Critical macOS vulnerability found to bypass SIP restrictions
The flaw lies in how the OS handles software packages and post-installation scripts
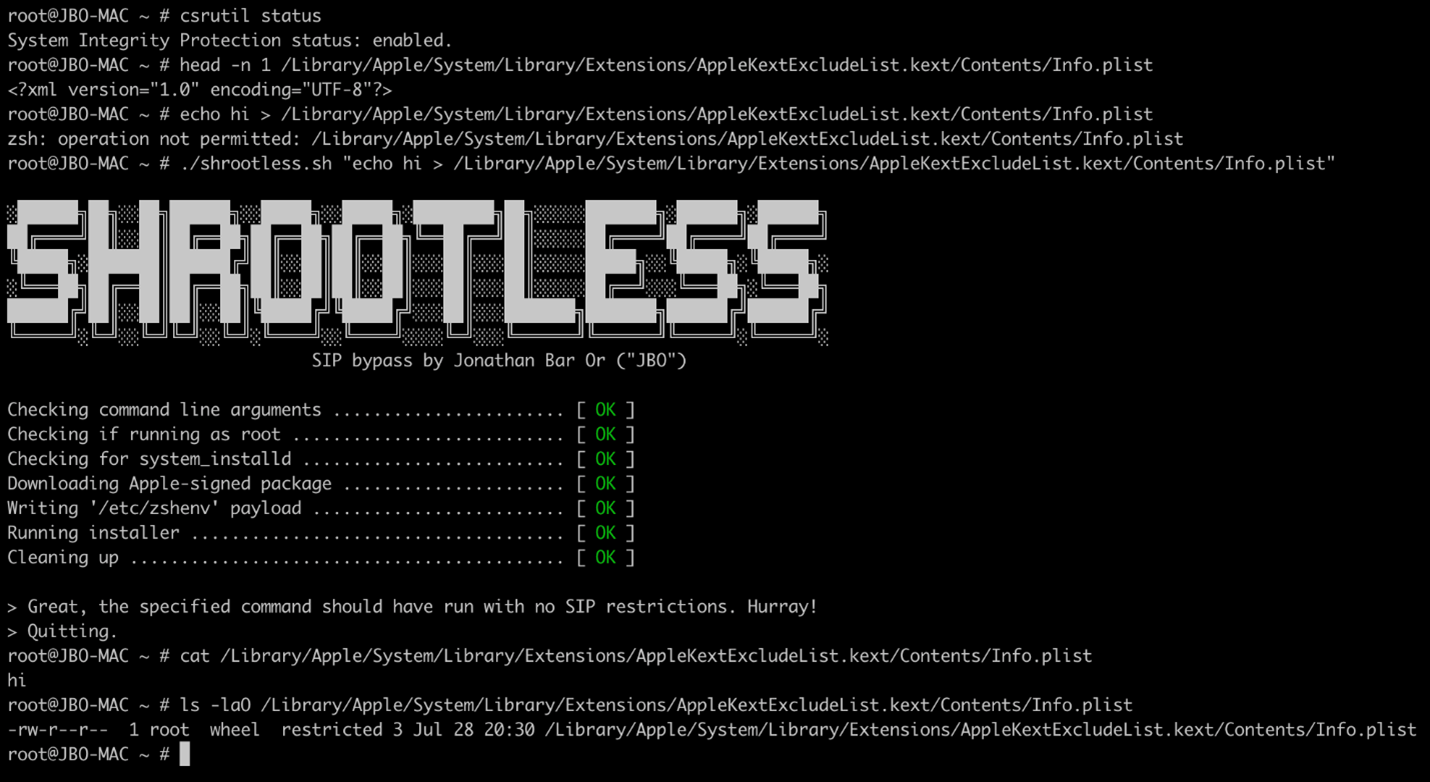

Security researchers at Microsoft have discovered a flaw in Apple’s macOS that can hackers could use to bypass the System Integrity Protection (SIP) feature and execute arbitrary code.
Dubbed Shrootless, the flaw has been identified as CVE-2021-30892 and was included in the security updates released by Apple on 26 October.
The flaw lies in how Apple signs the software package and how the post-installation scripts are installed in it. The researchers found that attackers can use this mechanism for malicious purposes by creating a custom package that can intercept the installation process. After SIP bypass, an attacker can install rootkits and undetectable malware, and even overwrite system files.
A design flaw means that in some cases software packages require access to directories protected by SIP, as is the case with system updates. Files with the extended attribute 'com.apple.rootless' are similarly SIP-protected. Of course, there’s no way to add that extended attribute to a file legitimately, otherwise malware could use SIP for its own protection.
While analyzing macOS processes to bypass SIP, researchers came across the 'system_installd' daemon with powerful 'com.apple.rootless.install.inheritable' rights. With these rights, any 'system_installd' child process can avoid all SIP-set file system restrictions.
RELATED RESOURCE

The top three IT pains of the new reality and how to solve them
Driving more resiliency with unified operations and service management
The researchers decided to examine all the child processes of 'system_installd' and were surprised to find several cases that allow hackers to abuse this functionality to bypass SIP.
For example, if an Apple-signed package (.pkg file) is installed, the package will start the 'system_installd' process, which is responsible for installing it. If the package contains any post-installation scripts, 'system_installd' starts them by initiating the default shell (on macOS, this is zsh).
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
It's important to note that after starting zsh, it then looks for the '/etc/zshenv' file and, if found, automatically runs commands from it, even in a non-interactive mode. Therefore, to perform arbitrary operations on the device, attackers can create a malicious '/etc/zshenv' file and then wait for 'system_installd' to invoke zsh.
Researchers said that the research underscores the importance of collaboration among security researchers, software vendors, and the larger security community.
“As cross-platform threats continue to increase, vulnerability discoveries, coordinated response, and other forms of threat intelligence sharing help enrich our protection technologies that secure users’ computing experience regardless of the platform or device they’re using,” said Jonathan Bar Or, senior security researcher at Microsoft’s 365 Defender Research Team.
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
-
 A journey to cyber resilience
A journey to cyber resiliencewhitepaper DORA: Ushering in a new era of cyber security
By ITPro
-
 A new framework for third-party risk in the European Union
A new framework for third-party risk in the European Unionwhitepaper Report: DORA and cyber risk
By ITPro
-
 Kali Linux releases first-ever defensive distro with score of new tools
Kali Linux releases first-ever defensive distro with score of new toolsNews Kali Purple marks the next step for the red-teaming platform on the project's tenth anniversary
By Rory Bathgate
-
 Microsoft releases scripts to restore shortcuts deleted in faulty Windows Defender update
Microsoft releases scripts to restore shortcuts deleted in faulty Windows Defender updateNews However, some users have resorted to creating their own fixes as they’ve encountered Microsoft’s to be problematic
By Zach Marzouk
-
 Windows Defender update deletes Start Menu, Taskbar, Desktop shortcuts
Windows Defender update deletes Start Menu, Taskbar, Desktop shortcutsNews For now, it appears that administrators will have to manually recreate their shortcuts once the issue has been fixed
By Zach Marzouk
-
 IBM LinuxONE for dummies
IBM LinuxONE for dummiesWhitepaper Secure your data, build an open hybrid cloud environment, and realise the cost benefits of consolidation
By ITPro
-
 Windows 10 users encounter ‘blue screen of death’ after latest Patch Tuesday update
Windows 10 users encounter ‘blue screen of death’ after latest Patch Tuesday updateNews Microsoft said it is working on a fix for the issue and has offered users a temporary workaround
By Ross Kelly
-
 Apple issues fix for ‘actively exploited’ WebKit zero-day vulnerability
Apple issues fix for ‘actively exploited’ WebKit zero-day vulnerabilityNews The update marks the 10th fix for zero-day vulnerabilities this year
By Ross Kelly

