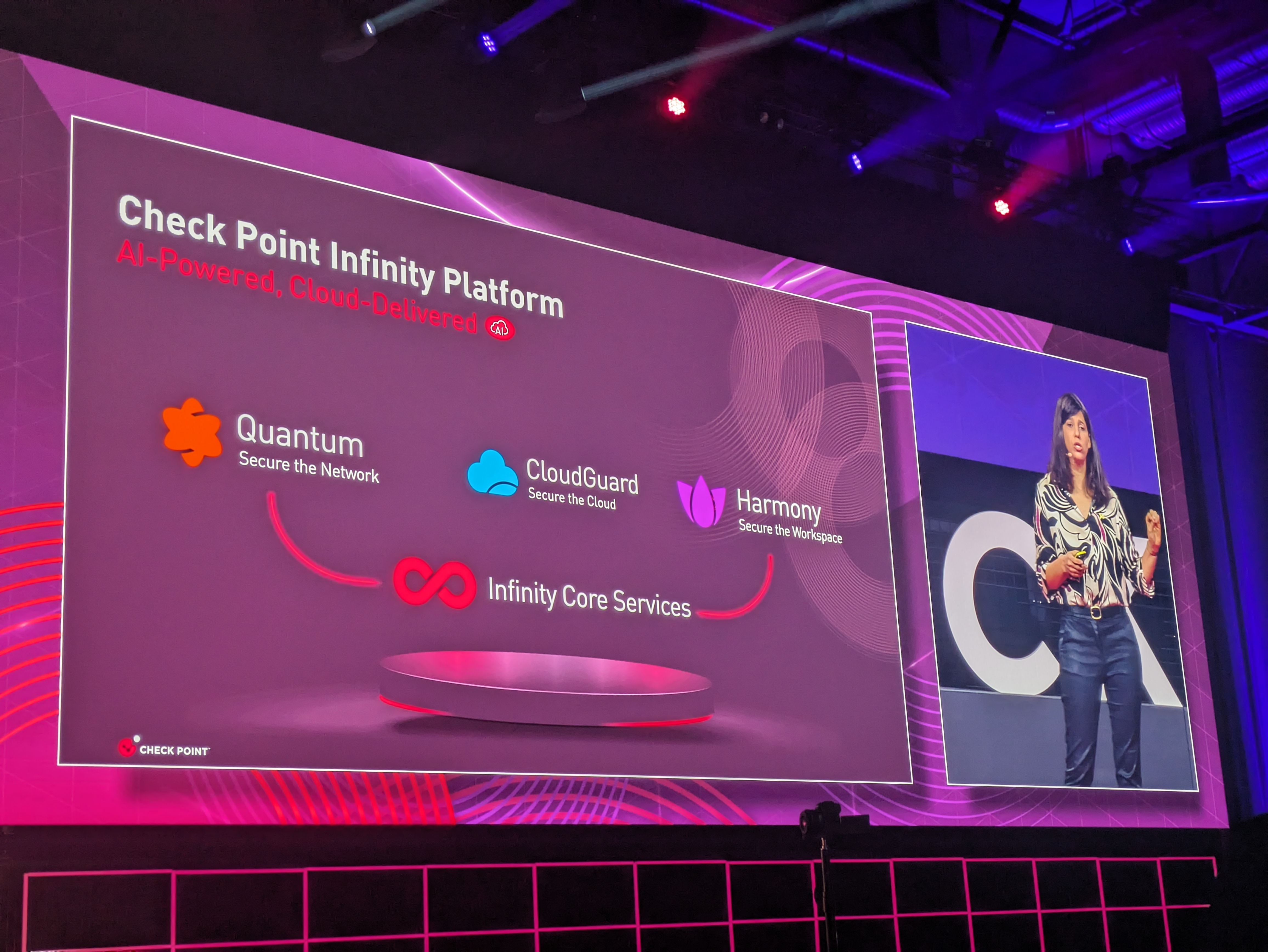
First up is Quantum which takes care of an enterprise's mesh network. Kramer says the Quantum solution's three strengths lie in strong threat prevention performance, simplicity for end users, and superior performance.
Kramer outlines Check Point's decision to enhance their Quantum offering with the AI-powered Quantum Force, announced today, will boost performance for enterprises.
Now Kramer is discussing Harmony, Check Point's endpoint protection solution, with a specific focus on protecting the workspace in an era of hybrid work.
Kramer explains when speaking to customers, user experience was the most important factor, where compromised UX hurts the productivity of employees and businesses.
Not just productivity, employees frustrated by their user experience will do everything they can to bypass security layers.
Check Point are baking this into their SASE approach by bringing security as close as possible to the device, which will provide double the internet browsing speed than competing solutions, according to Kramer.
Kramer is now discussing Check Point's CloudGuard cloud security solution, trying to fix the endless endless headaches businesses have migrating to and securing their cloud infrastructure.
CloudGuard will automatically use traffic data to tailor its WAF solution, requiring no signatures and speeding up business operations that is able to learn what is normal and abnormal traffic.
Network security is another important piece of this puzzle, where Check Point is focussed on helping businesses manage their cloud and on-prem network security solutions.
Now Kramer introduces what she describes as Check Point's X-factor: the Infinity Core Services that provides collaborative threat prevention, unified management, and bringing AI everywhere.
Check Point's approach to collaborative threat prevention will bring real-time shared intelligence, the Playblocks system that offers automatic response and remediation platform across Check Point and third party vendors, and XPR to detect and stop multi-vector attacks.
Kramer concludes by welcoming Eyal Manor Eyal Manor, VP of Product Management to walk through some of Check Point's announcements.

This includes implementing AI to work against brand spoofing, the local brands threat actors use in social engineering attacks to steal credentials.
Manor says more than 560,000 account take-over attempts were prevented in just one month at the end of 2023.
Manor walks through how Playblocks is able to talk to security products across a enterprises IT estate.
Businesses can connect their management environment to the Playblocks system, which see when a particular attack has been blocked and inform admins and describe the attacker and provide their IP address (which is blocked automatically).
This system works without the need to add new security policies, helping save admins time when trying to tailor specific access policies to protect against a myriad attack vectors.
Manor is now talking about Check Point's AI Copilot and the new security features it can provide cyber professionals.
Admins can ask the Copilot 'have there been any attempts to attack the network?'
The Copilot is able to check the logs, and provide a detailed response, while also predicting what the admin will want to do next, such as notifying the employee about new CVEs in the future.
Manor is now going back over some of the new networking security features as part of their Quantum ecosystem. For example he shows off R82, a new feature set that provides new capabilities including TLS inspection and more.
Another element Manor wants to cover is Quantum Spark, its business firewall offering. Today Check Point are announcing new features to Quantum Spark including SD-WAN implementation, as well as expanding Quantum spark to provide solutions for smaller business of up to 1000 employees.
Spark is getting two new appliances, meaning Check Point have announced 12 new networking appliances today!
Now Eyal is bringing Amit Bareket, VP, Security Service Edge, on stage to talk about the shifting paradigms in SASE and cloud security.
Bareket was the founder of Perimeter 81, a dedicated SASE security solution acquired in August 2023 to help Check Point meet the booming demand for access solutions.
Bareket says Perimeter 81 entered a very crowded market of secure access services, but his platform was attract over 3,500 cutomers by focussing on providing robust threat prevention as well as a seamless experience for end users.
Strong threat prevention capabilities are common among SASE products according to Bareket, but the primary factor that goes into selecting a SASE solution are user experience.

Next up, Manor wants to talk about Harmony SaaS, which looks to secure the SaaS ecosystem for enterprises.
A product demo shows how admins can view all of the SaaS services in use in an organization.
As mentioned previously, tool sprawl in the security space is a growing concern and top of mind for CISOs in 2024, and Harmony SaaS is Check Point's answer to a ever complexifying IT estate.
In addition to visibility, the system can inform admins about SaaS services that have over permissive access.
Threat prevention is also baked into the Harmony SaaS management service, which can immediately block applications too.
Harmony SaaS is available today.
CloudGuard is the next in this quick fire product round up. Manor explains one of the challenges with WAF, where false-positive signatures are a common sticking point.
CloudGuard can now offer signature-less WAF-as-a-service which will streamline protecting web applications.
A video demo shows how the CloudGuard platform uses AI to bolster an organization's understanding of security incidents, and offers a new reporting module to ensure security professionals can quickly disclose breaches and vulnerabilities.
Shwed is back on stage to give a brief summary of what we have just seen, the throughline of this keynote has been presenting Check Point 2024 vision as 'the platform company'.
Each speaker has emphasized how this platform is AI-powered and cloud-delivered, with the special sauce being collaboration, key to delivering a holistic approach to security.
Shwed brings back Avi Rembaum who is going to recognize some of Check Point's customers for some of the work they have done over the course of 2023.
That wraps things up for the first half of this keynote, attendees file out to get refreshments.
We'll be back shortly to bring you live coverage of the second half!
The keynote is expected to get back underway at 11.15 CET. Until then, here's a shot of the lobby area bustling with attendees as they rush to get their coffee before the show goes on.

In the second half of the keynote we will be hearing from VP of Research Maya Horowitz on the topic 'Hacking Like da Vinci', as well as a continuation of the discussion on the shifting paradigms of SASE and cloud security.
The session will conclude with a customer case study looking into an organization's journey toward securing the cloud systems that underpin their operations.
Stay tuned!
We are being transported back to the renaissance with some baroque music and ornate set design.
Maya Horowitz is on stage and states she wants to try and better understand the threat landscape through the art and science of the renaissance genius.

Horowitz says the two major ongoing conflicts in the world have seen increased use of cyber warfare tactics, where the motivation for cyber crime is not for profit but strategic purposes.
As such their tactics differ, data wiping tools are used to attack critical national infrastructure organizations, as opposed to profit seeking extortion attempts.
Horowitz moves on to Roman architect Vitruvius. He defined three key qualities in architecture strength, utility, and beauty.
Tying this into cyber security, Horowitz explains how da Vinci used the Vitruvius' detailed study of the human form to inform his art and compares this to how threat actors are refining their phishing emails, making them identical to authentic messages sent to users.
This is not just limited to phishing emails, Horowitz warns, mobile applications such as those for mobile banking, paying tolls, and transportation apps, to steal credentials.
Next on this rather long analogy Horowitz uses da Vinci's mechanical lion to introduce the resurgence of hardware in cyber attacks, .
The return of the USB stick as an attack method, Check Point detected three different threat actors using usb drives as their main infection vector during 2023.
Horowitz details the story of Chinese hacking collective Camera Dragon. Where a Biritsh doctor visiting a conference in Asia used a usb stick to deliver a presentation.
On his return to the UK this usb was used to inject malware onto the network of a British hospital.
And with that, Horowitz wraps up our brief journey into the past, and on comes chief strategy officer at Check Point Itai Greenberg.
Greenberg wants to continue the conversation around the shifting paradigms in SASE and cloud security.
Greenberg begins by looking back at his time working at Microsoft looking at demand for various designs of mobile phones by customers.
He details how in 2006, one year before the introduction of the iPhone, there was little demand for a touch screen design among customers, favoring the legacy t9 form factor.

Greenberg says his point is that sometimes products need to think differently about what customers need, in contrast to what they want.
Greenberg explains customers have a littany of security risks within their cloud assets, and once inside, hackers target these risks to cause the most damage.
The agility and dynamism of the cloud has created many openings for threat actors, Greenberg adds, claiming CISOs need to regain control of security of their enterprises, adding prevention to an organization's cloud platform.
How can we address those risks? Greenberg asks, first up is a WAF system to protect the organization's front door.
Greenberg argues that a particular type of WAF is required however, one that provides preemptive security using AI and integration across products and networks.
Up until this point, Check Point's WAF worked as a plugin, now it is offering WAF-as-a-service, also introducing API discovery to help admins understand which APIs their application is using and what kind of API should be used and how they should be accessed securely.
Greenberg also announces cloud native WAN services that work with the major public cloud providers, again emphasising the importance of a seamless and unified approach to maximize simplicity for customers.

Check Points CNAPP will be powered by the companies well renowned threat intelligence, and as such will reflect the latest attack vectors and vulnerabilities being used to target organizations' cloud systems across the world.
Greenberg has now handed things over to Lior Goldgraber, head of cloud security EMEA at Check Point who is speaking with Andreas Janda, IT architecture expert at eneterprise application specialists SAP.
Janda explains SAP's main strategy was to go and implement a cloud first strategy with their products to help provide enterprises easily transition on-prem SAP workloads into a managed SAP cloud service.
The executive data that goes into these applications, referred to as the 'crown jewels' by Janda are the most valuable and critical data that drives their business.
As such Janda wants to lift-and-shift the attached data into a managed private cloud, underpinned by Check Point's cloud security platform.
Greenberg is back on stage to discuss how Check Point is adding prevention to their CNAPP approach, which he hopes will allow customers to forget about attacks like Log4j Shell and MOVEit.
The shift to cloud and remote work made the network too complex to manage from a security standpoint, between the remote user, offices, internet, cloud and the data center.
In 2022, Greenberg says the world moved to cloud SASE to secure these assets, but customers encountered issues around internet speed, privacy concerns, and exorbitant cloud costs.
Greenberg says Check Point wanted to rethink how it could rethink cloud SASE to address these topics. On comes Amit Bareket to talk further about how Check Point's hybrid SASE can solve these issues.
Bareket describes how Check Point were able to provide two times faster internet connectivity for their hybrud cloud SASE services, outstripping its cloud-only competitors.
In addition, it will bring other features including full mesh connectivity, enabling the hybrid SASE solution to sit on top of any organization's network infrastructure.
Take a look at the full breakdown of the new features provided by Check Point's hybrid cloud SASE solution below.

Bareket invites Gil Friedrich, VP Email Security, to the stage who says he wants to talk about another shifting paradigm, this time in relation to email.
As email moved to the cloud, with Microsoft365 or Google Workspace, organizations needed a better way to secure these systems.
Moving email to the cloud is important as it allows Check Point to bring their cloud security solutions to email, according to Friedrich.
Integral to this was Check Point's first API-based email security solution, which was launched in 2016. Friedrich outlines how Microsoft's system missed 19% of email security threats, representing 570,000 attacks.

"Microsoft did their best, and we're are focused on those attacks Microsoft missed", Friedrich explains.
Part of the success of Check Point's approach to email security is anticipating this shift toward the cloud, rather than reacting to this movement.
Friedrich concludes by summarizing the three paradigm shifts Check Point have observed pertaining to security in relation to the growth of hybrid cloud approach to enterprise IT solutions.
First up is securing the cloud element of this IT estate, second is integrating SASE across the devices and services, and third is rethinking email security as it moves to the cloud with inline protections that anticipate the threats.
That brings Avi Renbaum back out on stage to bring the keynote to a close.

The auditorium empties at a startling pace as the attendees make their way out.
Thank you for following ITPro's live coverage of the opening keynote of Check Point Experience 2024 here from Vienna! Here's a quick summary of announcements we saw.
– General availability of Check Point's Infinity AI Copilot aimed at helping security professionals speed up their workflow
– Quantum Force networking solution launched with 10 new network security gateways for enterprises of all sizes
