Microsoft Authenticator mandates number matching to counter MFA fatigue attacks
The added layer of complexity aims to keep social engineering at bay


Microsoft Authenticator will now enforce number matching for all push notifications to make multi-factor authentication (MFA) less susceptible to social engineering attacks.
High-profile cyber criminals have seen success exploiting MFA fatigue attacks. These involve sending a barrage of MFA push notification requests to organizations’ staff, often at unsociable hours, to manipulate them into authenticating a login attempt just to clear the frustrating notifications.
Number matching involves opening a push notification, launching Microsoft Authenticator, and entering a series of numbers that appear in the app in order to approve the login attempt.
The technique has been around for years and marries the authentication methods of MFA and two-factor authentication (2FA).
These numbers usually reset after a given time period, like 30 seconds, and add an additional layer of interaction to help reduce the risk of successful social engineering attacks.
In a typical attack scenario, recipients of the constant notifications are often asleep and wake up to a series of loud alerts from their smartphone.
Half asleep, the attack can see success when staff simply approve login attempts so they can get back to sleep, for example.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Adding another manual layer increases the difficulty in quickly approving requests, making the process more manual and potentially allowing more time for the recipient to realize that the event is being triggered by a bad actor.
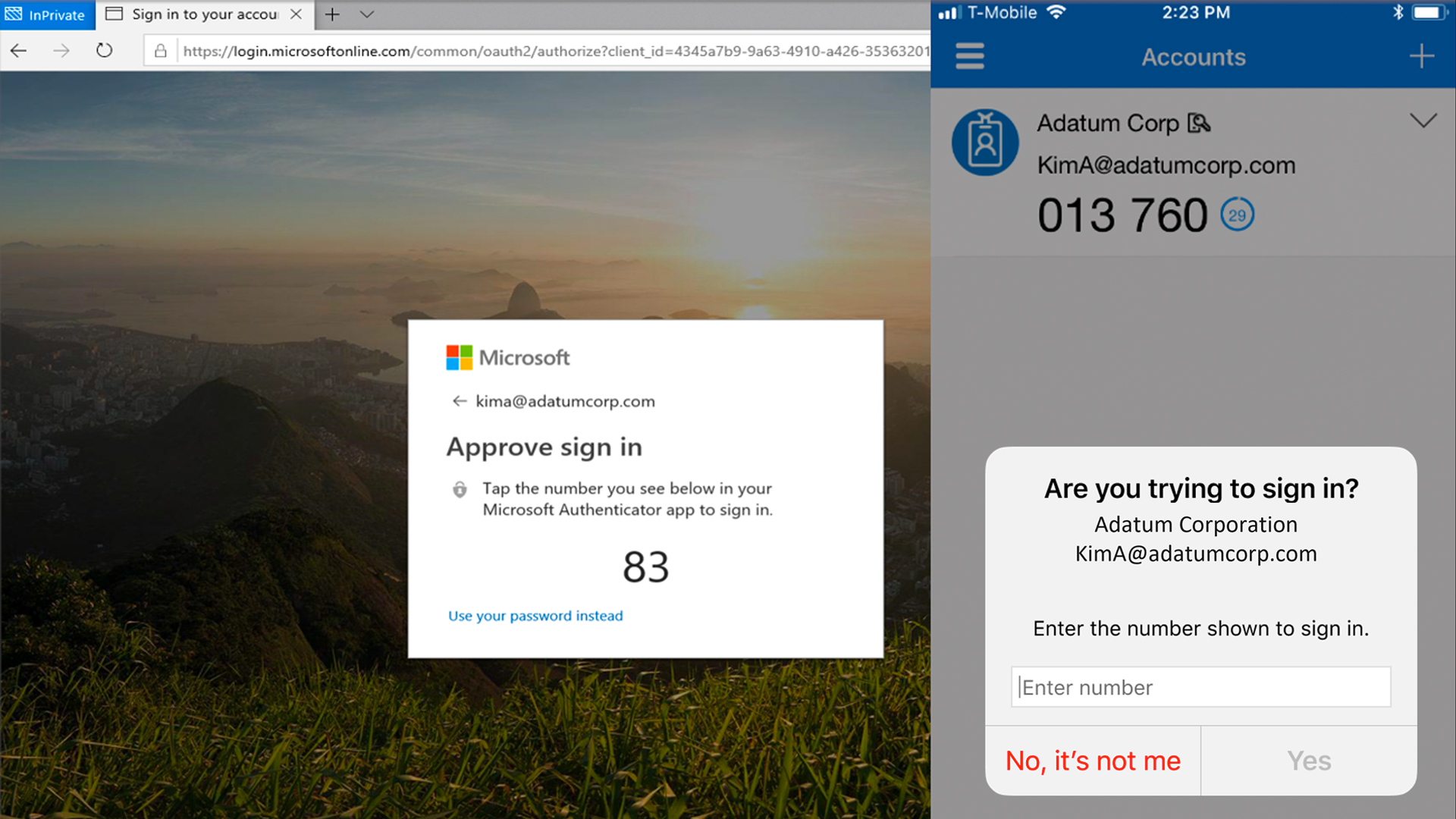
“As relevant services deploy, users worldwide who are enabled for Authenticator push notifications will begin to see number matching in their approval requests,” said Microsoft in its Active Directory (AD) documentation.
“Users can be enabled for Authenticator push notifications either in the Authentication methods policy or the legacy multifactor authentication policy if Notifications through mobile app is enabled.”
Microsoft said number matching will be applied as standard to a number of different authentication scenarios.
RELATED RESOURCE

Users attempting a self-service password reset (SSR) will also have to use MFA number matching to complete the process.
Number matching will also be enforced for combined registration in Azure AD and the AD FS adapter for Windows Server.
Microsoft clarified that users cannot opt out of number matching, but there may be some scenarios that don’t enforce it, such as in MFA Server, which is deprecated, and with old versions of Authenticator which will no longer work, requiring an update.
The AD portal may also still show the setting to enable number matching manually, but Microsoft said that you may just need to refresh the browser in order to see the update.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published
-
 I love magic links – why aren’t more services using them?
I love magic links – why aren’t more services using them?Opinion Using magic links instead of passwords is safe and easy but they’re still infuriatingly underused by businesses
By Solomon Klappholz Published
-
 Password management startup Passbolt secures $8 million to shake up credential security
Password management startup Passbolt secures $8 million to shake up credential securityNews Password management startup Passbolt has secured $8 million in funding as part of a Series A investment round.
By Ross Kelly Published
-
 LastPass breach comes back to haunt users as hackers steal $12 million in cryptocurrency
LastPass breach comes back to haunt users as hackers steal $12 million in cryptocurrencyNews The hackers behind the LastPass breach are on a rampage two years after their initial attack
By Solomon Klappholz Published
-
 GitHub launches passkeys beta for passwordless authentication
GitHub launches passkeys beta for passwordless authenticationNews Users can now opt-in to using passkeys, replacing their password and 2FA method
By Daniel Todd Published
-
 Microsoft SQL password-guessing attacks rising as hackers pivot from OneNote vectors
Microsoft SQL password-guessing attacks rising as hackers pivot from OneNote vectorsNews Database admins are advised to enforce better controls as attacks ending in ransomware are being observed
By Rory Bathgate Published
-
 No, Microsoft SharePoint isn’t cracking users’ passwords
No, Microsoft SharePoint isn’t cracking users’ passwordsNews The discovery sparked concerns over potentially invasive antivirus scanning practices by Microsoft
By Ross Kelly Published
-
 As Google launches passwordless authentication for all, what are the business benefits of passkeys?
As Google launches passwordless authentication for all, what are the business benefits of passkeys?News Google follows Apple in its latest shift to passwordless authentication, but what are the benefits?
By Ross Kelly Published
-
 There's only one way to avoid credential stuffing attacks
There's only one way to avoid credential stuffing attacksOpinion PayPal accounts were breached last year due to a credential stuffing attack, but can PayPal avoid taking responsibility?
By Davey Winder Published