Russia-linked state-sponsored hackers launch fresh attacks by abusing latest red team tool
Researchers said the new tool has evaded the detection of many leading security products and is quickly growing in popularity


Security researchers have discovered hackers abusing the latest penetration testing tool in active attacks on global targets.
Unit 42 experts said that a malicious payload associated with the Brute Ratel C4 (BRc4) red teaming tool goes undetected by many major security products and has been sued against organisations in North and South America.
The packaging of the malicious payload is consistent with the tactics deployed by advanced persistent threat group 29 (APT29) - otherwise known as ‘Cozy Bear’ - a Russian-linked state-sponsored hacking group known for the notorious SolarWinds attack in 2020.
The BRc4 tool has been around since 2020 with India-based security engineer Chetan Nayak, who previously worked for red teams at leading western security vendors, recently commercialising the product.
Nayak has said the pentesting tool was built after reverse-engineering several major security products, while Unit 42 said BRc4 is newer but no less capable than the more commonly abused Cobalt Strike.
“Overall, we believe this research is significant in that it identifies not only a new red team capability that is largely undetectable by most cyber security vendors, but more importantly, a capability with a growing user base that we assess is now leveraging nation-state deployment techniques,” Unit 42 said.
“We encourage all security vendors to create protections to detect activity from this tool and all organisations to be on alert for activity from this tool.”
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
After first being uploaded to VirusTotal in May 2022, the malicious payload slipped under the detection of 56 different security vendors that evaluated it, assigning it ‘benign’ status, Unit 42 said, showing how effective Nayak’s reverse engineering efforts have been.
Method of delivery
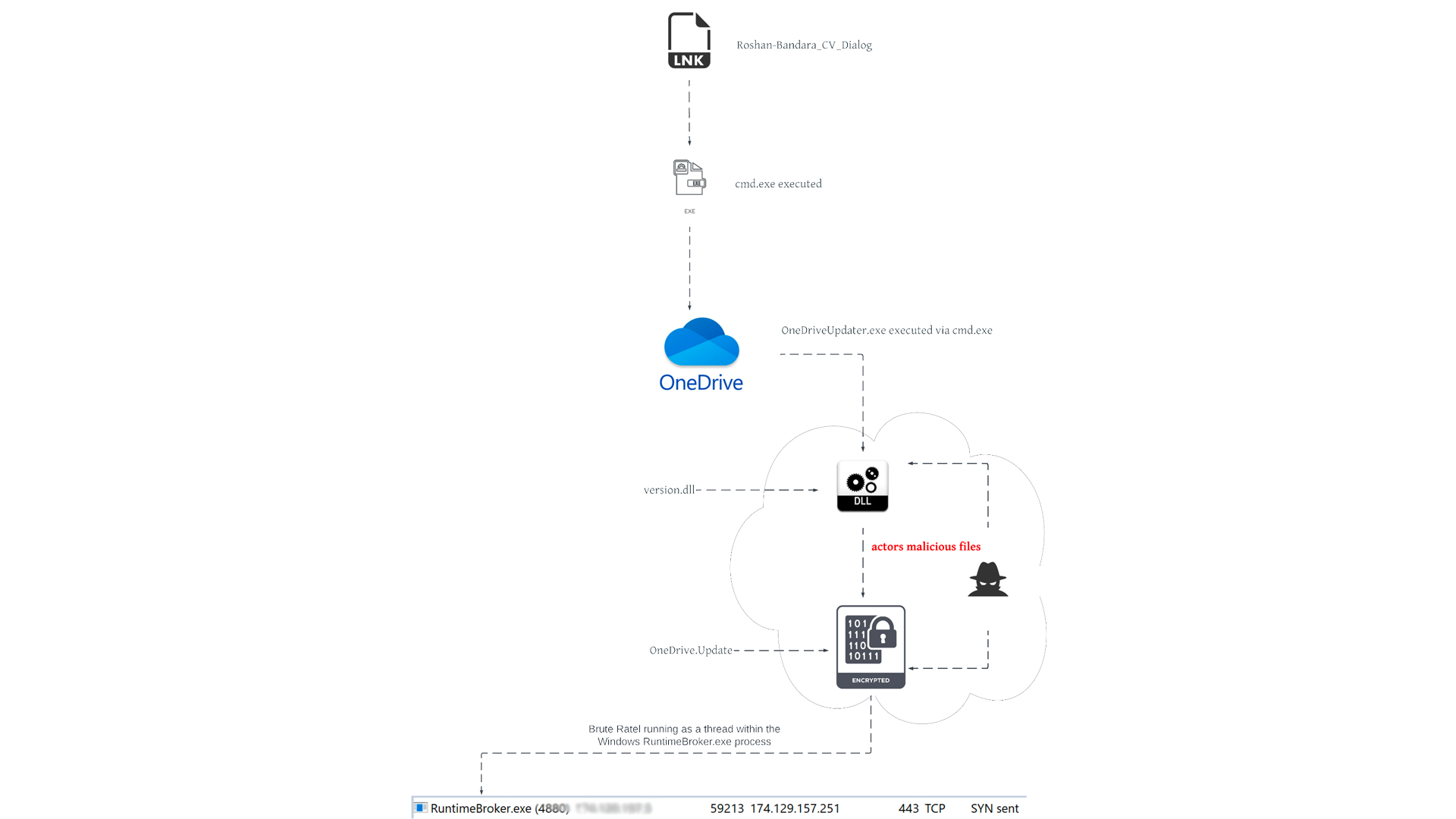
The malicious file is packaged up as a self-contained, benign ISO file and included in the ISO is the lure file - a Windows shortcut (LNK) file masquerading as a Word document, complete with a fake word doc file icon, and seemingly being a CV for a Roshan Bandara.
This is the actual malicious file, hidden inside the ISO which slipped through security vendors’ detections. It appears on a user’s hard drive after the ISO is double-clicked and mounted as a Windows drive. When the lure file is opened-clicked, BRc4 would be installed.
RELATED RESOURCE

This file is typically sent to victims through spear-phishing campaigns or downloaded to the victim by a second-stage downloader, Unit 42 said.
“While we lack insight into how this particular payload was delivered to a target environment, we observed connection attempts to the C2 server originating from three Sri Lankan IP addresses between May 19-20,” said the researchers.
In the same folder where the lure file is stored, other archived .exe and .dll files are present but hidden to most Windows users thanks to the operating system’s (OS) default configuration.
BRc4’s capabilities
Once installed, BRc4 advertises itself as having a broad range of capabilities. These were designed for legitimate use in red team-blue team exercises, but like Cobalt Strike, the powerful tools are often abused by black hat hackers in malicious cyber attacks.
Some of the tool’s capabilities include:
- SMB and TCP payloads provide the functionality to write custom external C2 channels over legitimate websites such as Slack, Discord, Microsoft Teams, and more
- Ability to keep memory artefacts hidden from EDRs and AV
- Take screenshots
- x64 shellcode loader
- Reflective and object file loader
- Patching Anti Malware Scan Interface (AMSI)
- Create Windows system services
- Upload and download files
Unit 42 also said the C2 infrastructure used by the threat actors abusing BRc4 is consistent with the methods used by APT29, using popular cloud storage and collaboration platforms.
The sample analysed by the researchers found the payload ‘calling home’ to an AWS-registered IP address located in the US over port 443. The X.509 certificate on the listening port was also self-signed and set up to impersonate a Microsoft security team.
A Ukrainian IP address was also used to administer the C2 infrastructure, and researchers believed that the attackers harnessed a residential network for this.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published
-
 Bugcrowd’s new MSP program looks to transform pen testing for small businesses
Bugcrowd’s new MSP program looks to transform pen testing for small businessesNews Cybersecurity provider Bugcrowd has launched a new service aimed at helping MSP’s drive pen testing capabilities - with a particular focus on small businesses.
By Ross Kelly Published
-
 Building a new approach to security with the next generation of penetration testing
Building a new approach to security with the next generation of penetration testingSponsored Combining human-led testing with continuous automated scanning can elevate your security regime
By ITPro Published
-
 OpenAI to pay up to $20k in rewards through new bug bounty program
OpenAI to pay up to $20k in rewards through new bug bounty programNews The move follows a period of unrest over data security concerns
By Ross Kelly Published
-
 Kali Linux releases first-ever defensive distro with score of new tools
Kali Linux releases first-ever defensive distro with score of new toolsNews Kali Purple marks the next step for the red-teaming platform on the project's tenth anniversary
By Rory Bathgate Published
-
 Podcast transcript: Meet the cyborg hacker
Podcast transcript: Meet the cyborg hackerIT Pro Podcast Read the full transcript for this episode of the IT Pro Podcast
By IT Pro Published
-
 The IT Pro Podcast: Meet the cyborg hacker
The IT Pro Podcast: Meet the cyborg hackerIT Pro Podcast Resistance is futile - offensive biotech implants are already here
By IT Pro Published
-
 Train firm slammed over 'bonus' phishing test
Train firm slammed over 'bonus' phishing testNews Security experts suggest businesses use other 'lures' to avoid upsetting workers in the current climate
By Bobby Hellard Published
-
 Taking a proactive approach to cyber security
Taking a proactive approach to cyber securityWhitepaper A complete guide to penetration testing
By ITPro Published