How to make your email hack-proof
How to secure your inbox, enhance your mail and unlock secret codes

Even with the rise of social networks and messaging apps, email is still the most popular means of online communications and remains essential for registering with websites, confirming your identity and receiving important information.
Most email services are far from perfect, however, despite the introduction of GDPR and improvements to spam filtering and anti-phishing protection. Some of the most well-known services fail to protect your data from hackers, invade your privacy by scanning message content, and generally lack important features we all want and need.
In this advanced guide, we show you how to become an email power user by unlocking the full potential of your webmail service.
Create a fake 'burner' email address
When you use your real email address to register with a website, you're not only opening yourself to a deluge of marketing messages (despite the recent introduction of GDPR), you're also handing over an essential piece of personal information.
If the site suffers a security breach, your email address could fall into the hands of cyber criminals, compromising the safety of your other online accounts.
The best way to avoid being spammed, scammed and hacked is to create a temporary fake address using a disposable-emails service. Use this fake address to sign up to a website, click the link in the confirmation message that arrives in your alternative inbox and you'll gain access to the site without sacrificing your privacy or security.
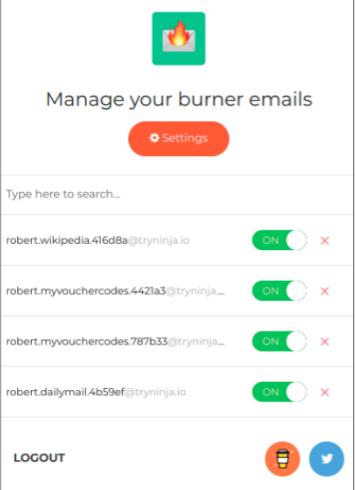
Burner Emails conceals your real email address when you register with sites
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Our favourite new tool for this task is Burner Emails. It's available for Firefox and Chrome, and also works with Opera and Vivaldi. This browser extension automatically detects email fields on web pages and lets you click them to generate and enter fake addresses. Messages sent to these addresses are then forwarded to your real account, so you won't miss important verification and confirmation emails. You can then delete or disable each 'burner' address so you won't receive any further communication from that site.
We also like the Firefox add-on Bloody Vikings, which lets you create fake addresses on the fly using 14 disposable email services, including Dropmail, Fake Mail Generator and Mailinator. Usefully it opens your temporary inbox in a background tab, so you can confirm your registration without leaving the page. Another handy Chrome extension is Disposable Temporary Email Address, which generates accounts that expire after 10 minutes.
Stop third-party tools reading your emails
Google recently admitted that the contents of Gmail messages are not only processed by computer algorithms but can sometimes be read by human third parties, when certain apps are granted access to user accounts. With so many useful tools available for Gmail, this situation is difficult to avoid, but it still pays to know exactly which apps you've allowed to access your emails so you can block any that look suspicious.
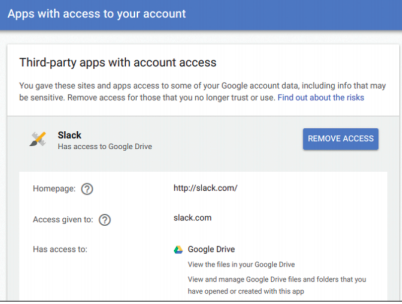
Remove unwanted third-party apps that have access to your Gmail account
To find out which of your apps can access your email, go to your Google Account and click the 'Apps with account access' link in the 'Sign-in & Security' section. Click Manage Apps to view further details about what personal data third-party apps can access, and click remove Access to disconnect undesirable tools from your Gmail account.
Make two-factor authentication easier to use
Two-factor authentication (2FA) also known as two-step verification adds a second layer of protection to your email account by asking you to enter a code when you sign in from a new device or if you've been logged in on your current one for 30 days. In January, Google software engineer Grzegorz Milka admitted that fewer than 10% of Gmail users have enabled this feature but if you're security-conscious, it's definitely worth setting up.
To do so, head here, click 'Get Started', then sign into your Gmail account and click 'Start Setup'. Enter your mobile number, choose how you want to receive the verification code and click Send Code. When you receive the six-digit code, enter it in the box and click Verify to add your phone number to your account.
If you prefer, you can use Google's Prompt feature, which saves you having to type a code each time. Instead, you tap Yes to confirm that you're trying to sign in from another device. This method is less secure, so Google recommends it's used only on phones and tablets that have screen lock activated. You can also print one-off back up codes to use as your convenience.
To set up 2FA for Outlook.co, go to the new 'Security Settings' page and sign into your account. Under 'Two-step verification', choose 'Set up two-step verification' to turn the feature on, then follow the instructions. You can opt to receive your verification codes by text message or phone call, or have them sent to an alternative email address, but the easiest method is to use an authenticator app, such as Microsoft Authenticator or Authy, which also works with Gmail.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published
-
 Microsoft Authenticator mandates number matching to counter MFA fatigue attacks
Microsoft Authenticator mandates number matching to counter MFA fatigue attacksNews The added layer of complexity aims to keep social engineering at bay
By Connor Jones Published
-
 As Google launches passwordless authentication for all, what are the business benefits of passkeys?
As Google launches passwordless authentication for all, what are the business benefits of passkeys?News Google follows Apple in its latest shift to passwordless authentication, but what are the benefits?
By Ross Kelly Published
-
 There's only one way to avoid credential stuffing attacks
There's only one way to avoid credential stuffing attacksOpinion PayPal accounts were breached last year due to a credential stuffing attack, but can PayPal avoid taking responsibility?
By Davey Winder Published
-
 Google Authenticator 2FA update accused of making service less secure
Google Authenticator 2FA update accused of making service less secureNews Lack of end-to-end encryption in code backup has some developers worried
By Rory Bathgate Published
-
 Five things to consider before choosing an MFA solution
Five things to consider before choosing an MFA solutionIn-depth Because we all should move on from using “password” as a password
By Rene Millman Published
-
 What is multi-factor authentication (MFA) fatigue and how do you defend against attacks?
What is multi-factor authentication (MFA) fatigue and how do you defend against attacks?In-depth Strong authentication is key to security, but it needs to be properly managed to avoid MFA fatigue
By Sandra Vogel Published
-
 Beyond Identity strikes up strategic partnership with World Wide Technology
Beyond Identity strikes up strategic partnership with World Wide TechnologyNews WWT will implement Beyond Identity’s authentication platform internally while also acting as a global channel partner
By Daniel Todd Published
-
 Implementing strong authentication across your business
Implementing strong authentication across your businessIn-depth Strong authentication is hugely important, but implementing any regime at scale is not without its challenges
By Sandra Vogel Published