Encryption
Discover expert analysis on encryption with news, features and insights from the team at IT Pro.
-

Australian Federal Police plots "aggressive" cyber division following law change
News New powers allow law enforcement to launch disruptive operations and collect data on suspected criminals
By Zach Marzouk Published
News -
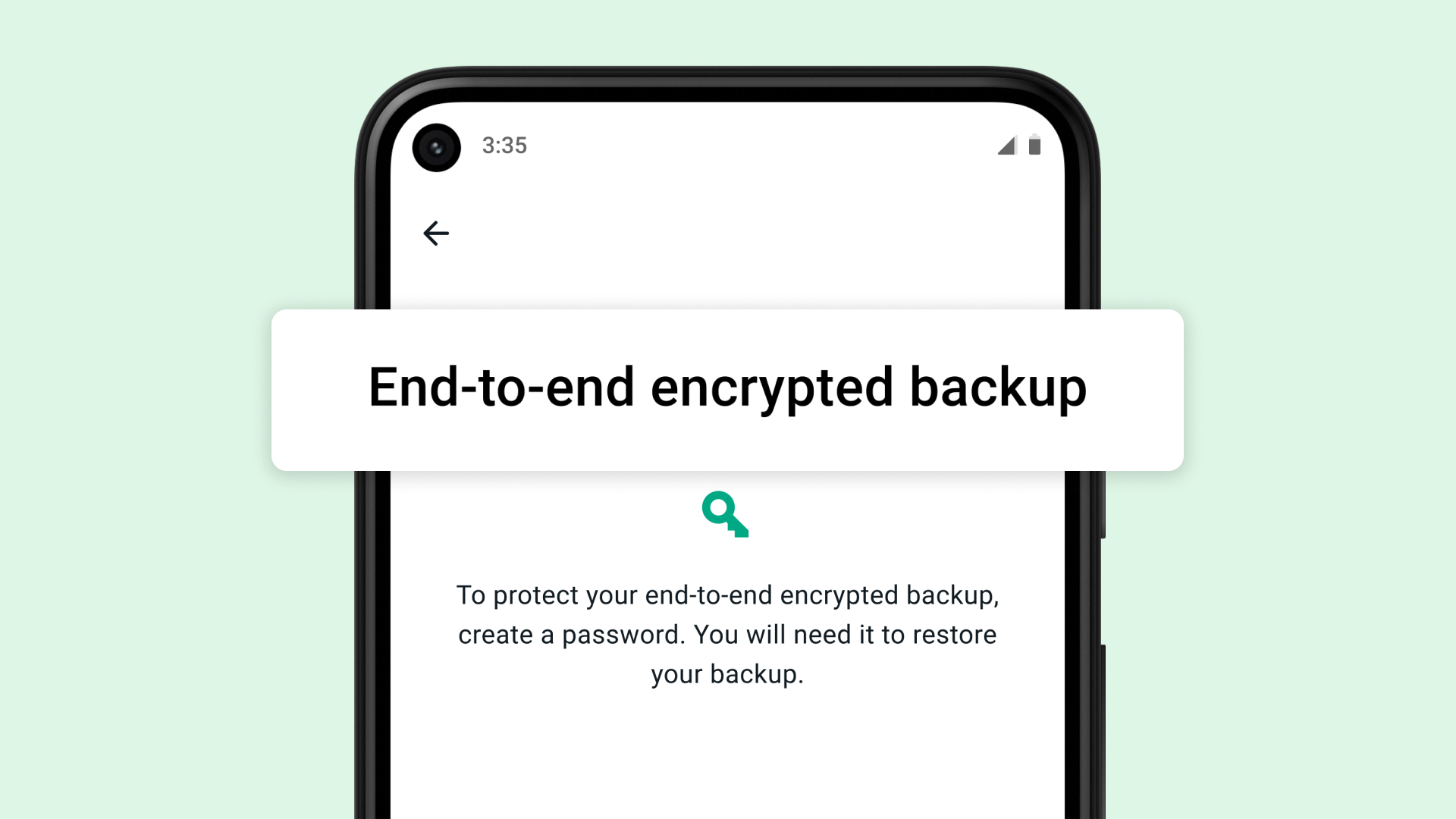
WhatsApp backups to get end-to-end encryption
News Facebook says it's the final step towards a full end-to-end encrypted messaging experience on the chat app
By Bobby Hellard Published
News -

WhatsApp activates end-to-end encrypted cloud backups
News The messaging service will grant users a password-protected key when they save their chat histories to the cloud
By Keumars Afifi-Sabet Published
News -
ProtonMail criticised for sharing activist's IP address with law enforcement
News The company prides itself on benefitting from Switzerland's strict privacy laws, yet had to follow the “legally binding order"
By Sabina Weston Published
News -
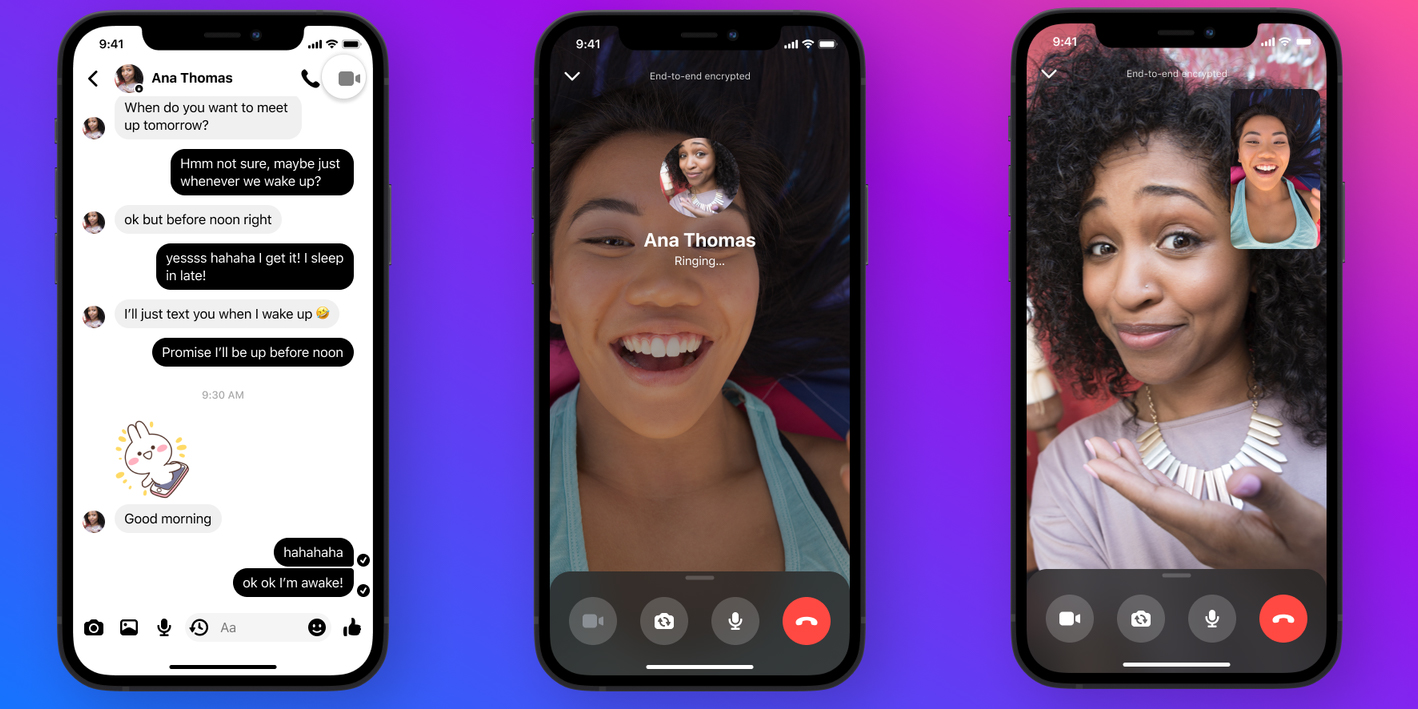
Facebook defies gov pressure with end-to-end encryption expansion
News The social network is bringing E2EE to Messenger voice and video calls
By Sabina Weston Published
News -

From zero to hero: The path to CIAM maturity
Whitepaper Your guide to the CIAM journey
By ITPro Published
Whitepaper -

Lantronix adds zero-touch automation to its SaaS platform
News Update allows remote installation of Lantronix’s IoT and OOB devices
By Praharsha Anand Published
News -

WhatsApp launches multi-device beta with support for end to end encryption
News An infrastructure change means up to four devices can be attached to a single account without compromising security or privacy, company claims
By Bobby Hellard Published
News -
Futurex and Google enable client-side Google Workspace encryption
News Full-spectrum key management solution allows customer-controlled import and export of cryptographic keys
By Praharsha Anand Published
News -

US and Australia arrest 'hundreds' in encrypted messaging sting
News The 'Anom' app was installed on phones distributed by authorities and has led to arrests in 18 countries across the globe
By Zach Marzouk Published
News -

WhatsApp sues Indian government over new privacy laws
News The law requires social media companies to identify users when authorities demand it, which could see the end of encryption
By Zach Marzouk Published
News -

UK gov warns Facebook's encryption plan could harm child safety
News Home secretary Priti Patel is set to deliver a speech on the dangerous effects of end-to-end encryption
By Sabina Weston Published
News