Lenovo ThinkPads vulnerable to privilege escalation exploit, researchers warn
A component running on the popular business computers is vulnerable to a chained exploit that grants full access to attackers


Users of Lenovo's range of ThinkPad workstations have been warned to patch their systems following the discovery of flaws that allows hackers to launch privilege escalation attacks.
It's believed that two separate flaws can be chained together to target the ImControllerService component and change a user's access level to a system, according to security researchers at NCC Group.
The ImControllerService is a component present on Lenovo's ThinkPad hardware range and controls tasks such as system power management and app and driver updates.
The vulnerability can be triggered by exploiting two flaws, tracked as CVE-2021-3922 and CVE-2021-3969, affecting the way in which the ImControllerService handles the execution of highly privileged child processes, NCC Group said.
The normal running of a system will have the ImControllerService periodically start child processes that open named pipe servers. These named pipe servers connect to the parent process in order to retrieve and execute the necessary XML serialised commands.
One of these commands is to load a plugin from an arbitrary location on the system. The child process is required to validate the digital signature of the plugin dynamic-link library (DLL) before loading and executing the file.
However, hackers are able to hijack this process in order to change privileges and load any payload of their choosing onto the machine.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
RELATED RESOURCE

Modernise endpoint protection and leave your legacy challenges behind
The risk of keeping your legacy endpoint security tools
The first vulnerability lies in the fact that the child process fails to check whether the source of the initial connection is legitimate. This creates a race condition that effectively sees the hacker try and make a connection with the named pipe ahead of the parent process.
"An attacker using high-performance filesystem synchronisation routines can reliably win the race with the parent process to connect to the named pipe," said NCC Group. During testing NCC Group’s proof of concept code never failed to connect to the named pipe before the parent service could do so.
"Because the child process does not validate the source of the connection it will begin accepting commands from the attacker after the race condition has been exploited."
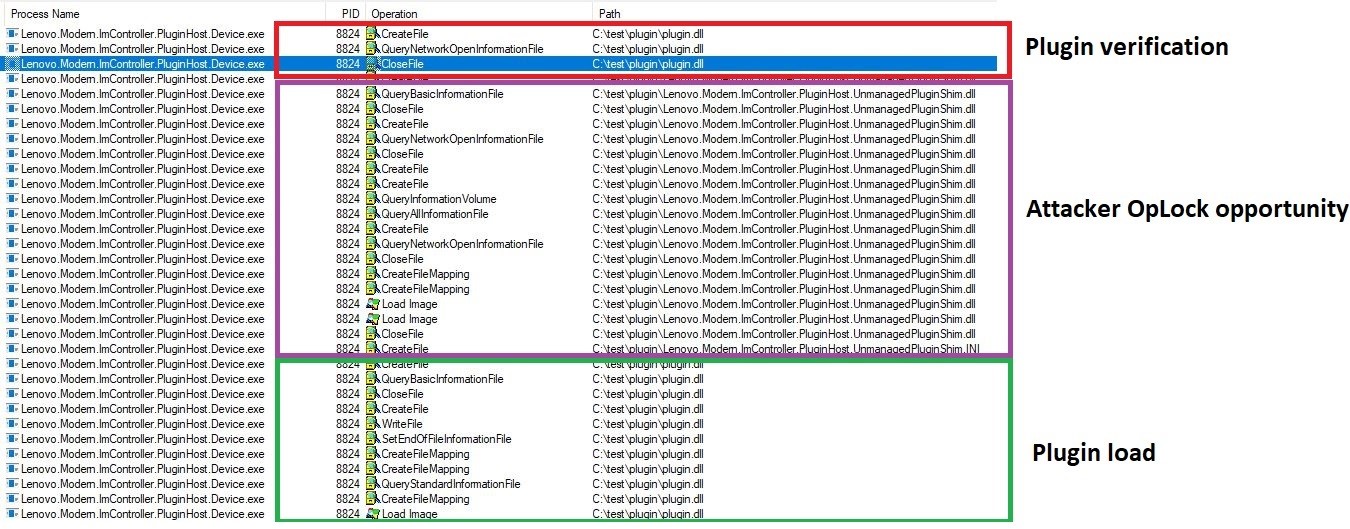
The second vulnerability is a time-of-check to time-of-use flaw, which stems from how the child process validates the plugin it's being asked to load. When loading a DLL, the child process validates its authenticity by checking if it's signed by Lenovo.
However, attackers can use opportunistic locking (OpLocks) on a file to stall the validation process long enough for them to load their own DLL. Once the lock is released, the machine will load the DLL of the attacker's choosing which leads to privilege escalation.
Lenovo has released an advisory in which it warns users to patch machines to the latest IMController version (version 1.1.20.3). The component is automatically updated by the Lenovo System Interface Foundation Service, which means the update can be triggered by rebooting the machine or manually restarting the 'System Interface Foundation Service' service, it said.
It's currently unclear how many Lenovo machines were, or currently are, thought to be affected globally, but Lenovo told IT Pro: "Lenovo worked with NCC in line with industry best practices and fixed the issue in November and customers are already protected."

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 The UK government wants quantum technology out of the lab and in the hands of enterprises
The UK government wants quantum technology out of the lab and in the hands of enterprisesNews The UK government has unveiled plans to invest £121 million in quantum computing projects in an effort to drive real-world applications and adoption rates.
By Emma Woollacott Published
-
 Netgear WBE710 review
Netgear WBE710 reviewReviews The compact WBE710 delivers great cloud management features and a good turn of Wi-Fi 7 speed – but it does have a premium price tag
By Dave Mitchell Published
-
 Hackers are targeting Ivanti VPN users again – here’s what you need to know
Hackers are targeting Ivanti VPN users again – here’s what you need to knowNews Ivanti has re-patched a security flaw in its Connect Secure VPN appliances that's been exploited by a China-linked espionage group since at least the middle of March.
By Emma Woollacott Published
-
 Broadcom issues urgent alert over three VMware zero-days
Broadcom issues urgent alert over three VMware zero-daysNews The firm says it has information to suggest all three are being exploited in the wild
By Solomon Klappholz Published
-
 Nakivo backup flaw still present on some systems months after firms’ ‘silent patch’, researchers claim
Nakivo backup flaw still present on some systems months after firms’ ‘silent patch’, researchers claimNews Over 200 vulnerable Nakivo backup instances have been identified months after the firm silently patched a security flaw.
By Solomon Klappholz Published
-
 Everything you need to know about the Microsoft Power Pages vulnerability
Everything you need to know about the Microsoft Power Pages vulnerabilityNews A severe Microsoft Power Pages vulnerability has been fixed after cyber criminals were found to have been exploiting unpatched systems in the wild.
By Solomon Klappholz Published
-
 Vulnerability management complexity is leaving enterprises at serious risk
Vulnerability management complexity is leaving enterprises at serious riskNews Fragmented data and siloed processes mean remediation is taking too long
By Emma Woollacott Published
-
 A critical Ivanti flaw is being exploited in the wild – here’s what you need to know
A critical Ivanti flaw is being exploited in the wild – here’s what you need to knowNews Cyber criminals are actively exploiting a critical RCE flaw affecting Ivanti Connect Secure appliances
By Solomon Klappholz Published
-
 Researchers claim an AMD security flaw could let hackers access encrypted data
Researchers claim an AMD security flaw could let hackers access encrypted dataNews Using only a $10 test rig, researchers were able to pull off the badRAM attack
By Solomon Klappholz Published
-
 Amazon confirms employee data compromised amid 2023 MOVEit breach claims – but the hacker behind the leak says a host of other big tech names are also implicated
Amazon confirms employee data compromised amid 2023 MOVEit breach claims – but the hacker behind the leak says a host of other big tech names are also implicatedNews Millions of records stolen during the 2023 MOVEit data breach have been leaked
By Solomon Klappholz Published