FBI warns of ‘Zoom-bombing’ hackers amid coronavirus usage spike
Cyber criminals are disrupting online meetings with hate speech and pornographic images


The FBI has warned individuals and businesses moving to flexible working patterns that hackers are disrupting video conferences with threatening language, hate speech and pornographic images.
With workplace meetings, and conferences social gatherings moving online en masse, the US law enforcement agency has detailed instances where cyber criminals have intruded on meetings on the likes of Zoom and Skype.
Zoom, in particular, has seen an explosion in usage since the coronavirus pandemic has caused lockdowns and office closures, with more and more people seeking a video conferencing platform to maintain normality.
Its rise in popularity has been coupled with a rise in cyber crime, however. Specifically, the Boston arm of the FBI has noted that reports of ‘Zoom-bombing’ have been flooding in from across the US.
“As large numbers of people turn to video-teleconferencing (VTC) platforms to stay connected in the wake of the COVID-19 crisis, reports of VTC hijacking (also called “Zoom-bombing”) are emerging nationwide,” the FBI Boston Division said.
“The FBI has received multiple reports of conferences being disrupted by pornographic and/or hate images and threatening language.”
The volume of reports has seemingly been rich enough to warrant the FBI issuing an official statement against the threat.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
The FBI Boston Division cited an example where a Massachusetts-based high school reported that while a teacher was hosting an online class, an unidentified individual dialled into the classroom before shouting profanities and Doxxing the teacher.
The agency has warned individuals and businesses against making meetings public, by either making it so the meeting requires a password, or by enabling the waiting room feature through which hosts can control admittance.
Users should also refrain from sharing a teleconferencing link on an unrestricted social media channel, and should instead provide links directly to specific individuals.
People using Zoom should ensure their software is up-to-date, especially given the platform only updated its privacy settings in January 2020 to ensure passwords to meetings were enacted by default.
Although the FBI’s warning largely concerns ensuring that organisations and individuals have activated the correct security and privacy settings, Zoom has been known to suffer from serious vulnerabilities in the past.
Dubbed ‘prying eye’, a flaw discovered in October 2019 allowed cyber criminals to snoop on videos conferences run on the Cisco WebEx and Zoom platforms. The weakness in web conferencing APIs could allow attackers to deploy a brute-force enumeration attack to find open calls or meetings.
After a Zoom flaw was discovered in July, meanwhile, Apple rolled out its own update that removed a web server that allowed websites to automatically launch a conference call and activate the webcam

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published
-
 Protecting every edge to make hackers’ jobs harder, not yours
Protecting every edge to make hackers’ jobs harder, not yoursWhitepaper How to support and secure hybrid architectures
By ITPro Published
-
 Phishing emails target victims with fake vaccine passport offer
Phishing emails target victims with fake vaccine passport offerNews Scammers could steal victims’ personal information and never deliver the illegal goods, Fortinet warns
By Rene Millman Published
-
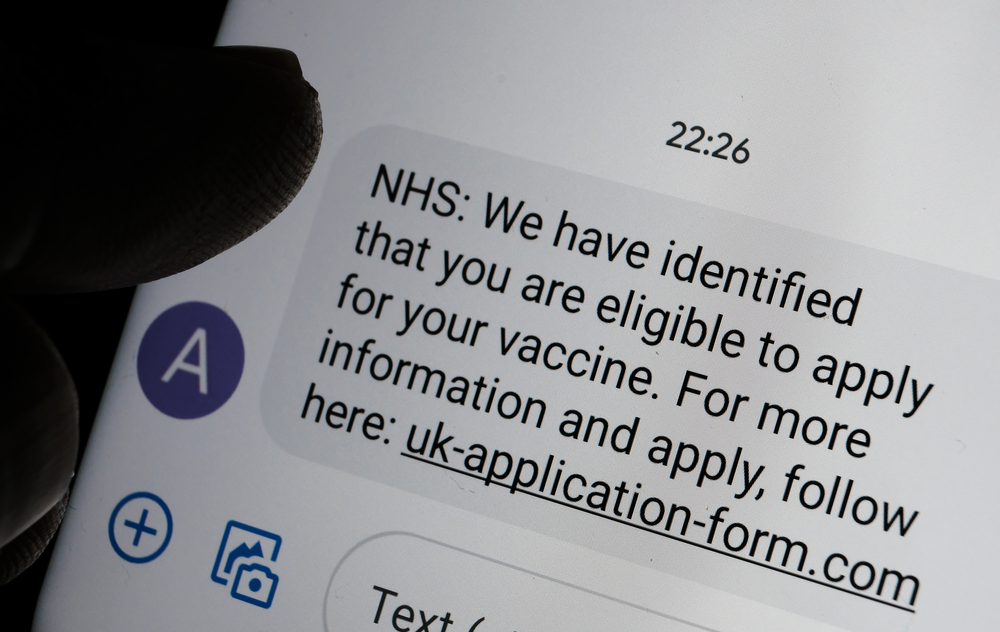 COVID-related phishing fuels a 15-fold increase in NCSC takedowns
COVID-related phishing fuels a 15-fold increase in NCSC takedownsNews The NCSC recorded a significant jump in the number of attacks using NHS branding to lure victims
By Bobby Hellard Published
-
 COVID vaccine passports will fail unless government wins public trust, ICO warns
COVID vaccine passports will fail unless government wins public trust, ICO warnsNews Data watchdog's chief Elizabeth Denham warns that it’s not good enough to claim ‘this is important, so trust us’
By Keumars Afifi-Sabet Published
-
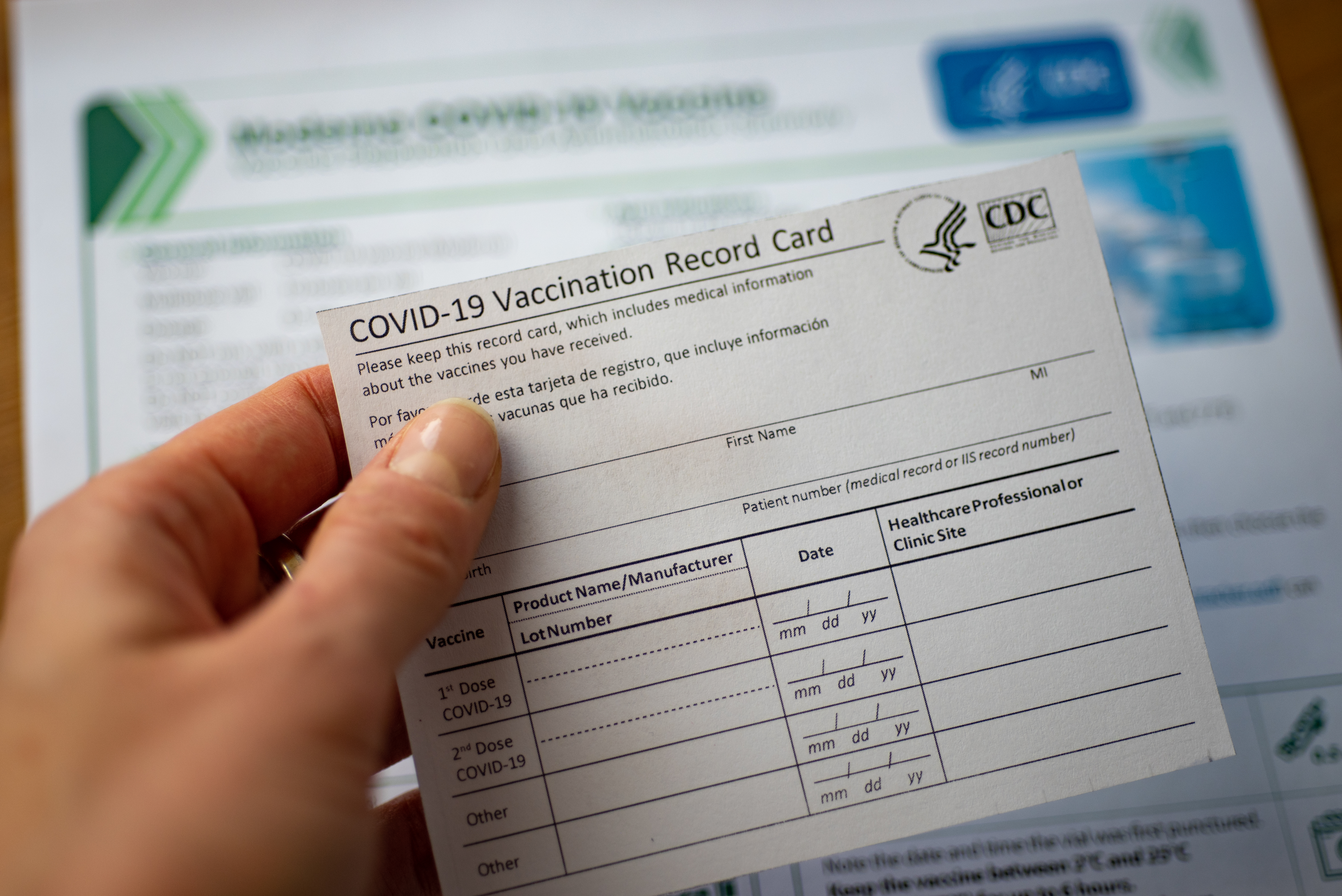 Fake COVID vaccination certificates available on the dark web
Fake COVID vaccination certificates available on the dark webNews Fast-growing market emerges for people wanting quick vaccine proof to travel abroad
By Rene Millman Published
-
 Cyber security firm saw attacks rise by 20% during 2020
Cyber security firm saw attacks rise by 20% during 2020News Trend Micro found attackers also heavily targeted VPNs
By Danny Bradbury Published
-
 Hackers using COVID vaccine as a lure to spread malware
Hackers using COVID vaccine as a lure to spread malwareNews Cyber criminals are impersonating WHO, DHL, and vaccine manufacturers in phishing campaigns
By Rene Millman Published
-
 Website problems slow coronavirus vaccine rollout
Website problems slow coronavirus vaccine rolloutNews Florida is the epicenter of website issues, as patients struggle with malfunctioning sites and hackers
By Danny Bradbury Published