What is the LAPSUS$ group and who is behind the criminal operation?
The most prolific cyber criminals of 2022 have largely evaded identification for months despite being anything but secretive in the way they work


The LAPSUS$ hacking group has arguably been the most prolific threat to cyber security in 2022, with numerous high-profile businesses admitting to breaches at the hands of the newcomers.
The likes of Nvidia, LG, Microsoft, Okta, and T-Mobile are among the most notable victims of LAPSUS$ in the space of just three months, and up until late March, very little has been known about the mysterious collective.
Unlike most of the ‘successful’ hackers in recent times, LAPSUS$ is unique in that it doesn't operate on a ransomware model, deploying other tactics to extort victims through financially motivated campaigns. Since the most recent supply chain attack on identity and access business Okta, the group has announced that it will be taking a hiatus, but the inner workings of LAPSUS$ will be studied by cyber criminals long after the group ends for good.
Who is behind LAPSUS$?
Perhaps the biggest uncertainty when it comes to analysing LAPSUS$ is identifying who is behind the cyber criminal organisation. Onlookers have been left perplexed by the group that appears to be both “competent and incompetent at the same time,” according to security expert Marcus Hutchins.
On one hand, the group has claimed numerous high-profile scalps that even the most experienced cyber criminals would be proud to hang from their mantle. But the group also displays a gung-ho approach to operational security. Rather than hiding in the shadows, it advertises its activity for all to see via a public Telegram channel and even offers channel members a way to vote on which company’s data is leaked next.
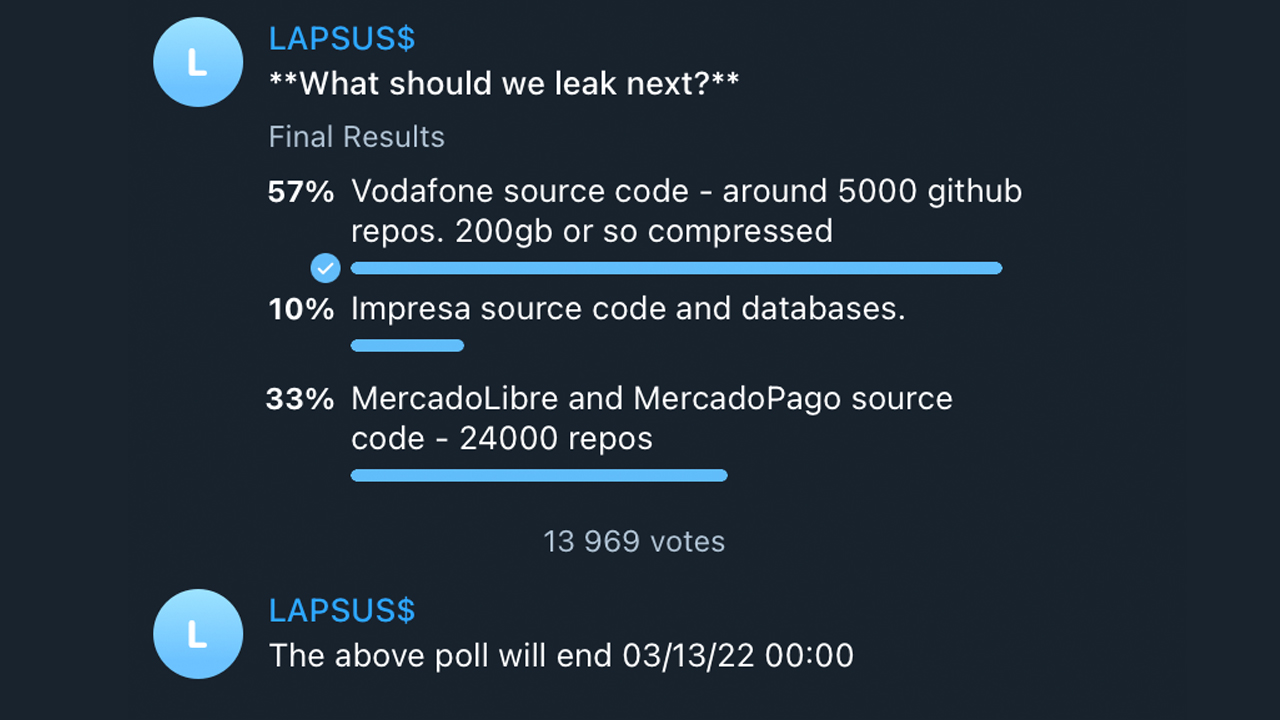
“They appear to be kids but are claiming responsibility for hacking top tier companies,” said Hutchins – a thought echoed by independent security researcher Bill Demirkapi who said the group “appear to be incredibly inexperienced with OPSEC. They posted their message boasting about access to Microsoft's internal DevOps environment while still exfiltrating source code”.
Researchers at Check Point said the LAPSUS$ hackers are Portuguese and are from Brazil, saying that its first major breach was in December 2021, the month in which the operation started, and targeted Brazil’s Ministry of Health and other government agencies.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
RELATED RESOURCE

Ransomware and Microsoft 365 for business
What you need to know about reducing ransomware risk
A separate breaking report from Bloomberg suggested the entire operation is being led by a 16-year-old based in Oxfordshire, UK, with other members also being based in the UK and Brazil.
UK law enforcement made seven arrests on 24 March in connection with the LAPSUS$ group and the City of London Police wouldn't immediately confirm if the 16-year-old was included. The seven arrests included individuals aged between 16 and 21; they were all released at the time, pending further investigations.
UK police confirmed on 2 April that two individuals have been charged in connection to the hacking group that breached the plethora of tech giants - both appeared in Highbury Corner Magistrates Court.
A 16-year-old and a 17-year-old were charged with several offences, including three counts of unauthorised access with intent to impair operation of, or hinder, access to a computer, and two counts of fraud by false representation, the BBC reported.
The younger defendant was also charged with one count of causing a computer to perform a function to secure unauthorised access to a program.
Both teenagers have been released on bail and many of their details cannot be revealed due to reporting restrictions activated because of their ages, though both are confirmed as males.
The arrests come days after LAPSUS$ made public details of its most recent hack, a major breach involving software company Globant. The hack involved the leaking of source code for mobile apps belonging to the likes of Facebook, DHL, Abbott, AB InBev, and more.
The hack was announced by the group on 30 March, one week after the group said that some of its members were taking a leave of absence, going on “vacation” and six days after the original arrests were made.
Prosecutor for the case Valerie Benjamin said the case should be heard in the Crown Court due to its complex nature and the large sums of money involved in the extortion group.
How does LAPSUS$ operate?
RELATED RESOURCE
A breakthrough piece of research published by Microsoft in March 2022 detailed the company’s investigation into the group, uncovering the inner workings of how it operates and how it was able to breach some of the biggest organisations on the planet.
Microsoft did not refer to who was behind the group or where it was based but said LAPSUS$ was a large-scale social engineering and extortion campaign, operating on a pure extortion and destruction model.
The seemingly juvenile perception of the group juxtaposes its doubtless expertise and sophistication in carrying out attacks. Microsoft said the attack methods used by LAPSUS$ were varied, elaborate, and some were used less frequently than other, more mature threat actors.
Social engineering and initial access
The social engineering tactics displayed by LAPSUS$ gave the “hackers intimate knowledge” of employees and companies, Microsoft said. The goal of the group is to gain elevated access to businesses through stolen credentials that enable data theft and destructive attacks, often with a corporate extortion element.
The group was observed calling help desks, convincing them to reset account credentials after studying how they work, and dropping into crisis communication channels on platforms like Slack and Teams. This required the hackers to breach a company to understand how they respond to a security incident, responding in a way that helped them evade detection.
LAPSUS$ achieves initial access through a variety of methods, including deploying the Redline password stealer and searching public code repositories for exposed credentials. It has also been found to have bought business credentials, perhaps through initial access brokers - an observation corroborated by ransomware gang Arvin Club. In other cases, LAPSUS$ simply paid company employees directly for access, a tactic it openly advertised on Telegram.
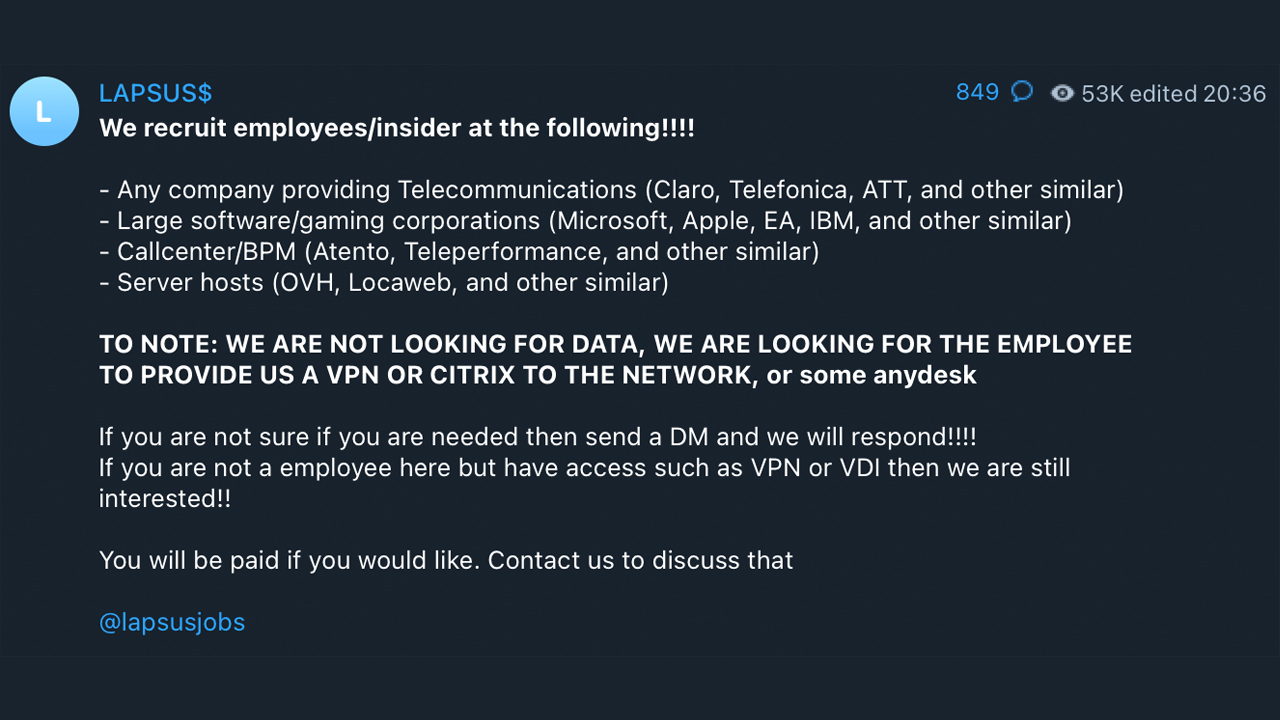
Cyber criminals use remote desktop protocol (RDP) and virtual desktop infrastructure (VDI) such as Citrix to remotely access a business environment.
LAPSUS$ bypasses multi-factor authentication (MFA) using techniques such as session token replay and spamming genuine account holders with MFA prompts after stealing their passwords.
The group said in a Telegram chat channel that spamming MFA prompts while employees are sleeping is likely to get people to approve the attempts to shut off the notifications.
Harvesting data and extortion tactics
Microsoft said LAPSUS$ also used virtual private networks (VPNs) intelligently and in a way that demonstrated the criminals understood how cloud monitoring services detect suspicious activity. For example, it said LAPSUS$ chose local egress points to prevent impossible travel alerts from being triggered.
The group also created virtual machines on victims’ cloud infrastructure to launch further attacks before locking the business out of its cloud platform entirely. Once LAPSUS$ achieved total control, it would ensure all of the organisation's inbound and outbound email was forwarded to its infrastructure, where it would harvest as much data as it could before deleting systems and resources. At this point, in some cases, Microsoft said LAPSUS$ would then either extort the victims to prevent the release of the data or simply post it online publicly.
LAPSUS$’s lucrative rewards
An unverified analysis of what is thought to be one of the wallet addresses associated with the LAPSUS$ group, by cyber security researchers Soufiane Tahiri and Anis Haboubi, has revealed a total revenue of 3,790.62159317 in Bitcoin (£123.9 million).
The finding has not been confirmed by LAPSUS$ or any other entity involved in investigations into the group, although the details of the group’s cryptocurrency wallet address were made available to members of its Telegram chat channel.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.

