BillQuick billing software exploit lets hackers deploy ransomware
The now-patched critical zero-day vulnerability also leaked sensitive data from the time and billing platform
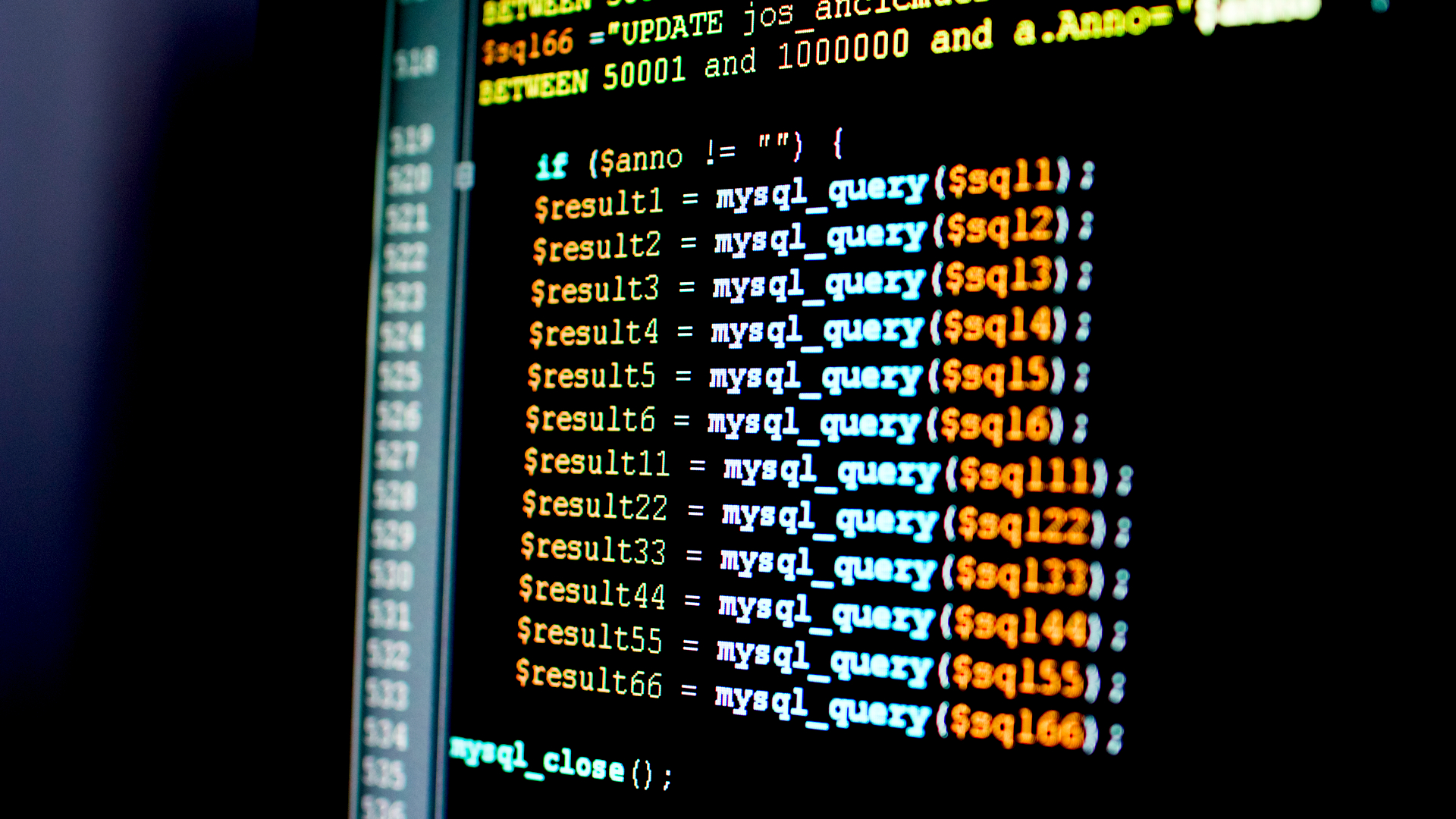

Hackers are exploiting a flaw in the BillQuick Web Suite, a time and billing system from BQE Software, to deploy ransomware.
According to a blog post by security researchers at Huntress, cyber criminals were able to exploit CVE-2021-42258 to gain initial access to a US engineering company and deploy ransomware across the victim’s network.
BQE Software has a user base of 400,000 users worldwide. At the time of writing, it's not known who the hackers behind the exploit are.
According to Caleb Stewart, a security researcher for Huntress Labs, researchers were first made aware of the issue when several ransomware “canary files” were tripped within an engineering company’s environment that was managed by one of Huntress’s partners. These files were set up to trigger alerts if they’re changed, moved, or deleted.
Further investigations found Microsoft Defender antivirus alerts indicating malicious activity as the MSSQLSERVER$ service account. This, according to Stewart, indicated the possibility of a web application being exploited to gain initial access.
“The server in question hosted BillQuick Web Suite 2020 (WS2020), and the connection logs indicated a foreign IP repeatedly sending POST requests to the web server logon endpoint, leading up to the initial compromise,” said Stewart.
The researchers suspected that a bad actor was attempting to exploit BillQuick, so then began a process of reverse engineering of the web application to trace the attacker’s steps. With a local copy of the app, researchers identified concatenated SQL queries.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
“Essentially, this function allows a user to control the query that’s sent to the MSSQL database - which in this case, enables blind SQL injection via the application’s main login form,” said Stewart.
Researchers were then able to recreate the victim’s environment and validate simple security tools like sqlmap easily obtained sensitive data from the BillQuick server without authentication.
RELATED RESOURCE

The best defence against ransomware
How ransomware is evolving and how to defend against it
“Because these versions of BillQuick used the sa (System Administrator) MSSQL user for database authentication, this SQL injection also allowed the use of the xp_cmdshell procedure to remotely execute code on the underlying Windows operating system,” said Stewart.
The firm has been in contact with BQE Software, which has since patched the flaw. It is still working with the company on “multipleother security concerns”.
Despite BQE Software’s cooperation, Stewart said other well-established vendors are doing “very little to proactively secure their applications and subject their unwitting customers to significant liability when sensitive data is inevitably leaked and/or ransomed”.
“In 2021, it’s still extremely common for vendors to sweep cyber security issues under the rug; we have the impression that BQE is taking our feedback seriously,” he added.
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published
-
 The complete guide to the NIST cybersecurity framework
The complete guide to the NIST cybersecurity frameworkWhitepaper Find out how the NIST Cybersecurity framework is evolving
By ITPro Published
-
 Are you prepared for the next attack? The state of application security in 2024
Are you prepared for the next attack? The state of application security in 2024Webinar Aligning to NIS2 cybersecurity risk-management obligations in the EU
By ITPro Published
-
 The economics of penetration testing for web application security
The economics of penetration testing for web application securitywhitepaper Get the most value from your security solution
By ITPro Published
-
 How to build your resilience against application layer threats
How to build your resilience against application layer threatsWhitepaper Addressing security threats with a consolidated cloud-based platform approach
By ITPro Published
-
 How applications are attacked
How applications are attackedwhitepaper A year in application security
By ITPro Published
-
 2022 Public Sector Identity Index Report
2022 Public Sector Identity Index ReportWhitepaper UK Report
By ITPro Published
-
 Businesses at work
Businesses at workWhitepaper Discussing the most popular apps and top performing apps of 2022, and the rise of Zero Trust security
By ITPro Published
-
 New app store code of practice aims to strengthen ecosystem cyber security
New app store code of practice aims to strengthen ecosystem cyber securityNews Developers and app store operators will be required to implement more robust security measures
By Ross Kelly Published