Pro-Russia Killnet hackers claim DDoS attack on EU Parliament website
The attack was launched shortly after MEPs voted to brand Russia a state-sponsor of terrorism for its invasion of Ukraine


Russian-aligned hackers have claimed responsibility for a cyber attack on the European Parliament's website on Wednesday.
The website was forced offline for around two hours after the pro-Russia Killnet hacking group launched a distributed denial of service (DDoS) attack against it - an attack method the group has widely adopted in its ongoing efforts to target pro-Ukrainian authorities.
RELATED RESOURCE
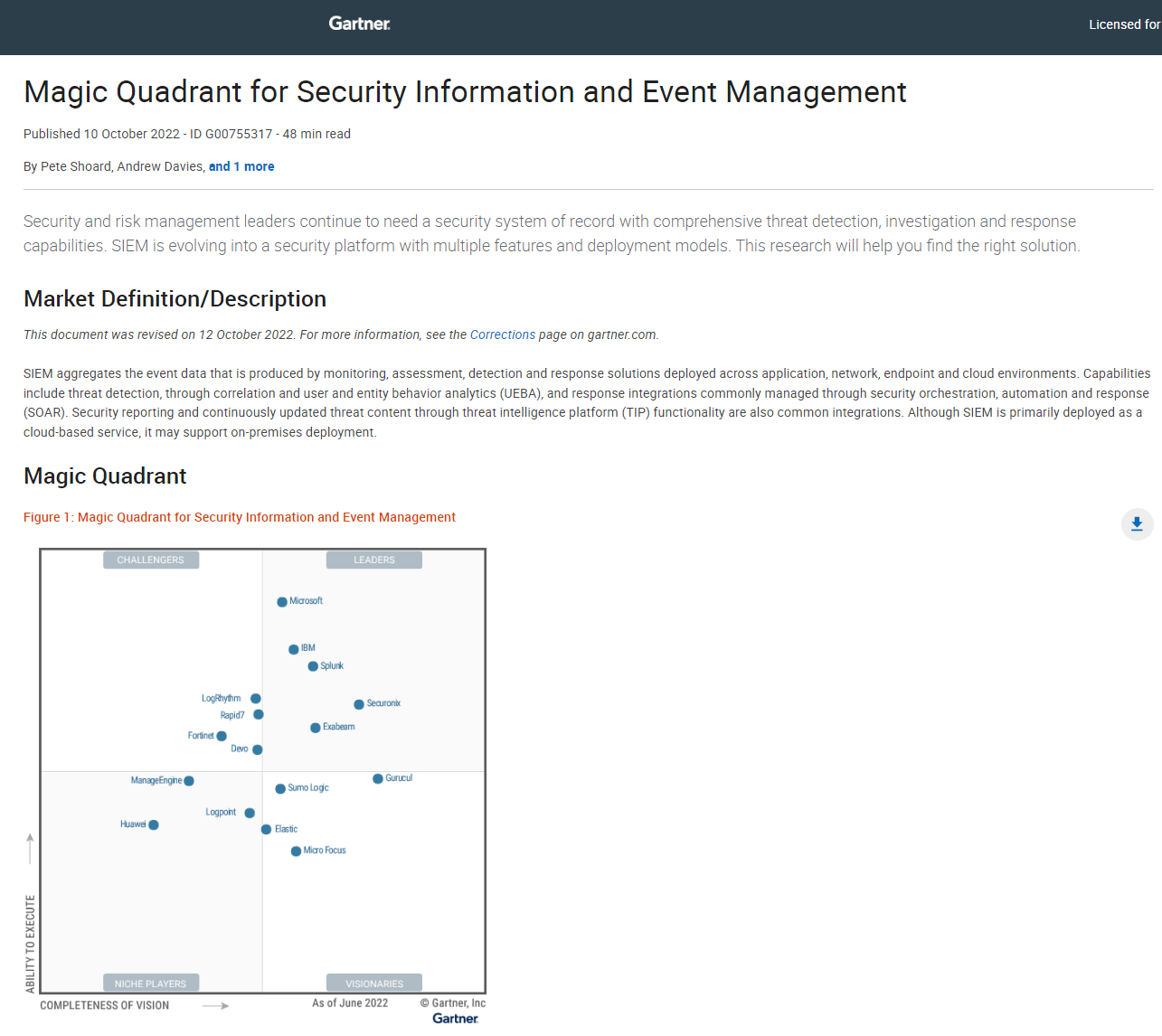
2022 Magic quadrant for Security Information and Event Management (SIEM)
SIEM is evolving into a security platform with multiple features and deployment models
The attack came just after members of the parliament voted to designate Russia as a state sponsor of terrorism following its invasion of Ukraine.
European Parliament President Roberta Metsola said in a tweet at the time that the website was facing "a sophisticated cyberattack”.
“A pro-Kremlin group has claimed responsibility. Our IT experts are pushing back against it and protecting our systems. This, after we proclaimed Russia as a state-sponsor of terrorism,” she added. “My response: #SlavaUkraini.”
Yesterday, politicians voted to declare Russia a state sponsor of terrorism, however, this is largely a token gesture as it doesn’t have legal powers to enforce this decision.
"The deliberate attacks and atrocities committed by Russian forces and their proxies against civilians in Ukraine, the destruction of civilian infrastructure and other serious violations of international and humanitarian law amount to acts of terror and constitute war crimes," said a statement from the European Parliament.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Killnet claimed responsibility for the attack via its Telegram channel. "Strap-on shelling of the server part of the official website of the European Parliament!" one message read.
"It cannot be understated the ease with which Killnet are able to launch these relatively low-sophistication attacks and make global headlines," said Justin Fier, vice president of tactical risk and response at Darktrace. "The group has no shortage of ‘reservists’ who they can call up to launch such an attack as part of their so-called ‘hacktivism’ – as seen in attacks on JP Morgan and the Lithuanian government earlier this year. The process for launching an attack such as this for one of their affiliates can be as simple as entering a URL into their attack tool software and hitting ‘run’.
“DDoS attacks, which are often fairly easy to recover from, are Killnet’s modus operandi, which the group use to make a political statement and cause reputational damage rather than cause any kind of financial harm. We must be careful in pointing the finger at the Russian state – cyber attribution and deciphering the extent of state-level tasking is difficult, with blurred lines between state-aligned, state-involved and state-directed increasing the risk of escalation, collateral and misattribution. Nonetheless, it does mount valid concerns that these citizen-led operations could become more destructive or that states could use these groups as a deniable proxy."
Killnet has risen to prominence in the past year since the war in Ukraine began and has claimed a number of attacks on various organisations and authorities that are against Russia's objectives.
Italy has been a particular focus of the group and the country has been the target of a large number of attacks against organisations within it over the past few months.
In May, Killnet carried out a spate of attacks on organisations that had links to Italy and in June, also attacked the Italian municipality of Palermo in an incident believed to have involved ransomware.
In August, Estonia successfully withstood and survived its "most extensive cyber attack since 2007" soon after it removed Soviet monuments from a region dominated by ethnic Russians, an attack that was also attributed to Killnet.
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published