The rise of ransomware as a service
Ransomware is no longer just for hackers - it's available off-the-shelf


Ransomware as a service (RaaS) is designed so that anyone, no matter how limited their programming knowledge, can get started in cybercrime. Professional criminals write and package the code before making it available for amateurs to download and use, flooding the market with new ransomware strains in the process.
Read Kaspersky's free security bulletin The ransomware revolution' for a deep-dive view of ransomware and other security threats
While this is not a new trend, the model is developing rapidly, with increasing numbers of ransomware creators offering their malicious products on demand'. This approach has proved immensely appealing to criminals who lack the skills, resources or inclination to develop their own.
This makes ransomware very cheap to download and easy to spread, compared to other types of malware and cyber attacks which require a higher level of programming and distribution knowledge. It is this growth in RaaS platforms which is likely to be one of the primary drivers behind the huge spike in ransomware attacks over the past 12 months.
Notable examples which appeared last year and use this model are Petya/Mischa (see below) and Shark ransomware, which was later rebranded under the name Atom and offered a high 80% share on ransom payments. Other popular tools like Satan claim to enable distribution of ransomware in under a minute.
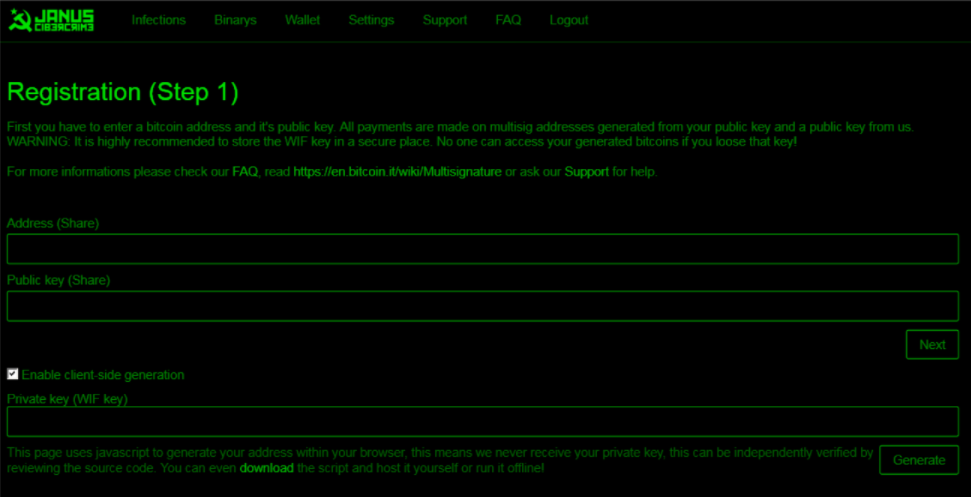
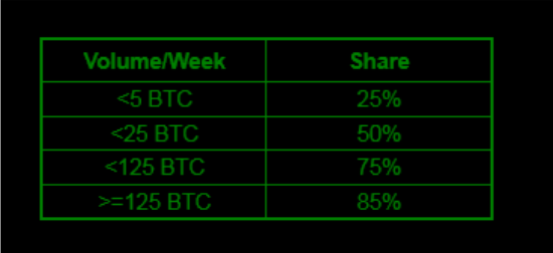
The business model for RaaS is a simple, franchise-like deployment model. Instead of writing and deploying their own ransomware software, a criminal will sign up to a traditional commission-based arrangement. One example is Peyta ransomware (see table below); if a partner makes 125 Bitcoins a week, they will walk away with 106.25 Bitcoins after commission. Some even get to see an estimate of their potential earnings before they sign up.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
There is also often an initial usage fee. Someone looking to use the Stompado ransomware, for example, needs to spend just $39 to get started. Other RaaS authors instead opt to take a cut of each ransom, incentivising a higher volume of attacks.
Have you protected your infrastructure from the risks of ransomware? Keep up to date with current threats to businesses with Kaspersky's security whitepaper detailing trends from the past year.
With other criminals offering their services in spam distribution and ransomware notes, it's no longer difficult for an amateur attacker to get started.
Typical antivirus solutions are designed to stop known attacks, so unfortunately are relatively ineffective against such a rapidly growing number of new ransomware strains. Using a reliable security solution, particularly one with a dedicated ransomware feature is an important way to keep your data and devices secure.
Businesses should also take steps to educate employees and IT teams about suspicious emails, and what to do in the event of falling victim to a ransomware attack. IT teams can take steps such as keeping sensitive data separate, restricting access and backing up everything regularly to mitigate the effects of a potential ransomware attack.
Petya RaaS screenshots via Kaspersky Security Bulletin 2016, The Ransomware Revolution, p13
Esther is a freelance media analyst, podcaster, and one-third of Media Voices. She has previously worked as a content marketing lead for Dennis Publishing and the Media Briefing. She writes frequently on topics such as subscriptions and tech developments for industry sites such as Digital Content Next and What’s New in Publishing. She is co-founder of the Publisher Podcast Awards and Publisher Podcast Summit; the first conference and awards dedicated to celebrating and elevating publisher podcasts.
-
 Cyber attacks against UK firms dropped by 10% last year, but experts say don't get complacent
Cyber attacks against UK firms dropped by 10% last year, but experts say don't get complacentNews More than four-in-ten UK businesses were hit by a cyber attack last year, marking a decrease on the year prior – but security experts have warned enterprises to still remain vigilant.
By Emma Woollacott Published
-
 IBM just unveiled its new z17 mainframe – and it's built with AI performance in mind
IBM just unveiled its new z17 mainframe – and it's built with AI performance in mindNews IBM has released the latest version of its mainframe, the z17, aimed at supporting AI workloads and inferencing.
By Emma Woollacott Published
-
 Healthcare systems are rife with exploits — and ransomware gangs have noticed
Healthcare systems are rife with exploits — and ransomware gangs have noticedNews Nearly nine-in-ten healthcare organizations have medical devices that are vulnerable to exploits, and ransomware groups are taking notice.
By Nicole Kobie Published
-
 Alleged LockBit developer extradited to the US
Alleged LockBit developer extradited to the USNews A Russian-Israeli man has been extradited to the US amid accusations of being a key LockBit ransomware developer.
By Emma Woollacott Published
-
 February was the worst month on record for ransomware attacks – and one threat group had a field day
February was the worst month on record for ransomware attacks – and one threat group had a field dayNews February 2025 was the worst month on record for the number of ransomware attacks, according to new research from Bitdefender.
By Emma Woollacott Published
-
 CISA issues warning over Medusa ransomware after 300 victims from critical sectors impacted
CISA issues warning over Medusa ransomware after 300 victims from critical sectors impactedNews The Medusa ransomware as a Service operation compromised twice as many organizations at the start of 2025 compared to 2024
By Solomon Klappholz Published
-
 Warning issued over prolific 'Ghost' ransomware group
Warning issued over prolific 'Ghost' ransomware groupNews The Ghost ransomware group is known to act fast and exploit vulnerabilities in public-facing appliances
By Solomon Klappholz Published
-
 The Zservers takedown is another big win for law enforcement
The Zservers takedown is another big win for law enforcementNews LockBit has been dealt another blow by law enforcement after Dutch police took 127 of its servers offline
By Solomon Klappholz Published
-
 There’s a new ransomware player on the scene: the ‘BlackLock’ group has become one of the most prolific operators in the cyber crime industry – and researchers warn it’s only going to get worse for potential victims
There’s a new ransomware player on the scene: the ‘BlackLock’ group has become one of the most prolific operators in the cyber crime industry – and researchers warn it’s only going to get worse for potential victimsNews Security experts have warned the BlackLock group could become the most active ransomware operator in 2025
By Solomon Klappholz Published
-
 Ransomware missteps that can cost you
Ransomware missteps that can cost youWhitepaper Agile risk management starts with a common language
By ITPro Published