NSA & GCHQ SIM card hack: Gemalto denies encryption keys stolen through hack
Special mobile unit was set up in 2010 to steal encryption keys

SIM card maker Gemalto has shared details of its investigation into claims British and US securities services hacked the company to steal billions of encryption keys.
Privacy International blasts security services
"GCHQ has lost it's way. In stealing the SIM card encryption keys of millions of mobile phone users they have shown there are few lines they aren't willing to cross," the charity told IT Pro.
"Hacking into law-abiding companies, spying on their employees and stealing their data should never be considered 'fair game.'
"The mentality of 'Act first, worry about the law later' has to come to an end. Unrestrained, unregulated Government spying of this kind is the antithesis of the rule of law and they must be held accountable for their actions."
The two agencies are said to have joined forces to set up a specialist Mobile Handset Exploitation Team (MHET) in April 2010, documents by The Intercept revealed. The unit's mission was to target vulnerabilities in mobile devices.
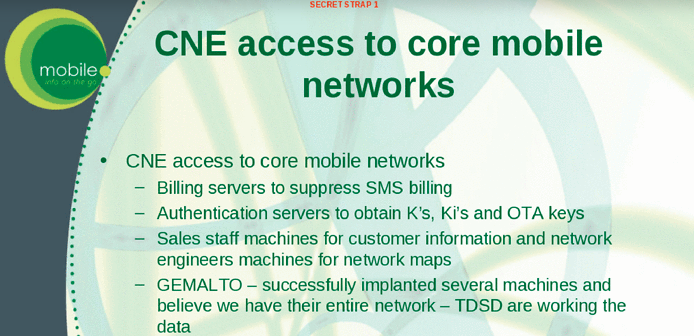
Operatives worked to infiltrate Dutch company Gemalto, which produces 2 billion SIM cards a year and serves 450 telecoms operators across the globe, it was claimed.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
A top secret slide (below) confirmed the NSA and GCHQ had gained access to Gelmato's network and mined the private communications of engineers and sales employees.
The claims are the latest in a long line of revelations to have been made public by NSA whistleblower Edward Snowden.
By stealing encryption keys, the intelligence agencies were able to monitor mobile communications without approval from telecom companies and foreign governments, all without being traced.
In a statement published on 25 February, the organisation said it has reason to believe the NSA and GCHQ were behind a series of attempts made in 2010 and 2011 to hack into the company and its network.
"At the time we were unable to identify the perpetrators but we now think they could be related to the NSA and GCHQ operation," the statement reads.
"These intrusions only affected the outer parts of our networks - our office networks - which are in contact with the outside world.
"The SIM encryption keys and other customer data in general, are not stored on these networks," the statement added.
Therefore, it denied claims the security services were able to steal the SIM encryption keys because the NSA and GCHQ appear to have only succeeded in breaching its office networks.
Instead, Gemalto's investigation into the matter has suggested the NSA and GCHQ may have targeted other parts of its SIM card supply chain to get access to the encryption keys, rather than via its own network.
Furthermore, it also denies that it ever sold SIM cards to four out of the 12 operators listed in the leaked documents.
Gemalto described the attacks as as "serious and sophisticated", but said no signs of malicious activity were observed anywhere else in its networks.
"No breaches were found in the infrastructure running our SIM activity or in other parts of the secure network which manage our other products such as banking cards, ID cards or electronic passports," the statement continued.
"We are conscious that the most eminent state agencies, especially when they work together, have resources and legal support that go far beyond that of typical hackers and criminal organisations.
"And, we are concerned that they could be involved in such indiscriminate operations against private companies with no grounds for suspicion," the statement concluded.
When the allegations first came to light last week, Gelmato said in a statement that the security services appear to have tried to reach as many mobile phones as possible.
"We cannot at this early stage verify the findings of the publication and had no prior knowledge that these agencies were conducting this operation," the firm said.
"We take this publication very seriously and will devote all resources necessary to fully investigate and understand the scope of such sophisticated techniques."
This article was originally published on 25/2/15 and updated on the same day to include details of Gemalto's investigation.
-
 Should AI PCs be part of your next hardware refresh?
Should AI PCs be part of your next hardware refresh?AI PCs are fast becoming a business staple and a surefire way to future-proof your business
By Bobby Hellard
-
 Westcon-Comstor and Vectra AI launch brace of new channel initiatives
Westcon-Comstor and Vectra AI launch brace of new channel initiativesNews Westcon-Comstor and Vectra AI have announced the launch of two new channel growth initiatives focused on the managed security service provider (MSSP) space and AWS Marketplace.
By Daniel Todd
-
 Former GCHQ intern risked national security after taking home top secret data
Former GCHQ intern risked national security after taking home top secret dataNews A former GCHQ intern has pleaded guilty to transferring data from a top-secret computer onto his work phone.
By Bobby Hellard
-
 Businesses must get better at sharing cyber information, urges former GCHQ chief
Businesses must get better at sharing cyber information, urges former GCHQ chiefJeremy Fleming, the former head of GCHQ, has warned businesses face increasingly sophisticated cyber attacks on critical national infrastructure (CNI).
By Rory Bathgate
-
 Hackers are lying low in networks to wage critical infrastructure attacks - here’s how they do it
Hackers are lying low in networks to wage critical infrastructure attacks - here’s how they do itNews Hackers are researching key IT workers in their bid to gain access to vital systems
By Steve Ranger
-
 ASUS, Cisco, Netgear devices exploited in ongoing Chinese hacking campaign
ASUS, Cisco, Netgear devices exploited in ongoing Chinese hacking campaignNews Critical national infrastructure is the target of sustained attempts from state-sponsored hackers, according to Five Eyes advisories
By Ross Kelly
-
 US reveals bespoke tool that took down Russian malware operation
US reveals bespoke tool that took down Russian malware operationNews Snake had been used to steal NATO countries’ data for 20 years
By Rory Bathgate
-
 Move away from memory-unsafe languages like C and C++, NSA urges
Move away from memory-unsafe languages like C and C++, NSA urgesNews The US agency advises organisations to begin using languages like Rust, Java, and Swift
By Zach Marzouk
-
 US gov issues fresh warning over Russian threat to critical infrastructure
US gov issues fresh warning over Russian threat to critical infrastructureNews The FBI, NSA and CISA have urged network defenders to be on "heightened alert" for Russian cyber attacks
By Connor Jones
-
 UK and US pledge to punish cyber criminals at annual meeting
UK and US pledge to punish cyber criminals at annual meetingNews Intelligence and defence officials met at the annual forum to discuss approaches to cyber security for the years ahead
By Connor Jones