How businesses were left to scramble over data collection for coronavirus contact tracing
The lack of sufficient advice has opened the door for third-party tech firms to normalise massive-scale data harvesting


Whether you’re keen to book a meal out or pick up a coffee on-the-go, it’s impossible to enjoy any of our regained freedoms without sacrificing personal data. With an effective NHS Test and Trace system and mobile phone app still well beyond reach, entrusting food and drink outlets with this information on a long-term basis has become a critical part of the ‘new normal’.
From 4 July, businesses across all sectors were charged with managing reams of customer data, with full guidance published only two days prior. This thrust them into the role of data controllers almost overnight, attached with the strict responsibilities set out under GDPR. “The problem with this started at the very beginning, and the initial guidance was incredibly vague,” Madeleine Stone, legal and policy officer with Big Brother Watch, tells IT Pro.
While some companies, such as fast food chain outlets, may have been versed in data protection principles, smaller venues may have been concerned by the lack of sufficient guidance, Stone says. It’s no surprise, then, that dozens of third-party companies are waiting in the wings to collect contact tracing data on the behalf of those overwhelmed by the entire process.
“It's important to remember that it's pretty much every venue that you might go to,” she continues. “It's churches, places of worship, town halls, libraries, children's centres, cinemas, zoos, so it's a massive amount of businesses covered by this, and a lot of them will not have any experience in collecting this kind of data. So to [have given] them guidance two days before it's due to come out is really not acceptable.”
An invasion of privacy
In light of these extraordinary expectations, the Information Commissioner’s Office (ICO) produced guidance for businesses anxious about the prospect of securely handling data in this way. For organisations with no experience in data collection, the ICO also created a five-step guide that outlines their roles and responsibilities in simple terms. Nevertheless, concerns around data breaches and privacy violations, forecast by organisations like Big Brother Watch, have sadly materialised, with the ICO suggesting it’s looking into a small number of cases that fall into this bracket.
One high-profile incident arose when a postgraduate student with Oxford University, Rose Lyddon, was contacted by a bartender using details she had left with a pub. Stone says it’s no surprise that abuses such as this are happening, with part of the problem being the absence of any Data Protection Impact Assessment (DPIA) to which organisations can refer. It’s not just smaller businesses that can fall foul of this either. In July, the government admitted it hadn’t conducted any DPIA for its flagship NHS Test and Trace programme, which Stone describes as a “massive scandal”.
“The DPIA is basically the heart of data protection in any mission like this. It outlines what could go wrong and what they're going to do about it, and without that, the government and these organisations are really going in blind. It wasn’t surprising – and it was quite depressing – how quickly it happened,” she adds, referring to the case of Rose Lyddon. “I'm sure there are probably lots of other instances where that kind of thing is happening that we don't know about yet.”
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
The consequence, she believes, is that some people will feel they can’t trust their data to be kept securely and aren’t going to want to participate in the scheme, which will in turn affect their community's response to the pandemic.
For its part, the data regulator is seeking to assure the public that it’s generally safe for businesses to collect their data in such a way, with a spokesperson reiterating that the guidance it has issued should stand businesses in good stead. “We appreciate the challenge that many small businesses face in introducing unfamiliar arrangements at speed,” an ICO spokesperson tells IT Pro. “Our focus is on supporting and enabling them to handle people's data responsibly from the outset and, while we will act where we find serious, systemic or negligent behaviour, our aim is to help the thousands of businesses that are doing their best to do the right thing.”
Despite this, research from identity and access management firm Okta would seem to back up Stone’s intuition; the organisation found that 84% of people believe data collected for contact tracing will be used for purposes unrelated to efforts to tackle coronavirus. This has led to concerns that customers will provide false information, which would disrupt the entire contact tracing operation should an outbreak occur. Indeed, in Derbyshire at least, it seems this is already happening, with pub landlords in August criticising a “small minority” of customers who were discovered to have left false information following a minor COVID-19 outbreak.
Third party support
Research from TAAP found the most common method of data collection in venues is pen and paper, with 90% of venues adopting the old-fashioned method, based on a relatively small sample size of “more than 15”. The prevalence of pen and paper has been corroborated by IT Pro’s own research, although venues are increasingly seeking to adopt tech systems to support these efforts. Given the scale of the challenge for many businesses, especially those with no prior data collection experience, may look to third-party companies with a specialism in data collection for support. Those that do will find there are plenty of options available.
London-based fortyeight.ai has been working with Twilio, a communications-focused platform as a service (PaaS) provider, to bring an SMS-based system to venues for customer check-in, for example. Patrons text a six-digit code to a dedicated number and receive a response, which staff can then visually confirm prior to entry. Scottish company Eco, meanwhile, has developed a contactless system reliant on QR codes that not only allows customers to sign in for contact tracing but also access documents like food and drinks menus. This is similar to a system developed by Stampede, which is used in venues run by First Restaurant Group, that relies on either Wi-Fi registration or QR codes to collect and time-stamp customer details.
RELATED RESOURCE

“We want to do right by our customers, reopen responsibly and provide the most normal and enjoyable experience possible,” operations director at First Restaurant Group & The Waterway restaurant, Oliver Etridge, tells IT Pro. “We’ve done a lot of research into how we can collect data securely, comply with government guidelines and support track and trace measures however we can. We found that the Stampede service was the best way of collecting data securely without infringing on the experience of our customers.”
As far as the ICO is concerned, it’s up to organisations to use whatever system best suits them. “It doesn’t have to be complicated, but whatever process they decide to use, they must take account of the basics - be transparent, only collect what you need, keep it secure, delete details and don’t use it for other things like direct marketing,” a spokesperson tells IT Pro.
These companies claim their technologies can reduce the lack of trust many may have when it comes to sacrificing their personal data. For Madeleine Stone, however, these same technologies give her greater cause for concern. “I think there absolutely is a risk [of organisations misusing the data for marketing purposes] and I think it's probably quite likely that it is happening,” she explains. “I'm sure that some companies are completely doing this by the book but there are probably a lot that aren't.
“It only takes one, one of these third-party apps to have a data breach, or to mishandle data, or to use it for marketing purposes, or to sell it on to someone else, and we have a serious issue for all those potentially hundreds of thousands of people who've put their data through this system.”
As far as the aforementioned companies are concerned, they claim their systems are fully compliant with data protection laws. fortyeight.ai, for instance, holds data for the minimum 21-day period in an ‘escrow’, with only individual businesses able to access the contact details. Eco, meanwhile, says all personal data is fully encrypted on secure servers to ensure there are no breaches.
While such assurances are welcome, there’s still cause for unease given such data collection regimes are set to continue indefinitely until, at least, there are effective enough treatments and vaccines to allow life to continue as it was. Indeed, with government contact tracers themselves allegedly falling foul of data protection rules, according to the Times, it doesn’t inspire confidence in those anxious about their privacy being invaded.
Legally, such a regime will be in force as long so it is “necessary” to do so as part of the wider public health response required to combat COVID-19, according to the data regulator. If at some point the public health authorities determine that the measure is no longer needed, then organisations will have to stop collecting the data immediately. For Stone, however, the crux of her concern, and those of other privacy advocates, boils down to the idea that businesses, and the government, have been given the green light to normalise data collection on a massive scale.
“We don't know when [the pandemic] is going to stop,” she says. “It could be indefinite, and that's why we're worried about is this kind of creeping, increasing data collection.”

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up sting
Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up stingNews Europol has detained several people believed to be involved in a botnet operation as part of a follow-up to a major takedown last year.
By Emma Woollacott Published
-
 Young tech professionals are shunning a full-time return to the office – unless it pays more
Young tech professionals are shunning a full-time return to the office – unless it pays moreNews Young tech professionals who entered the workforce post-pandemic expect on-site work to be paid more than remote options.
By Emma Woollacott Published
-
 Phishing emails target victims with fake vaccine passport offer
Phishing emails target victims with fake vaccine passport offerNews Scammers could steal victims’ personal information and never deliver the illegal goods, Fortinet warns
By Rene Millman Published
-
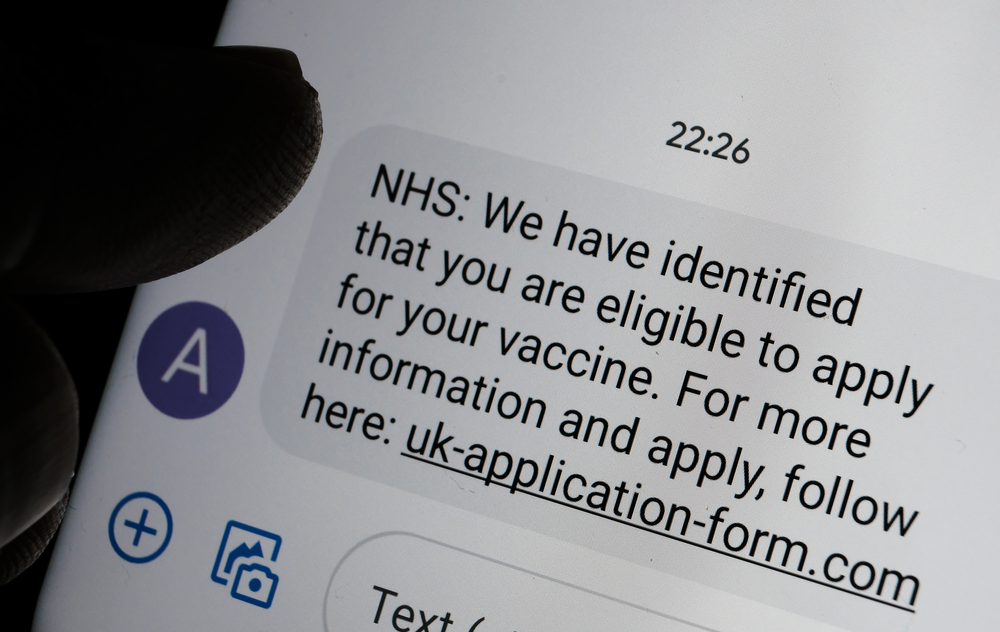 COVID-related phishing fuels a 15-fold increase in NCSC takedowns
COVID-related phishing fuels a 15-fold increase in NCSC takedownsNews The NCSC recorded a significant jump in the number of attacks using NHS branding to lure victims
By Bobby Hellard Published
-
 COVID vaccine passports will fail unless government wins public trust, ICO warns
COVID vaccine passports will fail unless government wins public trust, ICO warnsNews Data watchdog's chief Elizabeth Denham warns that it’s not good enough to claim ‘this is important, so trust us’
By Keumars Afifi-Sabet Published
-
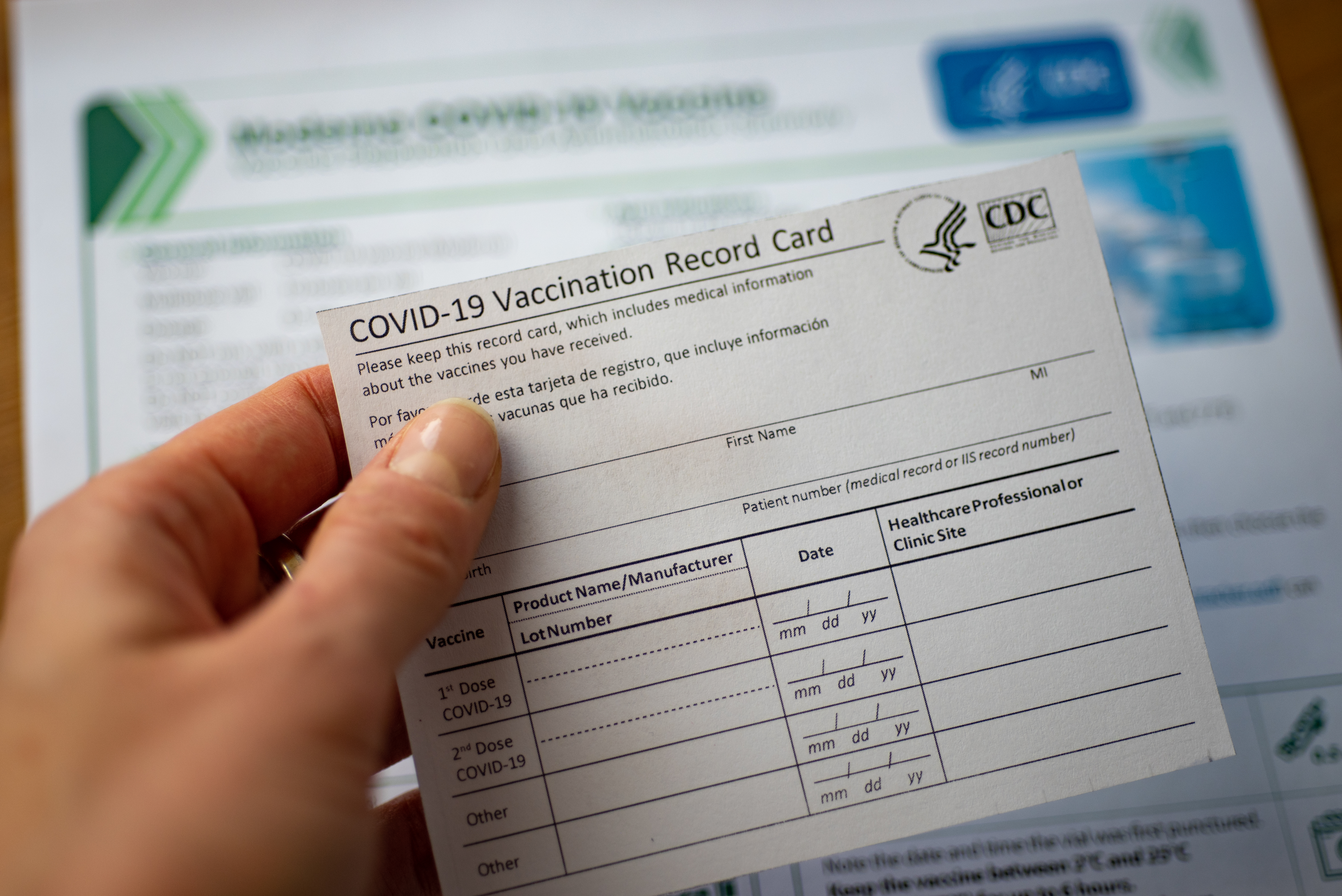 Fake COVID vaccination certificates available on the dark web
Fake COVID vaccination certificates available on the dark webNews Fast-growing market emerges for people wanting quick vaccine proof to travel abroad
By Rene Millman Published
-
 Cyber security firm saw attacks rise by 20% during 2020
Cyber security firm saw attacks rise by 20% during 2020News Trend Micro found attackers also heavily targeted VPNs
By Danny Bradbury Published
-
 Hackers using COVID vaccine as a lure to spread malware
Hackers using COVID vaccine as a lure to spread malwareNews Cyber criminals are impersonating WHO, DHL, and vaccine manufacturers in phishing campaigns
By Rene Millman Published
-
 Website problems slow coronavirus vaccine rollout
Website problems slow coronavirus vaccine rolloutNews Florida is the epicenter of website issues, as patients struggle with malfunctioning sites and hackers
By Danny Bradbury Published
-
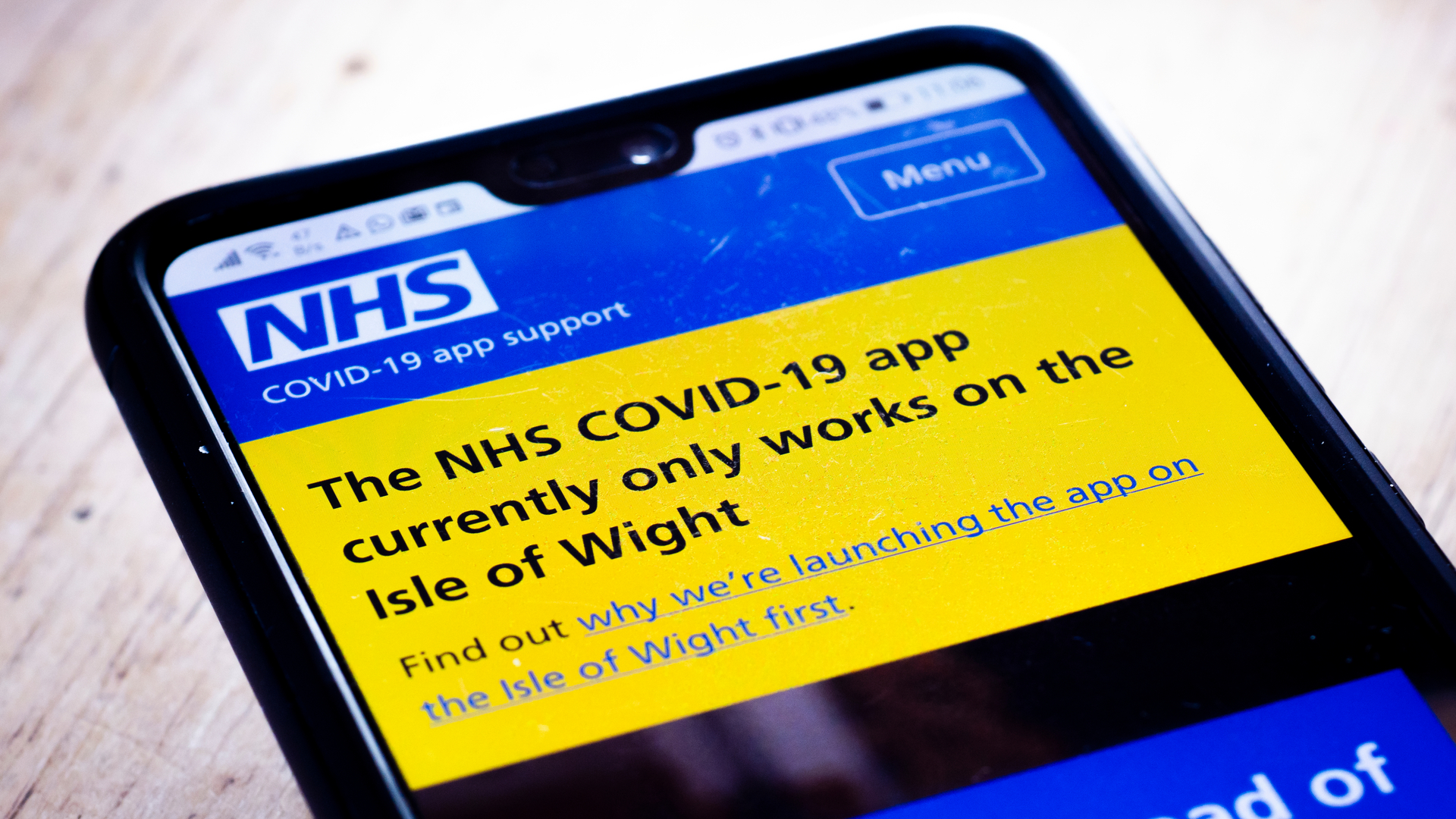 NHS COVID-19 app failed to ask users to self-isolate due to 'software glitch'
NHS COVID-19 app failed to ask users to self-isolate due to 'software glitch'News The bug is the latest in a long line of errors and glitches to plague the government's contact-tracing app
By Keumars Afifi-Sabet Published