Biggest hacks of 2014: From Apple to eBay, no-one is safe
On the heels of the Sony Pictures hack, we take a look at other high-profile targets

Banks, retailers and tech firms all succumbed to high-profile cyber attacks this year, proving that no company is invulnerable from hacking.
We take a look at the biggest hacks of 2014, which led to leaks of everything from films and private celebrity photos to payment details and addresses.
SONY PICTURES
The film studio has been the most recent victim of hackers, with the attack on its systems being so devastating, employees had to switch to pen and paper.
What was leaked?
Hackers obtained over 100 terabytes of data ranging from employee passwords and credit card details to medical histories and executive salary details.
Unreleased movies including Annie, Fury, Still Alice, Mr Turner and To Write Love on Her Arms have been leaked as well as the social security numbers of celebrities such as Sylvester Stallone.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Who did it and how?
A group known as Guardians of Peace' or GOP' took responsibility for the attack. Upon turning on their computers employees were supposedly greeted with the following message:
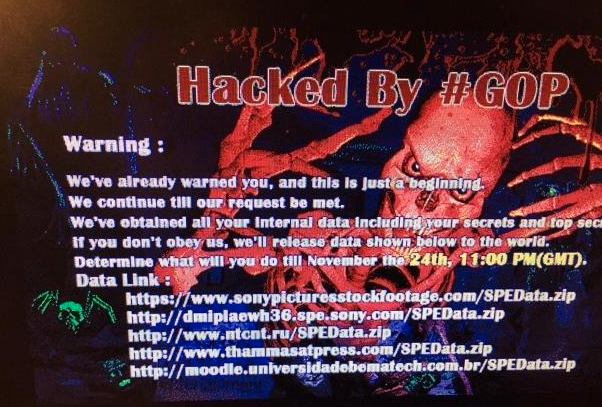
Fingers have been pointed at North Korea, which is said to have carried out the state-led attack in retaliation for Sony's involvement in the upcoming movie The Interview'. This is a comedy where the plot revolves around a plan to kill the North Korean leader Kim Jong-Un.
North Korea has denied being directly involved and as the perpetrators have been taunting Sony online and posting information on Pastebin, it does appear to suggest it wasn't a state-led attack as these are usually clandestine.
A malware analysis has been carried out by security experts at Blue Coat and they claim that preparation for the attack began as early as May.
"The first sample reviewed is a worm that spreads via SMB. Inside was a text file that contained over 10,000 mappings between internal host names and IP addresses," the firm said.
"This indicates the attackers had already performed recon of the network, knew what machines they were interested in targeting and had already obtained previous access before this sample was deployed."
Interestingly, Blue Coat confirmed there was a Korean language resource section in the code, suggesting the perpetrators could be based in the country.
The fallout
So far the leaked movies have been downloaded an estimated 2 million times. A source also told Buzzfeed, the cost of fixing the IT systems is likely to outweigh any losses at the box office.
The FBI has been contacted to investigate the breach and Sony has offered past and present employees 12 months of fraud protection to help mitigate any impact.
Perhaps more worryingly for Sony was that this isn't the first major breach it has had to deal with and it seems to be a popular target. As of 8 December, Sony's online store was also taken down by a group known as the 'Lizard Squad'.
------------------------------------------------------------------------------------------
APPLE iCLOUD
This wasn't the biggest breach of the year, but it gained the most attention due to the sensitivity of the content that was released at the end of August.
What was leaked?
Hundreds of nude images of female celebrities including Jennifer Lawrence and Kate Upton were obtained from Apple's iCloud service and released on 4Chan in an event dubbed "The Fappening".

Credit: 'Sad iCloud' courtesy of Ben Cameron -http://strangepaul.com
Who did it and how?
A 4Chan user who referred to himself as "a collector" tried to shop around the images privately before they were released.
Reddit became a primary source of distribution through the TheFappening' sub-reddit, which was subsequently banned by admins. Images were also shared on Twitter.
Celebrity iCloud accounts are believed to have been accessed by using a combination of simple brute force password attacks and by answering basic security questions.
The fallout
Although Apple has always maintained it wasn't "hacked", there is no denying that the private content was obtained from its iCloud service. After the leaks, the firm did increase security.
Apple now sends out notifications when requests are made to access the iCloud through a web browser or restore data to a device.
All the victims condenmed the invasion of privacy. Actress Gabrielle Union, who had private pictures released, confirmed she had contacted the FBI over the incident.
Joy Corrigan, a 20-year old model who also had her pictures leaked, said she previously flagged suspicious activity on her account but no action was taken by Apple. She has mounted a class-action lawsuit against the firm and Apple could be forced to pay out substantial damages if it is found to be at fault in court.
------------------------------------------------------------------------------------------
JP MORGAN CHASE & CO.
Despite having an expected spend of $250 million on cyber security during 2014, America's biggest bank couldn't prevent hackers from gaining access to its network.
What was leaked?
Details of 76 million US households and 7 million SMBs were compromised.Stolen data included names, addresses, phone numbers and email addresses.
Who did it and how?
Sources told Bloomberg that the origins of the hack could be traced back to cybercriminals located in Russia, and even pointed to a possible state co-ordinated attack. However, the perpetrators remain unknown.
The hackers are believed to have exploited flaws in one of the bank's websites and then used zero-day malware to gain access to the network and manipulate records.
The fallout
The FBI and US Secret Service have been investigating the cause of the breach. JP Morgansaid customers would not be liable for any unauthorised transactions carried out on their account.
It's unclear what the financial impact of the hack has been, but the reputational damage experienced by the firm could take more time to overcome.
------------------------------------------------------------------------------------------
WEBCAM HACK
One of the more bizarre and voyeuristic hacks of 2014 came to light last month when it was revealed that live feeds were being broadcast online from webcams around the world.
What was leaked?
A Russian website called Insecam was found to be streaming live video from thousands of webcams (excluding laptops) in a huge invasion of privacy.
In the UK, around 584 webcams were originally available to view, (135 as of writing) including feeds fromoffices, factories and even a pub in Egham. At one point, children and babies could be seen sleeping.
Who did it and how?
As mentioned the website was set up in Russia. The firm claims it does not hack into security cameras, instead they are accessed because they are not password protected or because they use default login credentials.
The fallout
The website is still up and running and provides a stark warning about networked cameras. Users of such devices are urged to make sure they use a secure password.
------------------------------------------------------------------------------------------
EBAY
The popular auction website had one of the biggest breaches of all time, when data of all its users was stolen.
What was leaked?
Personal details including addresses, phone number and dates of birth belonging to all 145 million customers were stolen.
Who did it and how?
Cyber criminals are believed to have compromised a small number of employee log-in credentials. These were then used to gain unauthorised access to eBay's corporate network.
The fallout
eBay was criticised for telling users about the hack two weeks after it found out. However, despite sitting on news of the breach, the firm claiming there was no evidence of increased fraudulent activity.
All users were advised to change their passwords after the breach was made public.
The US states of Connecticut, Florida and Illinois joined forces to investigate the company's security policies, along with the country's Federal Trade Commission.
The UK data protection watchdog, the Information Commissioner's Office (ICO), initially said it would launch a probe into the breach. However, after establishing eBay was registered as a data controller in Luxembourg, it told IT Pro no further action would be taken.
------------------------------------------------------------------------------------------
HOME DEPOT
Yet another well-known US brand was added to the list of hacking victims this year in what was the biggest retail breach to-date.
What was leaked?
The DIY giant had 53 million email addresses and 56 million payment details stolen from its servers.
Who did it and how?
No group has claimed responsibility for the hack.
The cybercriminals are believed to have used third-party vendor credentials to access Home Depot's network.
Zero-day malware was then deployed on Home Depot's self-checkout systems in the US and Canada, which gathered customer payment details.
The fallout
The hack highlighted the dangers when enterprises are slow to upgrade their security systems.
Since the hack, Home Depot enhanced encryption of payment data in all US stores and pushed out EMV chip-and-PIN technology, which has been used in the UK since 2004.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published