FBI email server hacked to send fake cyber attack alerts
An attacker exploited the system misconfiguration to send legitimate-looking cyber security alerts to partners


The Federal Bureau of Investigation (FBI) confirmed on Saturday that a hacker exploited its systems to send fake emails to law enforcement partners alerting them to a supposed cyber attack.
The hacker exploited a misconfiguration in its Law Enforcement Enterprise Portal (LEEP) web app to send legitimate-looking alerts to partners warning them that they had suffered a cyber attack and that a threat actor was currently in their system.
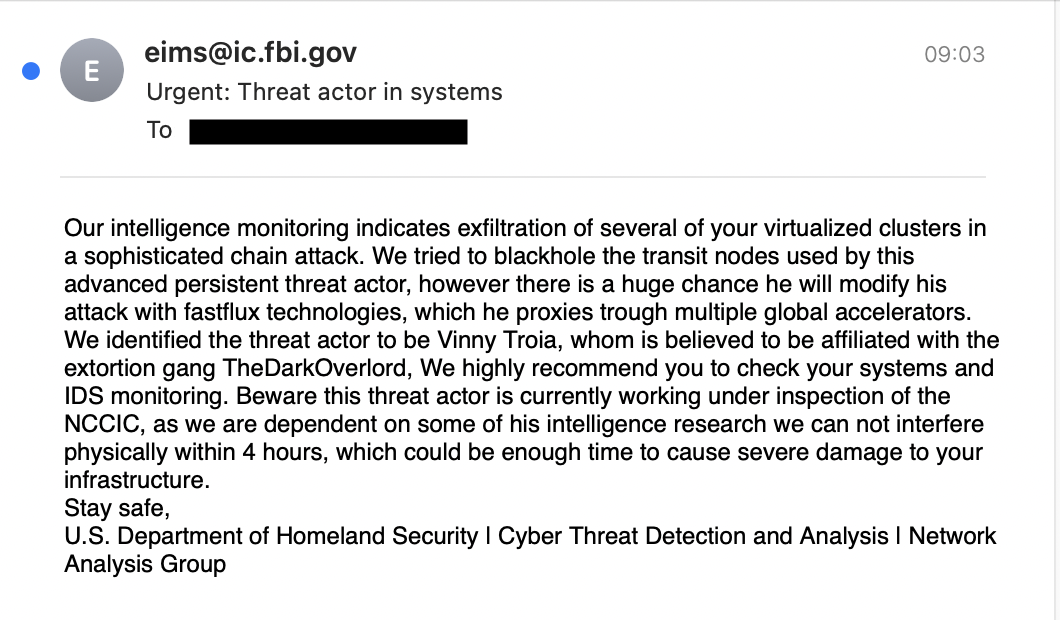
Emails were sent to partners from an official FBI email account with an @ic.fbi.gov domain, the headers of which also appeared to be legitimate after being sanitised.
The hacker falsely informed recipients they had fallen victim to a "sophisticated chain attack" attributed to Vinny Troia, a reputable security researcher and oft subject of memes in the cyber security industry.
Troia rejected his involvement in the attack shortly after its discovery.
The FBI confirmed the threat actor was unable to access or compromise any sensitive data held by the FBI, and said the server used to send the false emails was used only to push notifications for LEEP rather than being connected to the FBI's corporate email service.
"The FBI is aware of a software misconfiguration that temporarily allowed an actor to leverage the Law Enforcement Enterprise Portal (LEEP) to send fake emails," it said on Saturday. "LEEP is FBI IT infrastructure used to communicate with our state and local law enforcement partners.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
"While the illegitimate email originated from an FBI operated server, that server was dedicated to pushing notifications for LEEP and was not part of the FBI’s corporate email service. No actor was able to access or compromise any data or PII on the FBI’s network. Once we learned of the incident, we quickly remediated the software vulnerability, warned partners to disregard the fake emails, and confirmed the integrity of our networks."
Researchers at Spamhaus drew attention to the early reports of fake emails on Saturday, saying the recipients were chosen indiscriminately and email addresses were scraped from an ARIN database.
ARIN is a regional internet registry responsible for the management and distribution of internet number resources such as internet protocol (IP) addresses and autonomous system numbers (ASNs).
The email sent to recipients appeared as follows:
Spamhaus said its telemetry indicated two 'waves' of spam emails being sent, one just before 05:00 on Saturday and then another shortly after 07:00.
Security researchers reported having contacted the FBI at the time of the incident said the staff were "slammed" with calls from alarmed recipients trying to verify if the correspondence was legitimate or not.
RELATED RESOURCE

The best defence against ransomware
How ransomware is evolving and how to defend against it
A hacker known by the alias Pompompurin claimed responsibility for the attack in an interview with security researcher Brian Krebs. They said they wanted to draw attention to the security vulnerability in the LEEP web app.
Pompompurin said LEEP allowed anyone to apply for an account, despite it being reserved only for law enforcement partners of the FBI. Account authentication was also run through a one-time passcode emailed to the applicant - a code which the FBI's website leaked in the HTML code of its web page.
When users requested a confirmation code, they were sent a POST request which included parameters for the email subject and body content. Pompompurin replaced the parameters with his own email subject and body to automate thousands of email sends.
Experts have suggested that the level access Popompurin was able to achieve was worrying and that a wider attack campaign could have bene launched to compromise law enforcement partners across the US.
"The hack could have enabled an attacker to disperse a phishing email campaign to all the FBI’s state and local law enforcement partners - one that was designed to compromise US-wide law enforcement," said Alan Calder, CEO at GRC International Group.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Can the ‘microshifting’ trend work in the tech sector?
Can the ‘microshifting’ trend work in the tech sector?In-depth Research shows that employees want to break up their working days into short, flexible blocks – here’s how tech leaders can implement what’s being coined as ‘microshifting’
-
 Brother DCP-L1640W review
Brother DCP-L1640W reviewReviews This compact mono laser multifunction looks perfect for home workers, but is its appeal more than skin-deep?
-
 Two Fortinet vulnerabilities are being exploited in the wild – patch now
Two Fortinet vulnerabilities are being exploited in the wild – patch nowNews Arctic Wolf and Rapid7 said security teams should act immediately to mitigate the Fortinet vulnerabilities
-
 Everything you need to know about Google and Apple’s emergency zero-day patches
Everything you need to know about Google and Apple’s emergency zero-day patchesNews A serious zero-day bug was spotted in Chrome systems that impacts Apple users too, forcing both companies to issue emergency patches
-
 Security experts claim the CVE Program isn’t up to scratch anymore — inaccurate scores and lengthy delays mean the system needs updated
Security experts claim the CVE Program isn’t up to scratch anymore — inaccurate scores and lengthy delays mean the system needs updatedNews CVE data is vital in combating emerging threats, yet inaccurate ratings and lengthy wait times are placing enterprises at risk
-
 IBM AIX users urged to patch immediately as researchers sound alarm on critical flaws
IBM AIX users urged to patch immediately as researchers sound alarm on critical flawsNews Network administrators should patch the four IBM AIX flaws as soon as possible
-
 Critical Dell Storage Manager flaws could let hackers access sensitive data – patch now
Critical Dell Storage Manager flaws could let hackers access sensitive data – patch nowNews A trio of flaws in Dell Storage Manager has prompted a customer alert
-
 Flaw in Lenovo’s customer service AI chatbot could let hackers run malicious code, breach networks
Flaw in Lenovo’s customer service AI chatbot could let hackers run malicious code, breach networksNews Hackers abusing the Lenovo flaw could inject malicious code with just a single prompt
-
 Industry welcomes the NCSC’s new Vulnerability Research Initiative – but does it go far enough?
Industry welcomes the NCSC’s new Vulnerability Research Initiative – but does it go far enough?News The cybersecurity agency will work with external researchers to uncover potential security holes in hardware and software
-
 Hackers are targeting Ivanti VPN users again – here’s what you need to know
Hackers are targeting Ivanti VPN users again – here’s what you need to knowNews Ivanti has re-patched a security flaw in its Connect Secure VPN appliances that's been exploited by a China-linked espionage group since at least the middle of March.