Financial email accounts of 5,000 UK organisations publicly exposed
Companies "making it easy" for attackers to steal sensitive data and sell accounts online


The financial details of at least 5,000 UK companies have been exposed in third-party compromises, with attackers selling exposed email accounts for as little as $150 online.
Cyber security firm Digital Shadows found 33,568 finance department email addresses exposed in third-party breaches in its data breach repository, with 4,953 tied with .co.uk domains. Of all the company accounts exposed, 83% had passwords associated.
But concerningly, cyber criminals are able to easily access the 12.5 million email archive files publicly exposed due to improper backup procedures, and wouldn't need to breach an organisation's security in order to do so.
"One issue that this research particularly highlights is the risk posed by third parties and contractors, who are often forgotten about by businesses and security teams when it comes to defending your network and data," Digital Shadows' strategy and research analyst Rafael Amado told IT Pro.
"Often, short-term workers will back up their files and emails on personal NAS drives and leave this misconfigured.
"This issue goes beyond email account compromises. Businesses need to have a better understanding of where all their sensitive data resides and who has access to it. Third parties and suppliers are an important component of this."
Digital Shadows found a wealth of data exposed across misconfigured servers including rsync sites, file transfer protocol (FTP) servers, server message block (SMB), Amazon Web Services (AWS) S3 buckets, and NAS drives. The majority of these files, some 8.5 million, are .EML, while the rest comprise .MSG, .PST, .MBOX and .OST.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Some of these emails are incredibly sensitive, with analysts finding in one instance a whole accounting firm's email correspondence with clients made publicly-available including thousands of invoices and tax returns.
This latest research follows Digital Shadows' findings earlier this year that 12,000TB of data was found publicly exposed in the first three months of 2018 on misconfigured rsync sites, FTP servers, SMB, ASW S3 buckets, misconfigured Websites (WebIndex), and web-connected NAS drives.
The FBI earlier this year estimated that the damage to businesses from the practice known as business email compromise (BEC), including fake invoices and wire fraud, globally cost businesses $12 billion over the last five years.
Once compromised, businesses' financial details are frequently shared and traded on criminal forums and on the dark web.
Hacking services are available for as low as $150, but finance department credentials are lucrative, with Digital Shadows finding individuals offering up to $5,000. Many are searching for company emails that contain ap@, ar@, accounting@, and invoice@, among other terms.
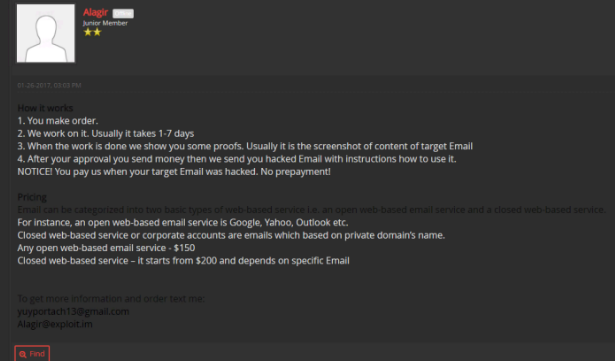
A forum user offering hacking services from as little as $150
Alongside services for acquiring business emails, malicious actors are known to offer between $150 and $500 per compromised businesses email. Some accounts, however, such those based on open web-based email services are more expensive than closed ones.
Through covert interactions, Digital Shadows' analysts engaged with one Russian-speaking threat actor who sought sensitive data from email archives.
In this case study outlined in the research, analysts learned the attacker wanted emails from accounting departments of specific targets and was searching specifically for accounts with accountspayable@, accountsreceivables@, payables@ and receivables@.
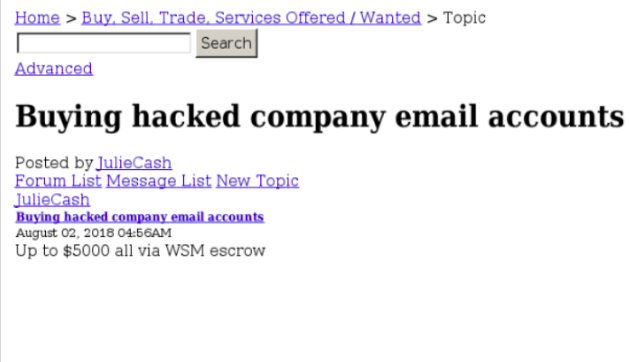
Some Dark Web users are paying up to $5,000 for hacked email accounts
The attacker specified 100 targets in this campaign, including organisations in construction (56), education (18), property (10) sectors, as well as 15 other companies. The majority of these were based in the UK, Australia, and Singapore.
"Business Email Compromise is becoming increasingly profitable for threats actors, who are conducting highly targeted campaigns," the research said. "Unfortunately, we're making it easy for adversaries to gain access to the precious information that sits within email inboxes."
Digital Shadows recommended seven steps for employees and businesses to take to bolster their protection against BEC. These include updating security awareness training to include such scenarios, as well as building them into contingency plans.
Analysts also recommended that manual controls be implemented in wire transfer applications which can monitor for exposed credentials.
But above all, preventing email archives from being publicly exposed is crucial. Risks can be mitigated by using strong, unique passwords and disabling guest access, as well as whitelisting IP addresses if an internet connection, or passwordless-access, is needed.

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published