Agility, control and freedom: How to maximise productivity while ensuring security
The workforce needs to be mobile, but the organisation needs security. How do you do both?


Employees today have the freedom to use their mobile devices to carry out tasks from any location, but organisations also need to ensure that corporate resources and data are kept safe.
This is a challenge for many organisations, especially as the trend for a growing mobile workforce is increasing. By 2018, the number of employee-owned smartphones and tablets used in the enterprise is expected to top one billion devices, according to figures from Juniper Research.
Greater and more numerous security threats
This also means that there is a greater attack surface from hackers and those keen to steal confidential data. This will only get worse as a dearth of security awareness, even indifference, among staff exposes companies to exploits.
Users downloading content and apps can expose organisations to malware and data snooping software. They will frequently use devices on unsecured networks at coffee shops, airports, hotels, and other public places, meaning corporate data stored on such devices is especially susceptible to breaches.
Privacy issues
In addition to that, data protection legislation, like the EU's upcoming GDPR rules, place greater importance on individuals' privacy, and place stringent regulations on organisations to secure and respect such data: staff with personal data on their devices don't expect their employer or IT staff to be able to access it.
To overcome this problem, and protect the business, some organisations are implementing corporate-owned mobile devices to isolate personal apps and data from corporate ones. But this doesn't get rid of all security anxieties.
Dongle Danger: Don’t let your company get caught out General Data Protection Regulation (GDPR)
Printing confidential information securely from mobile
When employees or contractors bring their mobile device, such as an iPhone or an iPad, into the workplace, sooner or later they will want to print out documents stored on these devices.
An issue here for organisations is that as the number of users grows, managing them and their printing rights becomes more complex. It poses the question: who can print where?
Another problem is that corporate networks are often built to represent their office and administrative environments. In other words, each department has its own subnet, and AirPrint does not work across subnets.
Security plays an integral role for many companies; they must transfer sensitive data securely over the network. For mobile printing, the transfer of data from iOS devices to the printer must be protected.
Managing applications and remote access securely
Remote users need access to organisational resources and applications to be productive, but it's essential to enable this access in a secure way.
Building a distinct network for mobiles can ensure that personal devices and mobile apps are validated before allowing them to access the network in line with corporate security policies.
Enterprises can implement a master security policy that enables access to corporate data and parts of the main network from mobile devices, while helping to ensure that no data leaks through personal devices.
Organisations should have in place a mobile user remote access policy to protect data from mobile threats. This means users must have a PIN or strong password to access a device's OS or apps, providing an initial defence against information theft if a mobile device is lost or stolen.
Enterprises should also deploy mobile access with authentication, network access controls and a VPN to enable only approved users and devices, along with whitelisted mobile apps, to access corporate resources.
Adding encryption to mobile devices can be a highly effective way to defend against data loss and theft. Enterprises can set and manage encryption policies based on users, groups and data sensitivity. Doing so on tablets and smartphones mitigates the risk of storing information on such corporate devices.
Another way of giving employees greater freedom while retaining control is to isolate enterprise apps and data from personal apps and data. Organisations can do this by creating a container (a cordoned-off workspace environment) on personal devices. This stops personal and corporate apps or data becoming mixed up, and helps combat the danger of corporate information compromise.
Organisations should also keep control of their employees' mobile environment by using identity and access management. Including mobility within this can mitigate security risks, even while users bring their own devices into the enterprise. A good identity and access management strategy can allow line of business managers to decide what access should be given to whom.
Overcoming secure printing challenges
When it comes to secure print management from an iPhone or iPad, organisations should use hardware and software to determine who is allowed to print and which printer they can use by connecting it to their Active Directory.
Essentially, it can be arranged that only Active Directory members are allowed to print, ensuring that non-members who can access the WLAN are not able to print. If an organisation wants finer control, they can define which Active Directory member can print to which printer (or not).
Securely managing mobile printing over different networks needs a solution that overcomes subnet boundaries, so that even though an iOS device is connected to the department WLAN (subnet), it can still print to a printer integrated into another subnet.
Lastly, to ensure better security, print data transmitted between iOS devices and a print server should be encrypted, for instance through point-to-point-encryption (P2PE).
Greater transparency, control and security
As the number of smartphone and tablet users within a company continues to increase, so does the need for transparency, control and security.
A mobile printing device, such as the Primos Enterprise AirPrint Server from SEH, could help your organisation print from your employees' iOS devices more securely, increasing flexibility and agility. Unlike many other solutions, Primos does not use a cloud, meaning sensitive print data remains in a company's network at all times.
Picture credit: SEH
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
-
 What to look out for at RSAC Conference 2025
What to look out for at RSAC Conference 2025Analysis Convincing attendees that AI can revolutionize security will be the first point of order at next week’s RSA Conference – but traditional threats will be a constant undercurrent
By Rory Bathgate
-
 Ransomware attacks are rising — but quiet payouts could mean there's more than actually reported
Ransomware attacks are rising — but quiet payouts could mean there's more than actually reportedNews Ransomware attacks continue to climb, but they may be even higher than official figures show as companies choose to quietly pay to make such incidents go away.
By Nicole Kobie
-
 New Microsoft Teams features for business users
New Microsoft Teams features for business usersIn-depth All the latest Microsoft Teams features after the platform is given a redesign, complete with an AI-powered assistant and a faster engine
By Danny Bradbury
-
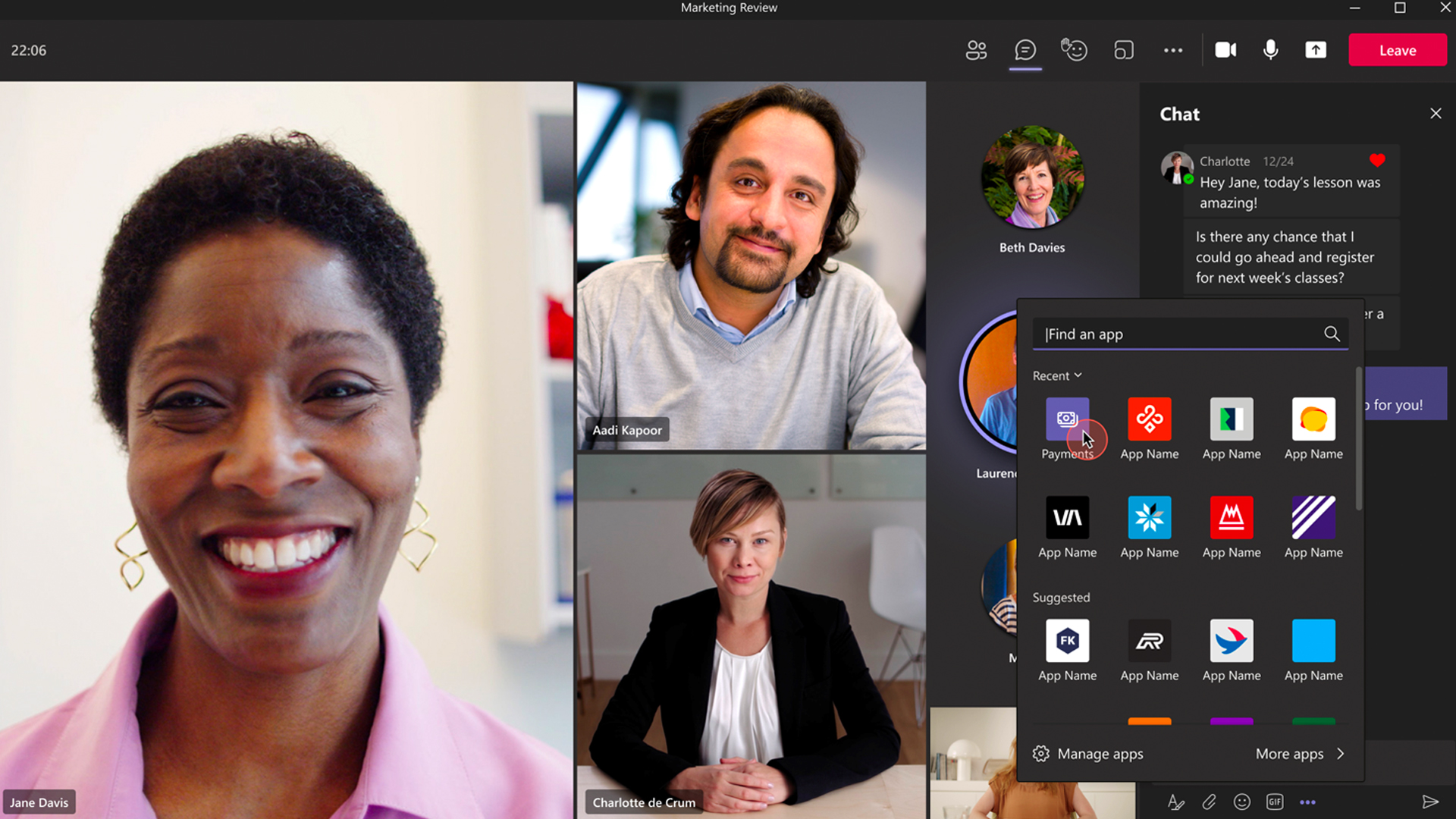 Microsoft Teams now allows SMBs to collect payments in meetings
Microsoft Teams now allows SMBs to collect payments in meetingsNews With the help of PayPal, Stripe, and GoDaddy, the Microsoft Teams Payments app offers in-meeting payment requests
By Connor Jones
-
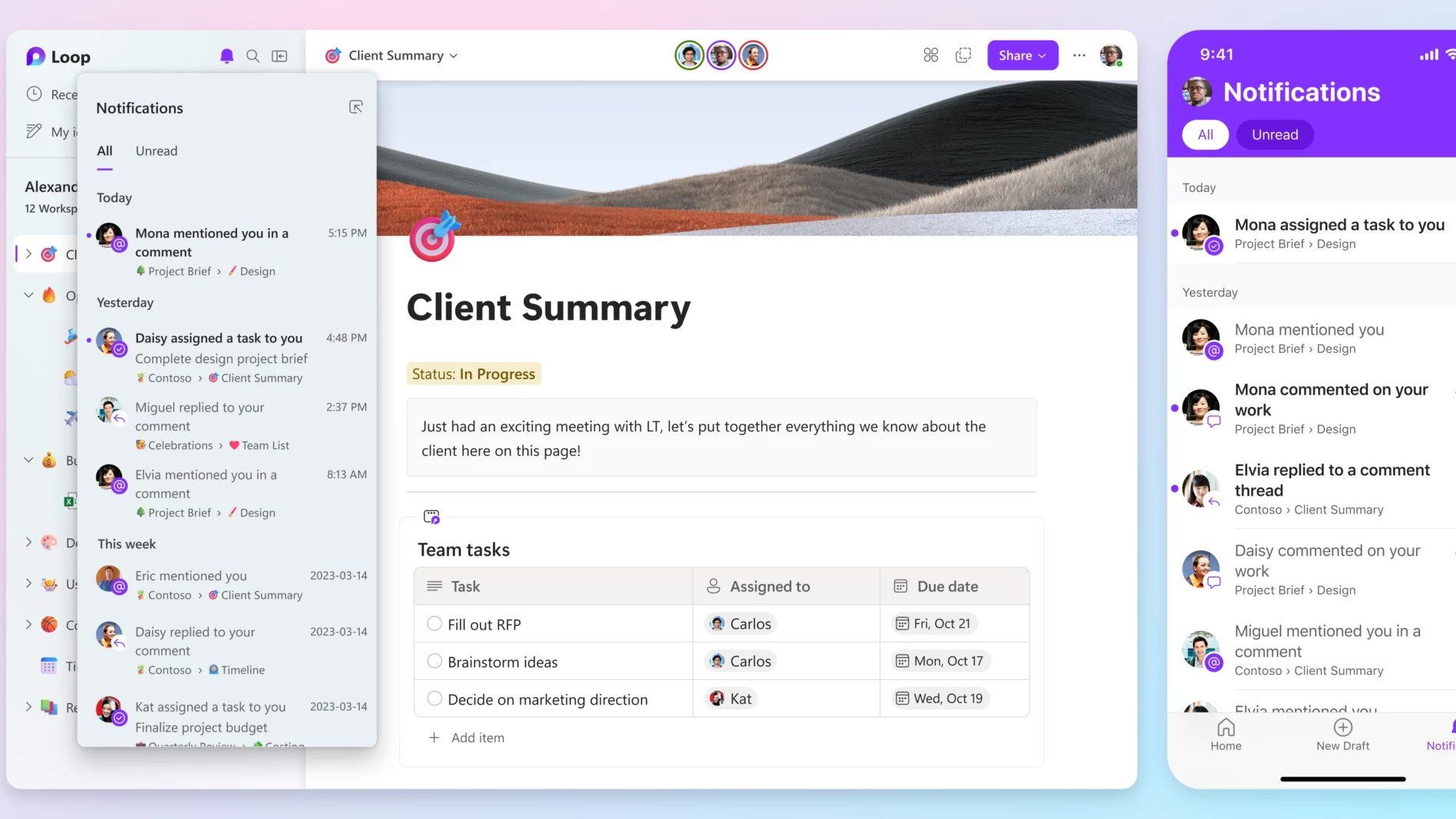 Microsoft launches collaboration platform Loop, its answer to Notion
Microsoft launches collaboration platform Loop, its answer to NotionNews Greater collaboration tools are coming to the Microsoft 365 suite, aiming to help teams work together without having to jump between different apps
By Zach Marzouk
-
 Meta Quest Pro preview: Meet Meta's 'laptop killer'
Meta Quest Pro preview: Meet Meta's 'laptop killer'Opinion We go hands-on with the Meta Quest Pro, as the firm banks on turning hardware preferences upside down
By Bobby Hellard
-
 Microsoft launches Places, includes GPS-style navigation to help find meeting rooms
Microsoft launches Places, includes GPS-style navigation to help find meeting roomsNews The new app built specifically for organisations adopting a permanent hybrid work model brings new features to manage people and the workplace itself
By Connor Jones
-
 The IT Pro Podcast: Enabling bilingual business
The IT Pro Podcast: Enabling bilingual businessIT Pro Podcast How Wales is using digital tech to deliver a greater choice of languages
By IT Pro
-
 Podcast transcript: Enabling bilingual business
Podcast transcript: Enabling bilingual businessIT Pro Podcast Read the full transcript for this episode of the IT Pro Podcast
By IT Pro
-

 Qnap KoiBox-100W review: An intriguing alternative
Qnap KoiBox-100W review: An intriguing alternativeReviews A versatile and affordable videoconferencing solution with great wireless screen presentation features
By Dave Mitchell