Play ransomware gang behind recent cyber attack on Rackspace
Rackspace said that “more than half” of affected customers have regained access to data in the wake of the attack


Rackspace has revealed the Play ransomware gang was behind a December attack which took down the company’s hosted Microsoft Exchange email service.
In a status update published on Thursday evening, the cloud computing firm confirmed the ransomware group gained access to Personal Storage Tables (PST) belonging to 27 hosted exchange customers.
Rackspace insisted that, at present, there is no evidence to suggest that threat actors “viewed, obtained, misused, or disseminated” emails or data belonging to the hosted exchange customers.
“No other Rackspace products, platforms, solutions, or businesses were affected or experienced downtime due to this incident,” the firm said.
At the time of Rackspace’s update, the firm revealed that “more than half” of impacted customers have had “some or all of their data available to them to download”.
“This indicates to us that many of our customers have data backed up locally, archived, or otherwise do not need the historical data,” the company said.
“We will continue working to recover all data possible as planned, however, in parallel, we are developing an on-demand solution for those customers who do still wish to download their data. We expect that the on-demand solution will be available within two weeks.”
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Rackspace added that the hosted Exchange service will not return following the incident.
Rackspace cyber attack
Rackspace first informed customers that it had suffered a breach on 2 December. The attack caused an outage on the company's hosted Microsoft Exchange email service, disrupting affected customers who were left unable to access email services and recover contacts or previous correspondence.
A follow-up disclosure by the firm confirmed that a ransomware attack was to blame for the incident, and subsequently began migrating customers to cloud-based Microsoft 365 services.
Initial speculation suggested that the incident was the result of the ProxyNotShell exploit, Rackspace said. However, the company said it can now “definitively state” that this is not accurate.
An investigation by CrowdStrike found that Play harnessed a zero-day exploit associated with CVE-2022-41080, known as ‘OWASSRF’, as part of the attack.
RELATED RESOURCE

Automate security intelligence with IBM Security QRadar SIEM
Simplify and improve threat detection, investigation and response with reducing overheads
The OWASSRF zero-day exploits two vulnerabilities, tracked as CVE-2022-41080 and CVE-2022-41082, and enables threat actors to achieve remote code execution (RCE) through Outlook Web Access.
According to CrowdStrike, this method “bypasses URL rewrite mitigations for the Autodiscover endpoint provided by Microsoft in response to ProxyNotShell”.
“Microsoft disclosed CVE-2022-41080 as a privilege escalation vulnerability and did not include notes for being part of a remote code execution chain that was exploitable,” Rackspace added in its update.
CrowdStrike said it discovered this new exploit on the back of an extensive investigation into recent Play ransomware attacks that targeted Microsoft Exchange.
What is Play ransomware?
The Play ransomware group is a relative newcomer to the global cyber crime space. Also known as PlayCrypt, the group is believed to have launched in June 2022 and has already caused significant disruption to a host of major organisations.
The group previously claimed responsibility for an attack on German hotel chain, H-Hotels, and earlier this week the group said it was responsible for an attack on the State of New York (SUNY) Polytechnic.
The attack is thought to be the first major ransomware attack on the education sector so far in 2023, and led to the exposure of sensitive data such as passport information, confidential contracts, and student IDs.
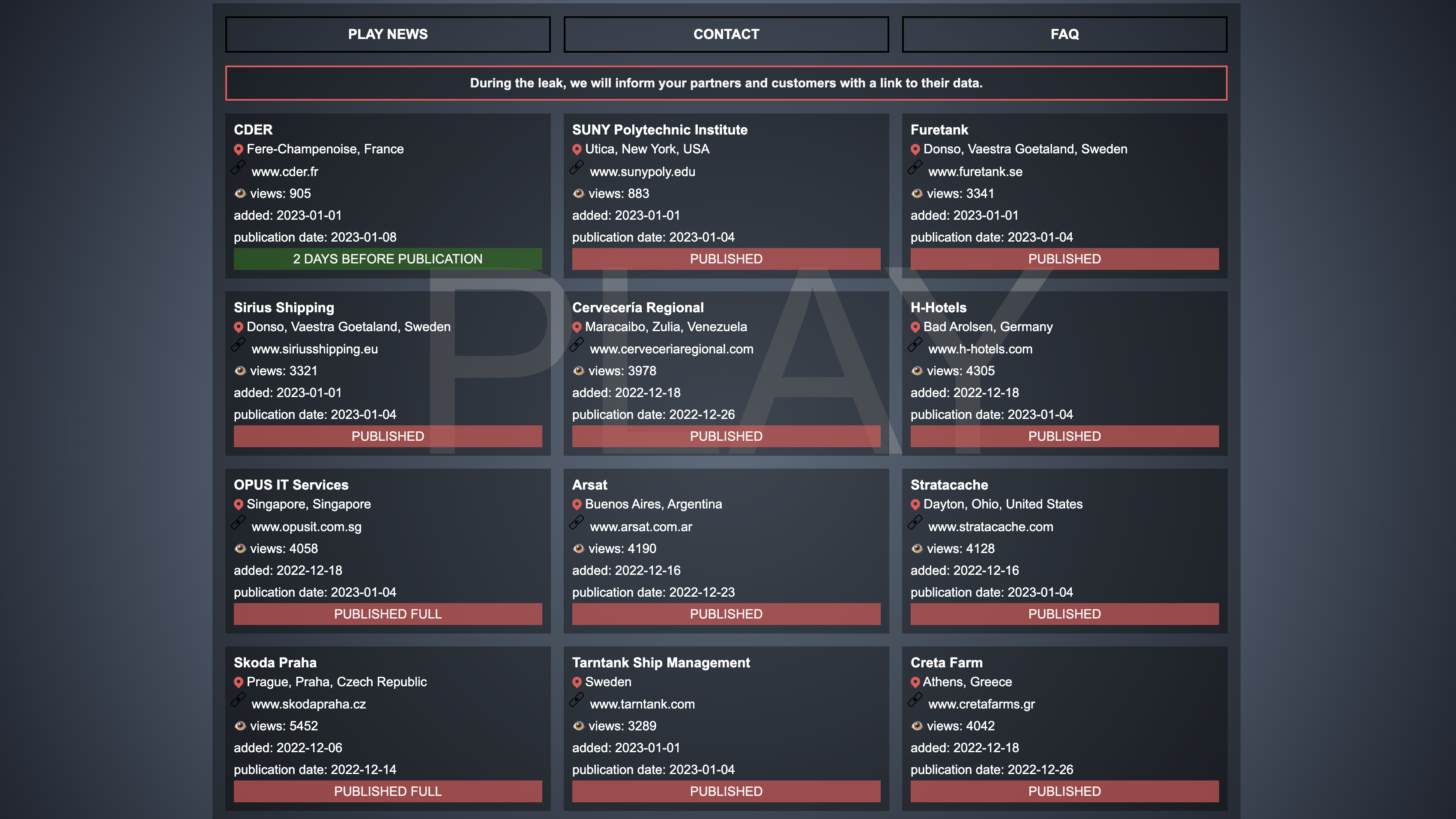
According to research from Avertium, Play has primarily targeted organisations across Latin America, but has also been observed deploying attacks on India, Hungary, Spain, and the Netherlands.
“Play is known for their big game hunting tactics, such as using Cobalt Strike for post-compromise and SystemBC RAT for persistence,” Avertium said in a blog post. “They have recently started exploiting the ProxyNotShell vulnerabilities in Microsoft Exchange.
“The group also has similar tactics and techniques to the ransomware groups Hive and Nokoyawa, leading researchers to believe Play is operated by the same people.”

Ross Kelly is ITPro's News & Analysis Editor, responsible for leading the brand's news output and in-depth reporting on the latest stories from across the business technology landscape. Ross was previously a Staff Writer, during which time he developed a keen interest in cyber security, business leadership, and emerging technologies.
He graduated from Edinburgh Napier University in 2016 with a BA (Hons) in Journalism, and joined ITPro in 2022 after four years working in technology conference research.
For news pitches, you can contact Ross at ross.kelly@futurenet.com, or on Twitter and LinkedIn.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published
-
 ‘Phishing kits are a force multiplier': Cheap cyber crime kits can be bought on the dark web for less than $25 – and experts warn it’s lowering the barrier of entry for amateur hackers
‘Phishing kits are a force multiplier': Cheap cyber crime kits can be bought on the dark web for less than $25 – and experts warn it’s lowering the barrier of entry for amateur hackersNews Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published
-
 Healthcare systems are rife with exploits — and ransomware gangs have noticed
Healthcare systems are rife with exploits — and ransomware gangs have noticedNews Nearly nine-in-ten healthcare organizations have medical devices that are vulnerable to exploits, and ransomware groups are taking notice.
By Nicole Kobie Published
-
 Alleged LockBit developer extradited to the US
Alleged LockBit developer extradited to the USNews A Russian-Israeli man has been extradited to the US amid accusations of being a key LockBit ransomware developer.
By Emma Woollacott Published
-
 February was the worst month on record for ransomware attacks – and one threat group had a field day
February was the worst month on record for ransomware attacks – and one threat group had a field dayNews February 2025 was the worst month on record for the number of ransomware attacks, according to new research from Bitdefender.
By Emma Woollacott Published
-
 CISA issues warning over Medusa ransomware after 300 victims from critical sectors impacted
CISA issues warning over Medusa ransomware after 300 victims from critical sectors impactedNews The Medusa ransomware as a Service operation compromised twice as many organizations at the start of 2025 compared to 2024
By Solomon Klappholz Published
-
 Warning issued over prolific 'Ghost' ransomware group
Warning issued over prolific 'Ghost' ransomware groupNews The Ghost ransomware group is known to act fast and exploit vulnerabilities in public-facing appliances
By Solomon Klappholz Published
-
 The Zservers takedown is another big win for law enforcement
The Zservers takedown is another big win for law enforcementNews LockBit has been dealt another blow by law enforcement after Dutch police took 127 of its servers offline
By Solomon Klappholz Published
-
 There’s a new ransomware player on the scene: the ‘BlackLock’ group has become one of the most prolific operators in the cyber crime industry – and researchers warn it’s only going to get worse for potential victims
There’s a new ransomware player on the scene: the ‘BlackLock’ group has become one of the most prolific operators in the cyber crime industry – and researchers warn it’s only going to get worse for potential victimsNews Security experts have warned the BlackLock group could become the most active ransomware operator in 2025
By Solomon Klappholz Published