Businesses stung by highly convincing Office 365 voicemail scam
This latest wave of phishing attacks incorporates real audio recordings to create a sense of urgency


Cyber criminals are stealing the login credentials of Microsoft Office 365 users using a phishing campaign that tricks victims into believing they've been left voicemail messages.
In the last few weeks, there's been a surge in the number of employees being sent malicious emails that allege they have a missed call and voicemail message, along with a request to login to their Microsoft accounts.
The phishing emails also contain an HTML file, which varies slightly from victim to victim, but the most recent messages observed include a genuine audio recording, researchers with McAfee Labs have discovered.
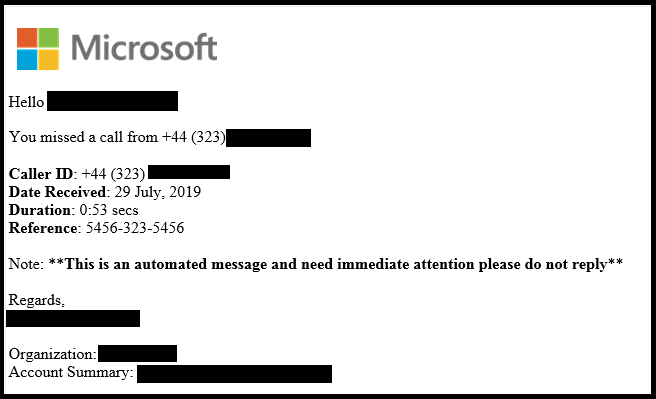
Users are sent fake emails that inform them of a missed call and a voicemail message
When loaded, this HTML file redirects victims to a phishing website that appears to be virtually identical to the Microsoft login prompt, where details are requested and ultimately stolen.
"What sets this phishing campaign apart from others is the fact that it incorporates audio to create a sense of urgency which, in turn, prompts victims to access the malicious link," said McAfee's senior security researcher Oliver Devane.
"This gives the attacker the upper hand in the social engineering side of this campaign.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
This Office 365 campaign has made great efforts to appear legitimate, such as through designing the phishing site to resemble the Microsoft login page. Another trick the cyber scammers use to look real is by prepopulating victims' email addresses into the phishing site and requesting just the password.
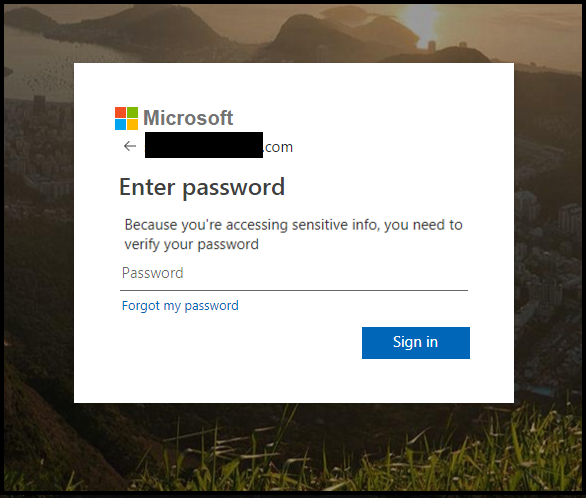
The phishing site appears virtually identical to the actual Microsoft login prompt and preloads victims' emails
Users are presented with a successful login message once the password is provided, and are then redirected to the office.com login page.
Researchers found three different phishing kits being used to generate malicious websites, Voicemail Scmpage 2019, Office 365 Information Hollar, and a third unbranded kit without attribution.
The first two kits aim to gather users' email addresses, passwords, their IP addresses and location data. The third kit uses code from a previous malicious kit targeting Adobe users in 2017, the researchers said, and it's likely the old code has been reused by a new group.
RELATED RESOURCE

6 best practices for escaping ransomware
A complete guide to tackling ransomware attacks
A wide range of employees across several industries, from middle management to executive level, have been targeted, although the predominate victims are in the financial and IT services fields. There's also evidence to suggest several high-profile companies have been targeted.
McAfee has recommended as a matter of urgency that all Office 365 users implement two-factor authentication (2FA). Moreover, enterprise users have been urged to block .html and .htm attachments at the email gateway level so this kind of attack doesn't reach the final user.
"We urge all our readers to be vigilant when opening emails and to never open attachments from unknown senders," the researchers added. "We also strongly advise against using the same password for different services and, if a user believes that his/her password is compromised, it is recommended to change it as soon as possible."
The use of audio in this campaign points to a greater tenacity among cyber fraudsters, who are adopting more sophisticated social engineering techniques. For example, earlier this year artificial intelligence (AI) combined with voice technology was used to impersonate a business owner and fool his subordinate into wiring 200,000 to a hacker's bank account.

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 Should AI PCs be part of your next hardware refresh?
Should AI PCs be part of your next hardware refresh?AI PCs are fast becoming a business staple and a surefire way to future-proof your business
By Bobby Hellard Published
-
 Westcon-Comstor and Vectra AI launch brace of new channel initiatives
Westcon-Comstor and Vectra AI launch brace of new channel initiativesNews Westcon-Comstor and Vectra AI have announced the launch of two new channel growth initiatives focused on the managed security service provider (MSSP) space and AWS Marketplace.
By Daniel Todd Published
-
 Have I Been Pwned owner Troy Hunt’s mailing list compromised in phishing attack
Have I Been Pwned owner Troy Hunt’s mailing list compromised in phishing attackTroy Hunt, the security blogger behind data-breach site Have I Been Pwned, has fallen victim to a phishing attack targeting his email subscriber list.
By Jane McCallion Published
-
 LinkedIn has become a prime hunting ground for cyber criminals – here’s what you need to know
LinkedIn has become a prime hunting ground for cyber criminals – here’s what you need to knowNews Cyber criminals are flocking to LinkedIn to conduct social engineering campaigns, research shows.
By Solomon Klappholz Published
-
 Phishing campaign targets developers with fake CrowdStrike job offers
Phishing campaign targets developers with fake CrowdStrike job offersNews Victims are drawn in with the promise of an interview for a junior developer role at CrowdStrike
By Solomon Klappholz Published
-
 C-suites consider quantum a serious threat and "amazing" deepfake attacks are just 'months away'
C-suites consider quantum a serious threat and "amazing" deepfake attacks are just 'months away'News Deepfake technology has matured at a rapid rate, and video scams are likely to be a on par with the more convincing voice-only campaigns very soon, one expert says
By Rory Bathgate Published
-
 Iranian hackers targeted nuclear expert, ported Windows infection chain to Mac in a week
Iranian hackers targeted nuclear expert, ported Windows infection chain to Mac in a weekNews Fresh research demonstrates the sophistication and capability of state-sponsored threat actors to compromise diverse targets
By Richard Speed Published
-
 Malware being pushed to businesses by search engines remains a pervasive threat
Malware being pushed to businesses by search engines remains a pervasive threatNews High-profile malvertising campaigns in recent months have surged
By Ross Kelly Published
-
 CISA: Phishing campaign targeting US federal agencies went undetected for months
CISA: Phishing campaign targeting US federal agencies went undetected for monthsNews Threat actors used legitimate remote access software to maliciously target federal employees
By Rory Bathgate Published
-
 Google Ads malvertising campaign prompts questions around Search security
Google Ads malvertising campaign prompts questions around Search securityNews A leading security researcher has called into question why Google still allows malware links to top search results
By Rory Bathgate Published