Hyvää huomenta! It’s another beautiful day here in Finland and welcome to ITPro's live coverage of WithSecure SPHERE24.
We have another busy agenda to look forward to, including a session on the future of AI with Dr. Kate Darling from the MIT Media Lab, and a panel session on navigating the world of mental health in the cyber security space.

Also on the slate today is a presentation on exposure management from Erik Nost, senior analyst at Forrester, who will be discussing how businesses can build out a more proactive approach to their security posture, actively managing the risks they are exposed and boosting their cyber resilience.
While we're waiting for the opening session to begin, check out our conference preview coverage, detailing all the company's recent goings on and its drive to target mid-market customers.
• WithSecure’s generative AI focus could be the key to its mid-market push
We are almost ready to get started with day one's opening keynote. CEO Antti Koskela is set to kick things off in Helsinki at 1pm EEST.
We are inside the Kaapelitehdas, or Cable Factory in Helsinki, which got its start producing marine cables and is also a former home of Finnish tech giant Nokia. People are starting to take their seats ready for the keynote and a buzz is starting to generate inside the venue.

The crowd is still fairly sparse at the moment, but with only 15 minutes to go before the opening address from Koskela, we can expect it to fill up fast!

The crowds are beginning to shift into the arena with an animated SPHERE logo jumping around in the background, sporting the conference’s rather befuddling ‘co-security unconference’ tagline.

Here we go! The lights have dimmed and here comes Antti Koskela, the Interim CEO at WithSecure.
Antti Koskela greets the crowd and outlines his hope this event can buck the trend of traditional cyber security conferences, which at least gives some context to the aforementioned tagline.

Koskela gets stuck in immediately introducing WithSecure's navigating strategy of targeting mid-sized businesses. He warns the crowd that cyber criminals do not discriminate along the lines of size or revenue - simply because they don't need to - with their attacks proving more lucrative each day.
WithSecure has been clear about its strategy to target the midmarket as the cornerstone of their business moving forward. It sees an opportunity in providing these mid-sized businesses with the solutions and expertise required to keep them secure in an increasingly hostile threat landscape.
Koskela now touches on their cosecurity approach, something he believes is the answer to raising digital confidence in the mid-sized market. Companies need to close the gap towards minimum effective security, combining resilience, trust & compliance, and efficiency.
WithSecure love to throw around their favorite buzzword: co-security at their Sphere conference, since it was introduced into the company lexicon in 2022, but it has remained fairly nebulous since then. Hopefully we get some more clarification on what this means today.
Koksela is now announcing three new products solely for the needs of the midmarket. He stresses the importance of including a proactive approach to cyber resilience with its services.
These new products are WithSecure's exposure management service built to boost resilience, its co-security services for trust and compliance, as well as its new GenAI experience - Lunimen.
Luminem is WithSecure's new generative AI capability based on a Large Language Models (LLMs), and is natively embedded into its cloud security platform WithSecurity Elements Cloud.
The company refers to it as an experience as it wants to emphasize that this isn't just another chatbot or security copilot, stressing the tool is embedded into the Elements platform.
The aim of Luminem is to boost situational awareness through natural language explanations of security events, with a wide-scope of context detections.
Three new products for the Elements cloud security platform
WithSecure has stressed it didn't want to simply jump into the generative AI gold rush, and layer generative AI capabilities on top of its services. Koskela explains that simply just adds unwanted complexity to the security stack as well as exposing the company to unnecessary risks via hallucinations or prompt engineering.
The key product differentiator is the fact that Luminem will lock down the types of prompts users can input, generating them based on context data, which should - in theory - make the tool impossible to jailbreak using refined prompts.
That’s it from Koskela, who gives way to a man who is theatrically wheeled onto the stage using a dolly. He introduces himself as Marcus John Henry Brown who will be hosting the event, but almost as soon as he is on, he introduces our next speaker, Anu Bradford, professor at the Columbia Law School.
Bradford will be talking about the geopolitical considerations affecting cyber security around the world. Bradford notes the diverging approaches to cyber security across the globe, with different regulatory styles bringing about different approaches.
Bradford details that China operates on a restrictive model, whereas the US runs on a permissive model around regulating new technologies. Bradford explains that what separates Europe is the fact that it exports regulation around the world. She adds Europe regulates at a faster rate than it innovates on new technologies.
Bradford talks about the horizontal battles between regions around their digital approach. She explains how American companies are abusing their dominance in the market to edge out European businesses. Europe is starting to push back and exert their regulatory powers, however, which has led to American businesses arguing the EU is overreaching with their regulatory approach.

Bradford makes some predictions that the American market-driven model is losing. There is a sense that the digital economy cannot be governed by tech companies themselves, saying the era defined by this style of governance is over, with governments getting behind the European rights-driven model around privacy.
But she raises three concerns about the European model here, first is that there is general admiration of the benefits of the model, but hesitation around whether it will foster innovation in the region.
She says people in Europe are very quick to name the GDPR as a product of Europe, but also that they struggle when asked to name an innovative tech company from the region.
Bradford sets out four reasons why the technology gap exists between the US and Europe. First is that there is no single market for digital companies and so they cannot scale as quickly as their American counterparts.Second is funding, it is much harder for European companies to secure funding frequently having to turn to US venture capital instead of local investors.
Third is the European bankruptcy laws, you need to let enterprises take risks, fail, and help them recover and try again, Bradford argues. She notes Europe has some of the most punitive bankruptcy laws in the world, whereas the US is far more permissive around entrepreneurship, which she concedes can go too far in some instances.
Finally, and the most important according to Bradford, is the skills shortage. The US has done a much better job of attracting the top tech talent around the world compared to Europe. Over 50% of startups in the US have an immigrant founder, Bradford names Bill Gates, Jeff Bezos, Elon Musk, and Sergey Brinn as examples of those from immigrant background going on to produce huge value for the digital economy.
The next challenge for Europe is competition from China. Bradford offers two reasons why it is hard for any techno democracy to persuade other countries not to follow China. These countries need a path to digital development, China can offer good quality technology for a good price.
Second, Bradford explains China shows freedom is not necessary for innovation. It is easy for other nations to look at China’s example and argue they don’t need to adopt a democratic model in order to maintain an innovative tech sector.
Bradford concludes by arguing the biggest challenge facing Europe is the threat to liberal democracies around the world. Arguing this battle can be lost if countries like the US and Europe fail to reign in massive tech companies. She notes China has no problem cracking down on any area of technology, whereas the US appears hamstrung by its corporate interests.
The same is the case in Europe where, companies can draw out long and expensive legal battles with governments that attempt to regulate them.
That concludes Bradford's presentation, next up is former President of Estonia, Toomas Hendrik Ilves, who oversaw Estonia’s ascent to a prominent emerging technology market. Ilves warns that, like Bradford, he will also be depressing the audience somewhat by discussing the geopolitical challenges associated with cyber security that are facing Europe today.

Ilves notes since the beginning of the millennium we have transitioned from cyber crime to cyber warfare. He notes the current cyber attacks plaguing critical national infrastructure, with Estonia having to totally shut down in 2007 after widespread DDoS attacks targeting its infrastructure.
He continues that things start getting more serious when hostile governments enter the fray, with very different motivations to financially-driven cyber criminals. Ilves cites the NotPetya worm, which was initially leveraged against Ukraine in 2017, but went on to cause havoc on digital infrastructure around the world. Ilves also points to the example of SolarWinds, which he says taught the security community that once attackers get into the genuine infrastructure of your defense systems the damage they can cause is almost unlimited.
Ilves says cyber security has been largely a national effort which has been an insufficient approach in the face of nation-state acts. Fortunately, Ilves says the US national cyber agencies have made strides in cross-border cyber initiatives, aiming to raise the floor on cyber resilience in organizations around the world.
Ilves argues there needs to be a shift in attitude around regulations, however. Whenever we talk about regulations around technology, the community gets its back up, Ilves argues, noting that the heavy hand of dull regulations often do try to box in a typically anarchic, creative people who tend to think outside the box.
Ilves returns to the 2007 DDoS attacks that crippled Estonia, the country was forced into action which put new efforts into nationwide cyber resilience, citing the voluntary Cyber Defence League initiative.
But Ilves says this is probably not enough to face the threats we now see in today’s security landscape, with a localized approach with national silos inhibiting multinational information sharing that is required to compete in the digital arms race.
He argues the signals intelligence background of many senior figures in the security sector may have led to a general resistance to share knowledge across borders. But Ilves states that borders are meaningless in cyber space, and any defence strategy needs to recognize this fact.
Geopolitical challenges facing the European tech sector
The complete lack of a consideration for security in new EU regulations, according to Ilves, which are instead centered around competition and privacy, which he argues is the result of a legacy attitude around how geopolitically charged the current generation of emerging technologies can become.
Ilves reminds the crowd the playing field is set between adversaries who don't play by the rules and those that do. He says the coalition of China, Russia, Iran, and North Korea, have significant capabilities, predominantly driven by Chinese innovation, but says so do the liberal nations competing with them on the cyber playing field.
Ilves says the problem is that these liberal nations are competing with each other instead of working collaboratively, noting Five Eyes still does not share information with its European counterparts in many instances - “we must be able to rethink security in the digital era".
Ilves draws his presentation to a close with a somewhat pessimistic view that policy makers and politicians are not seeing the bigger picture when it comes to cyber security. He offers some hope that it is the crowd, full of security professionals, who can change this equation and demonstrate what can be possible with collaboration in the security space.
That finishes the first session, we are off for a quick break and we'll be back with live coverage of WithSecure CISO Christine Bejerasco to talk about her 'CISO Ikigai'.
We’re back and Marcus John Henry Brown quickly introduces our next speaker Christine Bejerasco, CISO at WithSecure.Bejerasco will be giving a presentation on the CISO’s Ikigai, which refers to a philosophical concept which gives one’s life a sense of meaning.
Bejerasco gets started by announcing she is around 500 days into her CISO-career at WithSecure, and wants to discuss what she’s learnt over this period. Bejerasco says the CISO role is known for being incredibly stressful, noting that although the fallout from a cyber incident is well known for the pressure, peace time also exerts a certain level of pressure on cyber leaders.

Bejerasco asks how CISOs can reconcile wanting to have peacetime, and wanting to to enjoy that period also without giving in to the pressures that fall on them during this period. Here comes the concept of ikigai, which she concisely defines as one’s personal purpose.
Up on the screen is the Ikigai venn diagram developed by Andrés Zuzunaga, which simplifies finding your personal purpose to four questions.
– What is it that you’re good at?
– What do I love?
– What can I be paid for?
– What does the world need?
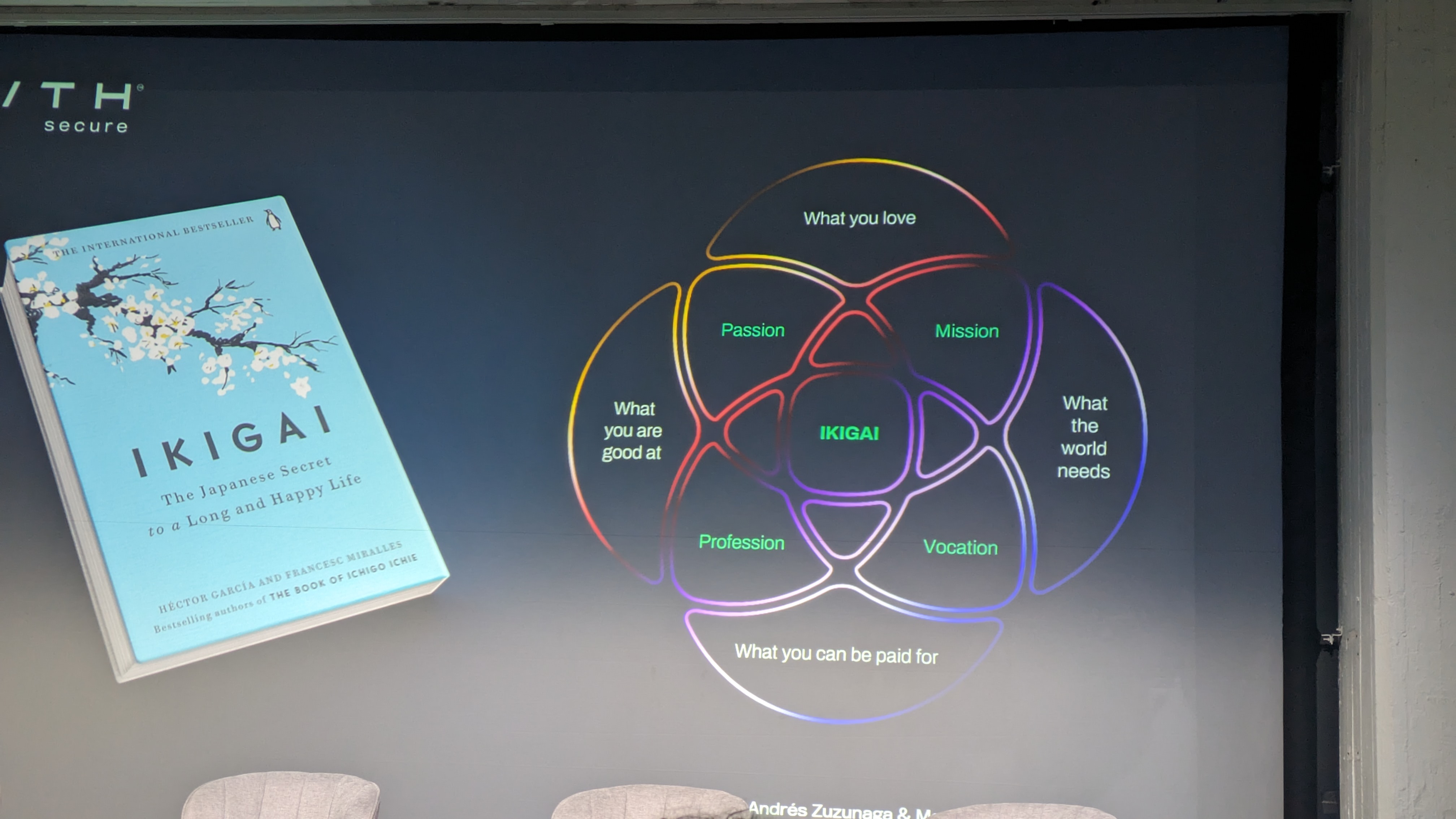
Of course, security outcomes are essential to the CISO role, defining what outcomes are needed to reduce the risks, but a large part of this process is justifying why you are doing what you are doing, Bejerasco explains.
This is particularly hard when your ‘tank is running low’ she notes, touching on the burnout that often afflicts security personnel. Bejerasco refers to a CISO at a large enterprise with over 1,000 staff underneath them, saying it’s impossible for this individual to keep on top of every element of the business’s security strategy.
Bejerasco says this is a universal truth among security staff, and to get round it the concept of taking joy in what we do to benefit the organization is a vital part of being a CISO. She argues we need CISOs who are happy, healthy, and energetic in order to contend with this Herculean task.
She concludes her presentation with the statement 'may you find your ikigai' before bringing on a panel of security leaders to discuss the minimum effective security mindset.
Bejerasco introduces her panel, which consists of Simon Füss, VP IT at IMPREG Group, Stephanie Mayberry, COO at odix, and Satu Koskinen, CIO at YTK.
The minimum effective security mindset is a phrase coined by Gartner referring to taking a minimal effort to inputs while preventing negative impacts on the outputs. Bejerasco says this initially sounded impossible to her and asks the panel how teams will ever accept giving back budget they usually fight so hard to be allocated.
Simon Füss repsons that perhaps we should split this problem into two where we first take on balancing minimum efforts to have the best effective security, which he says should be part of every security strategy, and then look at balancing the impacts on security outcomes.

Building on this, Bejerasco poses a question around how organizations can be proactive in the security measures if they are constantly contending with resource constraints that are concomitant with this minimum effective security mindset.
Satu Koskinen responds that we should not underestimate the importance of training, arguing that although the popular aphorism states humans are the weakest link in an organization's security chain, with proper training they can become the strongest part of their security posture.
Mayberry adds that she often reminds organizations that security is everyone's responsibility, and that ties in to the accountability and culture at that company.
They panel also briefly touches on the current cyber mega trends such as supply chain attacks. Mayberry begins by saying that the first pillar of this approach is that security leaders need to have this conversation with critical third parties noting that a growing issue is that these messages are often not passed down the line.
Koskinen builds on Mayberry's point, adding that this is always a continual process, requiring daily attention. Mayberry also notes that as important as this measure is, every organization needs to pair validation with trust when working with critical third parties.
Beating the heat of being a CISO
The final question of the panel centers around the role exposure management has in an organization's proactive approach to cyber defense, which is fielded by Hüss.
Hüss states that exposure management can really help organizations elevate their security guard as it can help them prioritize easier with a clearer undrstanding of where their most severe threats are coming from.
On top of this, Hüss advises that by combining this approach with internal databases will further improve the insights derived from exposure management tools.
After a rather awkward silence where the crowd was unable to muster a question for the panel, the second session draws to a close, with the final session of the day set to start at after a short networking break.
We are back and Marcus John Henry is back on stage trying to generate some energy in the audience for our final speaker, Keren Elazari, with a session on the future of cyber security from the perspective of an ethical hacker.
Elazari is an Israeli cyber security analyst and senior researcher at the Tel Aviv Interdisciplinary Cyber Research Center. Elazari first puts out a disclaimer that she has never been convicted for a cyber crime, reassuring the audience, but wants to introduce her mentor that showed her how to become a hacker: Angelina Jolie from the cult classic ‘Hackers”.

Now to the meat of the session, Elazari starts by saying the most innovative area of cybercrime over the last year has been ransomware, and more specifically ransomware as a service (RaaS).She claims it is the most successful cybercrime.
Elazari brings up LockBit, one of the most notorious ransomware operators of recent years, and the good news of recent law enforcement operation that shutteered its operations and revealed the identity of one of its leading members, Dmitry Yuryevich Khoroshev or LockBitSupp.
She says while LockBit may be on the run, its affiliates are far from gone, and reports they are working on new projects, specifically developing new payloads targeting the virtualization service Nutanix.
Elazari continues to detail another prominent ransomware operator BlackCat, is implementing another innovative programming technique, called intermittent encryption where only a selection of files and assets are encrypted to help the payload avoid detection on the target system.
Elazari sums up some of these traits in modern cybercrime, RaaS, affiliate programs, double and triple extortion, constant evolution, intermittent encryption, fast and wide exploitation, and cooptitin - a heady mix of affiliates sometimes cooperating with each other, and sometimes fiercely competing with one another.
The current leading ransomware groups still operating are BlackCat, LockBit, Clop, Apos, Akira, according to Elazari. She outlines how these groups are specializing in targeting specific remote monitoring and access tools.
Another trend in the the activity of these groups is a newfound focus on using operation relay boxes (ORB) networks, basically an army of botnets consisting of compromised devices to host the infrastructure underpinning their criminal operations.
Elazari now takes the discussion slightly closer to home, referencing the xz utils compression tool that is built into most leading Linux distributions in the world, developed and maintained by single person called tukaani, from Finland.
In this case a malicious actor pressured tukaani into allowing them to contribute to the project, and then began maliciously inserting backdoors into the tool’s code. Luckily a Microsoft threat researcher spotted the nefarious activity and the backdoors were addressed making it the “major backdoor that never was”.
Malicious LLMs are up next, with some of the biggest names, WormGPT, ThreatGPT, WolfGPT and DarkBard, all being shown on screen. Elazari asserts it is still uncertain how many of these are just scams used to trick less cautious hackers into buying fake software.
An expert we spoke to earlier this year, Eyal Mayor, senior director of security strategy at Cato Networks, said he was doubtful about the abilities of these tools to write exploits for vulnerabilities, stating it was not particularly sophisticated or accurate when writing Python scripts.
The future of cyber crime
Now Elazari is covering the well publicized case of a Hong Kong-based finance worker who was tricked by a video call using deepfakes of their employees to give up sensitive information that led to over $25 million being lost.
Elazari sums up with the rather depressing statement that it is a veritable cyber crime renaissance right now, and she hasn’t even mentioned the actions of nation-state actors using generative AI models, like ChatGPT for different espionage and covert malware development.
With these types of attacks, Elazari says it's all about trust. Bad guys taking advantage of technology to earn and then shatter our trust.
How do we solve this? Elazari thinks the first answer is visibility. She states that organization’s cannot protect what they cannot see. If a hacker has a better understanding of your network, you are in serious trouble, she warns.
We can also learn from hackers, Elazari claims, asking security personnel to adopt a hacker mindset, trying to understand how these attackers think and operate and to refine your defenses accordingly. Bug bounties have proven the worth of thinking like a hacker to shore up defenses and Elazari thinks there is more to be done along these lines.
ElazariIt concludes that it is a time to adapt and evolve, to take action, reassuring the crowd that the future of the security arms race is in their hands.
And that is it for today, the opening day of WithSecure's SPHERE24 is over and the crowd file out of the stifling auditorium.
Here's a quick summary of the new additions to the Elements cloud security platform from the opening session by Antti Koskela, CEO at WithSecure.
• Elements Identity Security for Entra ID to address growing risk of identity-based attacks taken cloud systems offline
• Exposure management designed for mid-market customers, aimed at bolstering a proactive security mentality to minimise potential threats
• Luminem, WithSecure's new generative AI capability that the company states will become an integral part of the Elements cloud experience, with a unique prompt generation system that mitigates the possibility of hallucinations and prompt engineering attacks
Thanks for following along with today's coverage of SPHERE24, and be sure to come back tomorrow for more coverage on the ground in sunny Helsinki.

The keynote theater in the Kaapelitehdas is still rather quiet, with just a smattering of attendees already in their seats. Our host Marcus John Henry Brown is set to take the stage at 9.30 EEST.
But with less than 10 minutes before we get started, a steady stream of people starting to shuffle into the theater. A warning bell rings out and the pace at which people are filing in has definitely increased.

There goes the second bell and the lights are brought down for a stylized video montage. Marcus John Henry Brown is back on stage and welcoming attendees as latecomers quickly find their seats.
He is regaling us with some images from yesterday’s party, where we got to see Finland’s Eurovision 2024 entry Windows95man, or Teemu Keisteri.
Now he takes us through today’s agenda, including a new keynote from Mikko Hyppönen about the irreversible nature of technological advancement, titled ‘We Can't Uninvent Things’.

But now it is time for our first presentation, which will be given by Dr. Kate Darling, an American-Swiss academic working as a research scientist at the MIT Media Lab who will be talking about social robots and the future of AI.
Darling works on the legal and ethical implications of technology and says rather than the technological advancements themselves, she is more interested in when you combine automated technologies with people..
She explains, when people encounter robots like those developed by Boston Dynamics, we see some varied and interesting reactions, ranging from horror to elation. Darling notes that the designers behind these robots did not really take into account the range of reactions they would elicit from human interactions.
Darling says there is an aspect to how we perceive robots that goes beyond what they can do for us. Humans have a tendency to anthropomorphize, projecting human qualities on nonhuman entities,
She notes that over 85% of the Roomba vacuum cleaners have been given names simply because it simulates animation. She says when Boston Dynamics first unveiled spot, the animal rights organization PETA started to receive complaints from concerned people, despite it being inanimate.
This is because Darling argues it is very hard for humans to watch something just move around and not feel like it has some form of agency. She uses an example of giving people a robot that mimics pain and distress when mishandled.
Darling gave the robot to groups of five people, who were simply asked to give it a name and play around with it. After a period of getting to know the robot, Darling reported that she then asked if any would be willing to hit the robot with a hammer.
She says the result shocked her in that she found when the group were asked to hurt the robots none of them were willing to comply. Darling said she was only able to get a group member to hurt their robot by threatening all of the robots. Darling says her conclusion from this and other tests was that people respond to the cues that simulated life gives them, regardless of whether they understand that they are not real.
The implications of this are that companies can lean into this tendency to anthropomorphize. For example, a manufacturing company in Japan got its assembly robots to join in with human coworkers in their morning exercise routine at the facility. This is intended to foster better perception of robots in the workplace, where staff view the robots as colleagues rather than fixed assets or tools.
But Darling warns that social robotics raises some ethical questions. She cites the Google engineer Blake Lemoine who claimed its AI system was sentient, and was widely derided in the media. Darling says we need to take this situation much more seriously, and the proliferation of chatbots means there will be many more instances like this.
One last reason why the anthropomorphization of robots matters, Darling says, is that it is the cause for many misconceptions we have concerning artificial intelligence today. She uses the example of the classic stock image of a brain used to represent artificial intelligence.
Darling says this analogy doesn't make a lot of sense, artificial intelligence as it exists today is not like a human brain, and she says this human comparison really limits us, and going into interactions with robots with this mindset is dangerous.
How do we stop doing this? Darling says that we can use different analogies, which can open people’s minds to new possibilities for what it is. This is integral to challenge the pervasive assumption that robots will or should replace people.
Darling highlights a recent headline ‘No Jobs? Blame the robots’ and say this should instead read ‘No Jobs? Blame company decision-making’, not quite as catchy but a good point.
She explains that the real value is in using robots to provide something we didn't already have. Darling gives an example of an animatronic stuffed animal used to treat dementia patients. Instead of replacing a pet, this facilitates animal therapy in instances where real animals cannot be used for reasons of safety or similar concerns.
The true potential of robotics and AI, Darling concludes, is that is not to replace what we already have, but to partner with these systems.
That’s it from Darling, and she gives way to our next speaker Thomas Anglero, Digital Disruptor and former CTO and Innovation. Picking up where Darling left off, Anglero is here to talk about the fusion of technology, culture and people.
Anglero gets started with the well-trodden ground of generative AI, and wants to give some concrete examples of how businesses can use AI today. First up is using AI to be on video calls with your team.
He says leaders can use AI agents to lead meetings, follow up with colleagues individually after each call. Working with each team member on a 1:1 basis is made possible using AI agents, Anglero says, and you can use this technology today, he notes.

Robotics and the future of AI
Anglero’s wants to show that there is something real behind the often derided hype around AI, but to be clear about where this value lies. He brings up robotic humanoids, using Figure AI, which he says the the ‘top 200 companies in the world’ have already ordered.
Anglero says these robots are going to be deployed this summer, and will combine the intelligence capabilities of generative AI with the knowledge of these large enterprises, assering humanoid robots will be a part of our everyday lives.
Anglero raises the agreement signed between Apple and OpenAI to integrate generative AI natively into iOS 18. He says the frenzy of AI projects can be disorienting and if abused or mismanaged could have some worrying consequences; but he wants to be clear that this is the future and ends on the rather trite claim that “we're the good guys and together we can create an even better world than the bad guys”.
We now go on a break and will be back in roughly 40 minutes for a panel on mental health in the cyber security industry.
The break is over, we are back in the keynote theater and our host is welcoming on our panel guests who will be discussing their experiences around mental health and burnout as security professionals.
Joining Marcus John Henry Brown are Leszek Tasiemski, VP of Product Management, Noora Hammar, head of security assurance Volvo Group, and Sarb Sembhi, chair of MHinCS Foundation.
Hammar kicks things off with a story about two burnouts she went through in her career that stemmed from the lack of support from her line manager. Despite a general awareness of burnout as a growing problem in the security community, Hamma describes the level of psychological safety in that workplace as virtually nonexistent.

Sembhi says Hamamar’s experience is not unique to the industry, and reports that due to the nature of security work and the people the industry attracts, who want to always do the right things to help secure their organization, security pros end up taking on far more work that they cannot keep on top of.
He continues that we often fail to appreciate the sheer scale by which the number of alerts, regulations, have expanded. "All of that is increasing the workflow and we're taking it on because we think it's the right think to do".
Mental health in the security industry
When asked how we can address these concerns, Hammar answers that we need to adopt a top down approach and set an example for the rest of the industry. “People are only human”, and Hammar says we need to remind ourselves of what we are capable of and let technology cover the rest of the equation.
She adds that there is a clear financial incentive for businesses to improve the level of psychological safety, as hiring another staff member is almost always more costly than retaining existing personnel.
Sembhi adds that every nation with a cyber resilience strategy says it depends on cyber resilience of our enterprises, but this misses the fact that the resilience of these businesses is also contingent on the resilience of its personnel. He argues that national leaders need to appreciate this fact if they are to meaningfully move the needle on national cyber resilience.
After another piece of testimony from Tasiemski, the panel is drawn to a close and we welcome our next speaker, Erik Nost, senior analyst at Forrester, who wants to talk about how businesses should approach being more proactive about their security posture, actively managing the risks they are exposed and boosting their cyber resilience.
He breaks proactivity down into visibility, prioritization, and remediation.If a tool in your program does not support one of these elements, then you do not have proactivity.
Nost says it's not enough just to say you are being more proactive about your security strategy. He says instead businesses need to be asking themselves what elements of their program support their ability to be proactive?
Visibility is a key here and Nost notes there is no lack of inputs from this perspective. If anything we seem to have too much of it, touching on the alert fatigue mentioned in the previous panel.
He said this can lead to a world of scattered inputs, complex metrics that makes remediation much more complex.

Nost shows a handy flow diagram showing how security professionals can map out a remediation process combining these three pillars of proactive security.
He says this process is cyclical and very tactical in nature, but ultimately holds up the strategic objective of proactively reducing risk also.
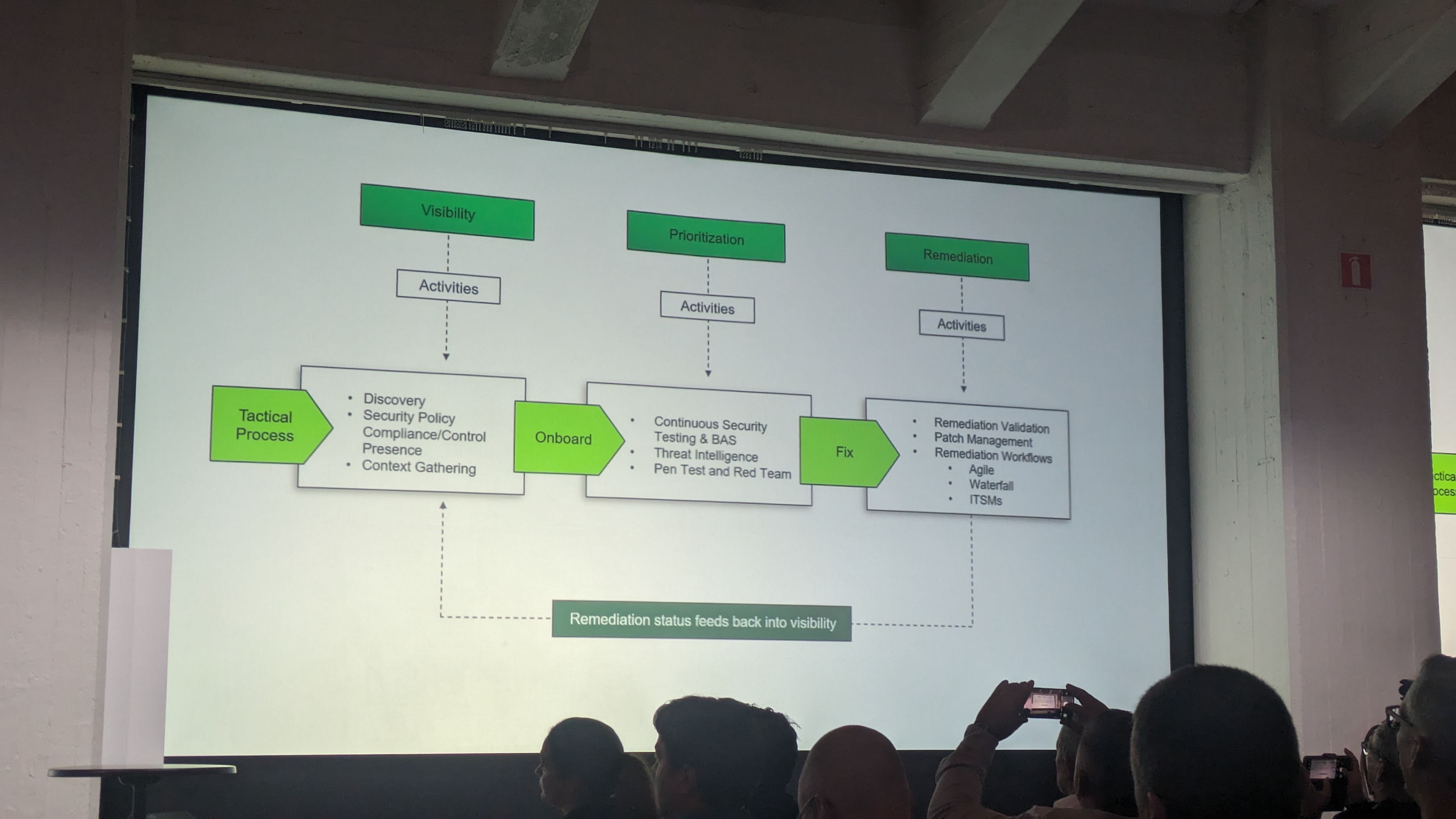
Now Nost is describing where exposure management fits into this picture. Exposure management is a platform capability, and is about consolidating all of the various weaknesses in your organization.
It gives you a top level view of your assets, an assessment of the CVE vulnerabilities and weakness across your environment, as well as a window into what the attacker sees when scoping out your organization.
Nost says a mature, proactive approach to securing your organization revolves around three questions:
• Knowing what you have
• Knowing what you have protecting what you have
• Then mapping how and adversary can get to it
Mapping all of this out will give enterprises an idea of what to fix instead of an exposure bandage, and this is where being able to intelligently prioritize these tasks comes in.
Prioritizing the security tasks according to risk and effort level is central to being able to action the insights gained from exposure management.
The beauty of a smart exposure management system comes in its ability identifying the best remediations for you at any given time, Nost concludes, before thanking the crowd and making a quick exit as the lunch rush ensues.
We'll be back in an hour for the closing session of SPHERE24 delivered by their in-house cyber-celebrity Mikko Hyppönen on the irreversible nature of technological advancement.
Here we go! The final session of WithSecure SPHERE24 is just about to get underway here in Helsinki. Marcus John Henry Brown is back on stage revving up the crowd for the last leg of the conference, thanking the demo, expo, and events teams for their work putting the event together.
But now it’s time to get to the main event, Mikko Hyppönen, chief research officer, and “distinguished voice in digital security”. With a law of cyber security named after him, Hyppönen certainly has the cyber bonafides.
Hyppönen begins by stating that with any technological revolution there come a series of negative consequences, you cannot simply take the benefits these advancements bring. But once the cat is out the bag you cannot turn back and Hyppönen wants to discuss how we can contend with this problem in the latest and upcoming technological revolutions.

With the latest generative AI explosion, identified by many technological luminaries experts as an inflection point in technological development, Hyppönen thinks the benefits clearly outweigh the negatives, and it is merely a question of learning how to live with and mitigate these negative outcomes.
Hyppönen is discussing a number of examples of tools that have provided clear value to everyone in the security industry, but necessarily introduce new issues that make our lives difficult.
For example, strong encryption brought a flood of new possibilities in terms of digitization, privacy, and security, but it can make your life awful when employed by cybercriminals. He adds that once the innovation occurs, and the new technology is in the hands of cyber criminals, we have no choice but to move forward and try to address these concerns, you cannot ‘uninvent’ the technology.
Another similar example of a genuine innovation that brought new opportunities for cyber criminals is the blockchain. Hyppönen lists some of the large ransomware groups that have plagued enterprises over recent years, which he describes as cyber crime unicorns.
Why unicorns? Because they have grown to the point where they can reinvest in themselves as an organization. Hyppönen says these groups have started to become rich enough to invest in physical infrastructure such as data centers.
He mentions the tendency of these groups to invest in their branding, learning from legacy organized crime groups like the Hells Angels or Cosa Nostra. By investing in their public image, these groups can coerce victims more easily using their notoriety to stoke fear of retribution.
Next up is the Tor network, initially developed by the US air force in an effort to build a network that could allow citizens in authoritarian states to use the internet freely. But soon enough this technology became the bedrock of underground markets for drugs, arms, and other illicit items.
Or the quantum computer, which promises to be a revolutionary technology in terms of computing. But it will also give cyber criminals an incredibly large scope for new attack types. Hyppönen says that we should really be getting started on updating our cars, phones, televisions, and other devices for the upcoming onslaught of attacks that quantum computers could facilitate.
Innovation is a one way road
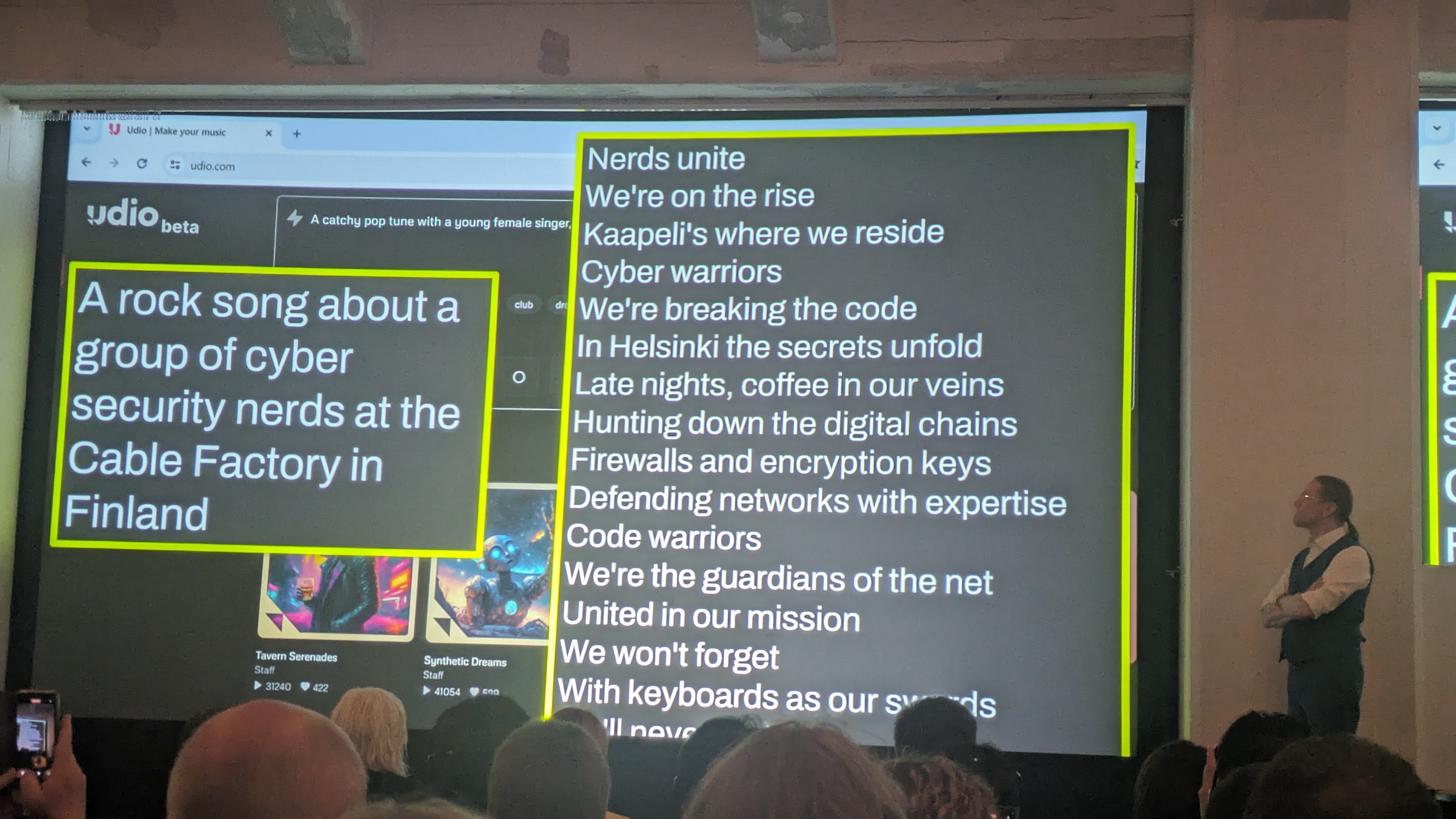
Fiinally we arrive at generative AI, Hyppönen raises an Nvidia H100 above his head, the graphics card that underpins the ongoing boom in LLM adoption, stating it is the real factor behind this ongoing technological revolution.
Last year at SPHERE23 Hyppönen previewed some of the potential capabilities generative AI can create with a rudimentary song generated by an AI model. This year he’s back with a new tune created by the tool Udio. Udio was prompted to create ‘rock song about a group of cyber security nerds at the Cable Factory in Finland' and it sounds a lot more polished than Hyppönen’s efforts last year.
He predicts there will be a top 40 hit created by one of these engines this year, speculating where the royalties will go.
With Hyppönen’s AI-generated tune still blaring on the PA Marcus John Henry Brown is back on stage getting the crowd involved. It looks like things are wrapping up here as both our host and Hyppönen thank the crowd for their engagement and wish them safe travels.

And that’s it for day-two keynotes at SPHERE24 as the attendees file out of the auditorium and get some respite from the heat. Thank you for following along and be sure to keep an eye on ITPro as we continue to bring you the latest from the conference, including in-depth analysis of the announcements.

