Ukraine's vigilante IT army now has a DDoS bot to automate attacks against Russia
The 270,000-strong IT Army of Ukraine will now combine supporters' cloud infrastructure to strengthen the daily attacks against their invaders


Ukraine’s unofficial ‘army’ of IT vigilantes has developed a new automated attack tool to increase the effectiveness of its cyber attacks against Russian domains.
Its “attack automation bot” was built to help more people easily launch distributed denial of service (DDoS) cyber attacks against Russia. The new tool encourages individuals to donate their cloud resources to the bot, which is capable of launching a “coordinated attack from all the available servers”.
“To run all our attacks at the same time we recommend to use our new DDoS bot,” the group said on its website. “All you need is [to] send credentials to your servers to our bot and check how [the] attack is going via Telegram bot.”
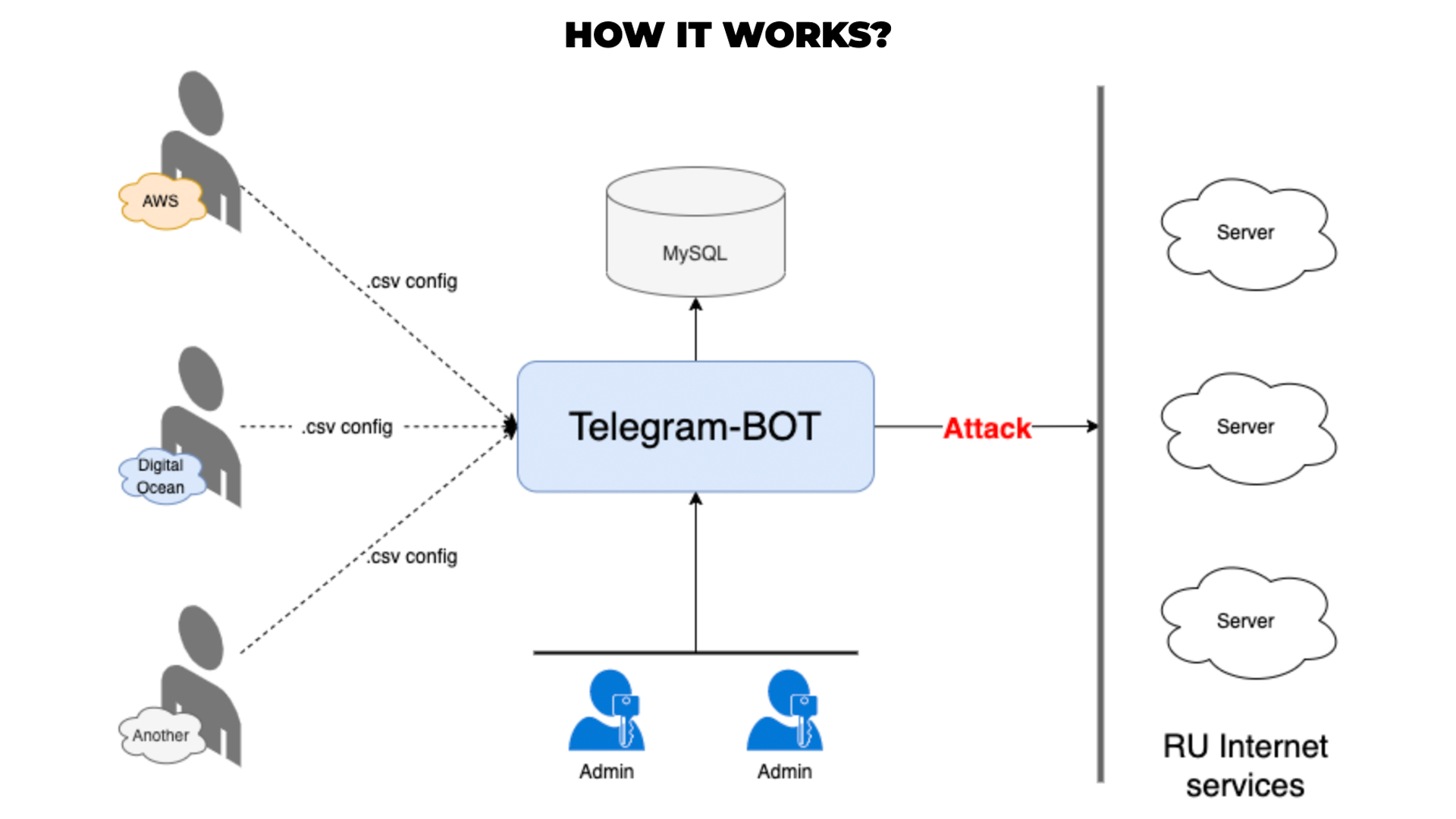
Should they wish to, supporters are also encouraged to purchase and share the credentials of new servers that can be bought for the sole purpose of strengthening the botnet's attack.
The organised group of cyber-savvy individuals who want to actively support Ukraine from afar has been growing in number since the start of the conflict. The group is assembled on Telegram and currently has more than 270,000 members.
The group’s members are fed instructions by leaders on a daily basis, complete with IP addresses, specific ports, and web domains that need to be targeted to disrupt the Russian regime as the war continues.
Past targets have included media organisations, banks, airlines, and app stores.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Russian cyber attacks against Ukraine have been large and sustained, starting weeks before the conflict broke out.
The Five Eye intelligence alliance confirmed last week that it believed with a high degree of confidence that Russia was behind the attacks on Ukraine in the early stages of the war.
The attacks on Ukrainian government websites in January, which also involved the use of the destructive Whispergate ‘wiper’ malware, were attributed to Russia’s military intelligence service, the GRU, as was the 24 February attack on communications company Viasat.
RELATED RESOURCE

The Total Economic Impact™ of Mimecast
Cost savings and business benefits enabled by using Mimecast with Microsoft 365
FREE DOWNLOAD
The attack on Viasat was conducted one hour before the Russia invasion of Ukraine became official and it was later revealed to have had effects in wider Europe, as wind farms and individual internet users outside of Ukraine also suffered outages.
The collateral effects of the Viasat attack were the most visceral examples of the ‘spillover effects’ many experts believed would affect Europe in the ongoing war between Russia and Ukraine in cyber space.
Russia has a history of launching devastating attacks on Ukraine dating back many years. Some of the most significant incidents have involved the use of Petya malware and repeated targeting of the country’s power grid, firstly in 2015, then again in 2016, and most recently in April 2022.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Europol hails triple takedown with Rhadamanthys, VenomRAT, and Elysium sting operations
Europol hails triple takedown with Rhadamanthys, VenomRAT, and Elysium sting operationsNews The Rhadamanthys infostealer operation is one of the latest victims of Europol's Operation Endgame, with more than a thousand servers taken down
-
 Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up sting
Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up stingNews Europol has detained several people believed to be involved in a botnet operation as part of a follow-up to a major takedown last year.
-
 Horabot campaign targeted businesses for more than two years before finally being discovered
Horabot campaign targeted businesses for more than two years before finally being discoveredNews The newly-discovered Horabot botnet has attacked companies in the accounting, investment, and construction sectors in particular
-
 UK crime fighters wrangle “several thousand” potential cyber criminals in DDoS-for-hire honeypot
UK crime fighters wrangle “several thousand” potential cyber criminals in DDoS-for-hire honeypotNews The sting follows a recent crackdown on DDoS-for-hire services globally
-
 Brand-new Emotet campaign socially engineers its way from detection
Brand-new Emotet campaign socially engineers its way from detectionNews This latest resurgence follows a three-month hiatus and tricks users into re-enabling dangerous VBA macros
-
 US begins seizure of 48 DDoS-for-hire services following global investigation
US begins seizure of 48 DDoS-for-hire services following global investigationNews Six people have been arrested who allegedly oversaw computer attacks launched using booters
-
 Microsoft says “it’s just too difficult” to effectively disrupt ransomware
Microsoft says “it’s just too difficult” to effectively disrupt ransomwareNews The company details its new approach to combatting cyber crime as the underground industry drains $6 trillion from the global economy
-
 Will triple extortion ransomware truly take off?
Will triple extortion ransomware truly take off?In-depth Operators are now launching attacks with three extortion layers, but there are limitations to this model

