How to choose a one-stop business security package
Looking for a simple, cost-effective way to protect your data? Here's what to look for in a UTM appliance or cloud service


Every business needs to take its IT security seriously and that most definitely includes smaller organisations. You might think your company isn't big or important enough to attract the attention of cyber criminals, but this is the type of thinking that leads businesses to skimp on security measures. And that's exactly what the bad guys are looking for.
Make no mistake, we're not talking about a theoretical threat. The UK government's 2018 cybersecurity survey found that 43% of businesses had suffered a data security breach over the previous 12 months and the potential cost has never been higher.
Every SME collecting, storing and using personal data is expected to comply with the General Data Protection Regulation (GDPR), which includes a requirement to keep customer data out of the hands of unauthorised third parties. If your business fails to do so even unintentionally you could face a fine of up to 20 million, or 4% of your annual turnover, whichever is higher. Even if you escape a fine, the NCSC estimates that each security breach for micro and small businesses costs around 1,400.
There's only one answer. Every SME needs to invest in network, endpoint and mobile security. We've reviewed all-in-one solutions from Kaspersky, Panda, Sophos and Zyxel; they're all easy to deploy and manage, and a lot cheaper than dealing with a breach.
The gatekeeper
Smaller businesses don't tend to have the IT resources to manage complex security systems. One popular approach, therefore, is to invest in a UTM (unified threat management) appliance also called a gateway appliance which integrates all the key security services in a single unit. Deployment is thus made as simple as possible, and since all internet traffic passes through one point on the network perimeter, it's relatively easy to monitor connections and enforce security policies.
The range of security functions on offer varies from model to model. The most basic UTM unit might be little more than a glorified firewall, but the appliances we've tested are much more versatile. Features include VPN services for secure site-to-site and remote user connections, and both appliances also include built-in wireless network services. This is a great feature that again simplifies management, as it ensures that both wired and wireless clients go through exactly the same security checks and restrictions.
On top of that, you can add on subscription-based options including antivirus, web content filtering, intrusion detection and prevention, application controls and antispam. With all these features on the table, it pays to research the licensing options, to ensure you're not paying for capabilities you don't want. If you're willing to invest for the long term, you can also make savings by committing to a three-year subscription, rather than a regular annual one.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
The two UTM units we reviewed were the Sophos XG 125w and the Zyxel USG60W.
Send in the cloud
If you don't have the expertise or the infrastructure to manage your own UTM appliance, there's another option: cloud-based security. This works on a similar principle to on-premises threat management, except that the "appliance" is a virtual server hosted by a trusted security vendor.
To ensure that all traffic is inspected and managed in accordance with your policies, a lightweight agent is deployed on all servers, desktops, laptops and mobiles. This then picks up and applies your security settings from the central management host.
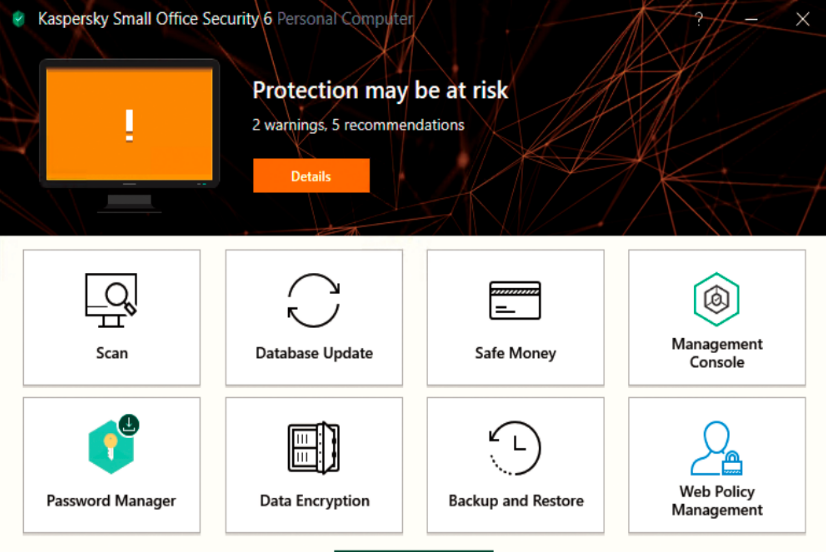
Kaspersky uses a small endpoint agent to protect your PCs and smartphones
Regardless of which security model you've chosen, it's normal to install some sort of endpoint protection software (EPS) on your clients. A good EPS agent will include a local firewall function, antivirus, application controls, website filtering and options to run on-demand and scheduled malware scans. EPS software can also manage access to removable devices and physical ports - something that can't be handled by a central UTM appliance.
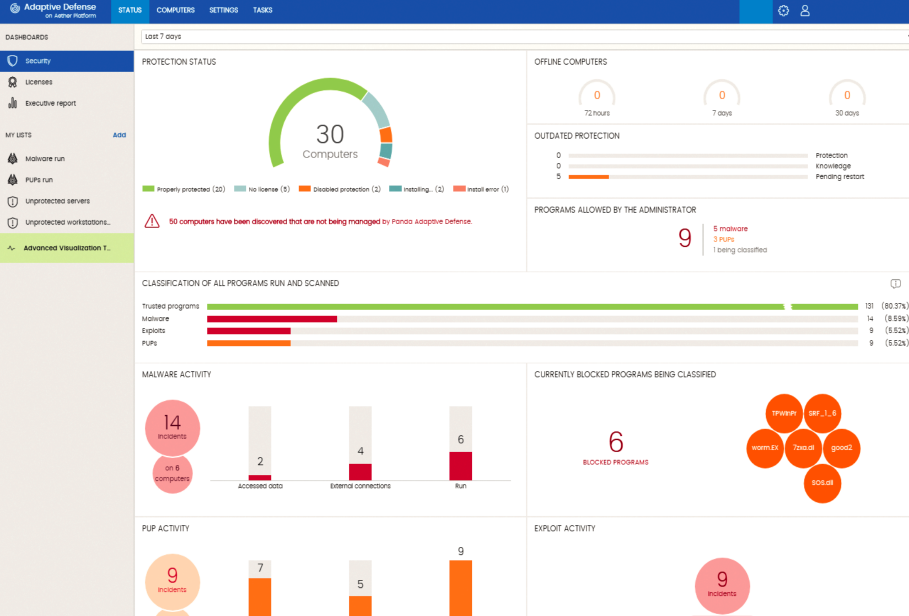
Panda's cloud portal presents a wealth of detail about detected threats
In everyday use, the functional difference between on-premises and cloud-hosted security isn't huge. The key benefits of a cloud service are that the setup costs are lower, and it's easier to manage a diverse workforce that may be spread across multiple sites, or include workers who spend their time at home or on the road.
The cloud suites we revied were Kaspersky's Small Office 6 and Panda's Adaptive Defense 360.
Feature finder
Whether you choose a cloud-based or UTM security solution, there are a number of key features that should be on your shopping list.
A firewall is a must, as this blocks intruders from probing your network and endpoints looking for ways to gain access. If you choose a UTM appliance you can expect it to include a powerful business-class firewall; if you're going down the EPS route, check that it's able to provide the sort of flexible protection you need.
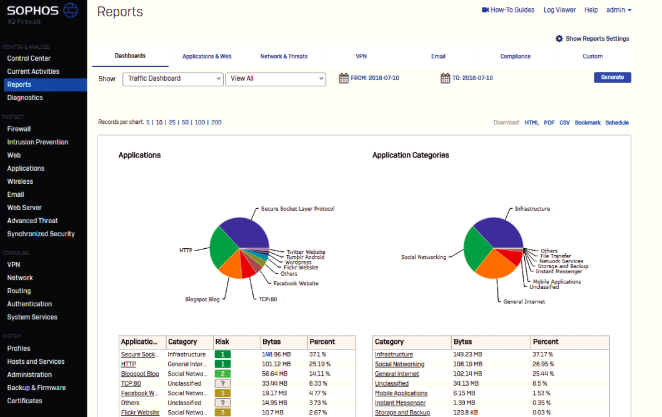
Sophos can tell you at a glance what apps are being used on your network
Malware protection is another essential component of any unified security product. If possible, choose a product that provides web and email antivirus services as well as regular file scanning, to block malicious software before it can even get onto an employee's desktop.
Then there's web content filtering, which lets you decide what types of websites your users are allowed to visit. The best solutions are the ones that offer fine granular controls, so that (for example) staff can use the company Facebook pages, while Twitter remains blocked.
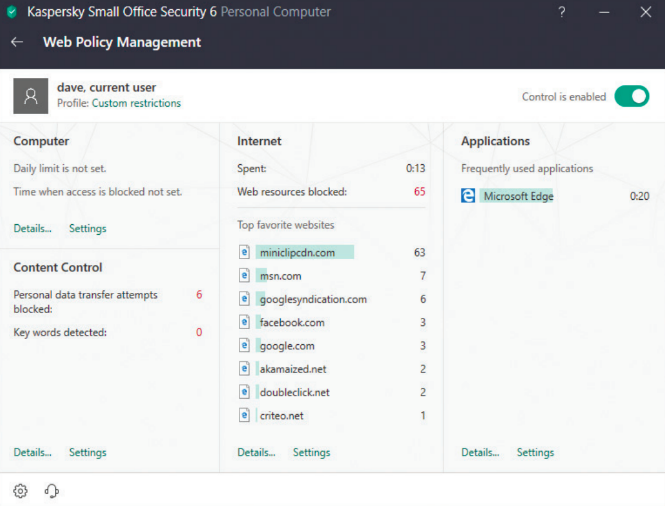
Kaspersky's web console lets you set up web-filtering policies
Finally, it's worth looking for antispam measures too. This isn't just about helping employees manage their inboxes; it can also filter out potentially dangerous phishing attacks. Don't expect perfect protection, though, as modern email fraud attacks often use clever social engineering tricks to fool both spam filters and unwary recipients. We recommend training your staff to recognise phishing attempts, and giving advice on how to handle and report them.
Safety in numbers
Business security is a multifaceted, multilayered thing, but a centralised solution can make it manageable even for small businesses. That's just as well, because the fallout from an incident could destroy your brand and even push you into insolvency. If you haven't already invested in a security solution, now's the time.
Small businesses can also get assistance from the government's Cyber Aware website (cyberaware.gov.uk), which provides help and advice about data security along with a link to report data breaches and fraud to the ActionFraud UK cyber crime centre.
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.
-
 Should AI PCs be part of your next hardware refresh?
Should AI PCs be part of your next hardware refresh?AI PCs are fast becoming a business staple and a surefire way to future-proof your business
By Bobby Hellard Published
-
 Westcon-Comstor and Vectra AI launch brace of new channel initiatives
Westcon-Comstor and Vectra AI launch brace of new channel initiativesNews Westcon-Comstor and Vectra AI have announced the launch of two new channel growth initiatives focused on the managed security service provider (MSSP) space and AWS Marketplace.
By Daniel Todd Published