AA: Our handling of security breach fell short
Breakdown firm apologises after security researchers claim cover up


The AA has admitted that a recent data breach "should have been handled better", apologising to customers after initially denying that credit card information was left at risk as part of the breach, before later acknowledging that it was.
AA President Edmund King said the company was "aware of concerns that we fell short in our handling of reports that some personal data from the AA Shop online had been compromised", adding that it accepts the criticism it should have been more transparent, in an email to affected customers sent on Friday.
The company was notified in April that 13GB of database backups were publicly accessible via an unsecured Amazon Web Services bucket, which it then took offline without notifying customers of the potential data leak - something it will soon have to do under incoming data protection rules.
However, security researchers later discovered that more than 100,000 user accounts of the AA Accessories Shop had been exposed as part of the breach, which the AA blamed on a third-party provider that operates the shopping service.
The breakdown company had previously denied that the "data issue" contained any credit card information, and claimed, in a tweet sent on 3 July, that the matter had been resolved.
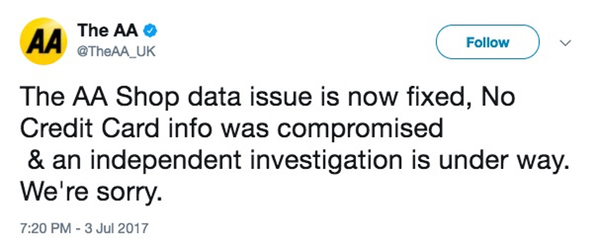
However, the company has beencriticised by security researchers who claim its actions amounted to an attempted cover-up, as it tried to downplay the full scope of a data leak that is now known to have included personal information, and "partial payment card information".
Security analyst and breach notification expert Troy Hunt said that the AA had "consciously elected not to notify subscribers after being alerted to the disclosure of 13GB worth of publicly accessible database backups back in April".
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
The breach is said to have included the names, email addresses, phone numbers, as well as credit card details of customers who used the AA online shop at any time before January 2017. The company maintains that the information isn't enough to make purchases, and that there is currently no evidence that the data has been exploited.
Customers also complained in June that they had received emails notifying them that their passwords had been changed, and to contact a number for support. At first the AA said it wasn't responsible and that it was investigating the matter, later claiming it was the result of an internal error.
Although customers were advised that their passwords had not been changed and that accounts remained safe, some reported being unable to login.
The AA maintains that there is "no connection" between the recent password blunder and the data breach. "We are obviously sorry about both unrelated incidents and any worry that they have caused," said AA president Edmund King, in a statement sent to IT Pro.
Screenshot courtesy of Troy Hunt
Main image: Bigstock
04/07/2017:AA security breach 'spilled 100,000 customers' personal data'
The AA has admitted to a security issue on its shop website after reports that data including customers' names, addresses, email addresses, and partial credit card information has been exposed on a publicly-accessible server.
The company said in a statement that it was informed of a potential vulnerability involving some AA Shop data on 22 April 2017, adding that it was fixed three days later. In a tweet, the AA added that no credit card information was "compromised".
But Motherboard reports that details of 100,000 AA customers were exposed, sharing details of security researcher Scott Helme's own investigation, and spoke to affected customers who said the AA had never directly informedthem of the breach.
The database relates to an online shop run by the AA offering a selection of vehicle-related goods. The breach first surfaced around a week ago. Security researcher Troy Huntsaidhe had been contacted by someone who claimed to have told the AA that it had a security issue back in April. It was claimed that around 123GB of database backups had been exposed.
Since then the AA has opened an independent inquiry into the issue and informed the UK's data watchdog, the Information Commissioner's Office (ICO), about it.
"Legal letters warning against a dissemination breach under the Computer Misuse Act' will be issued. The ICO has been informed and we have commissioned a full independent investigation into the issue," the AA said in a statement.
"We take any data issues incredibly seriously and would like to reassure our AA Shop customers that their payment details have not been compromised."
The ICO said it was aware of an incident involving the AA and would make enquiries.
"When organisations detect a breach, it should be their first priority to inform all affected customers and take steps to ensure the continued protection of any exposed data," said Ross Brewer, VP & MD of EMEA for security firm LogRhythm. "Failing to do so can, and often does, result in confidential information being left in the wild' for longer than it needs to be. It only takes one hacker to be in the right place at the right time to cause very real damage."
"Cyber criminals could easily be among them [the affected users], meaning that we should be prepared that the entire 100,000 database is breached and will be for sale on the dark web soon," claimed Ilia Kolochenko, CEO at High-Tech Bridge. "However, I would avoid any panic until a first confirmed incident, involving records from the breached database, appears. In any case, victims of the breach are better to cancel their credit cards and change all their passwords if they had same or similar ones for all the accounts."
Dale Walker is a contributor specializing in cybersecurity, data protection, and IT regulations. He was the former managing editor at ITPro, as well as its sibling sites CloudPro and ChannelPro. He spent a number of years reporting for ITPro from numerous domestic and international events, including IBM, Red Hat, Google, and has been a regular reporter for Microsoft's various yearly showcases, including Ignite.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published