Hackers using COVID vaccine as a lure to spread malware
Cyber criminals are impersonating WHO, DHL, and vaccine manufacturers in phishing campaigns


Security researchers have exposed a new phishing campaign that uses COVID-19 vaccine news to spread malware, phishing, and Business Email Compromise attacks (BEC).
The attacks target individuals within businesses by impersonating organizations, including the WHO, DHL, and vaccine manufacturers. The themes leveraged a range of topics, including the fear that a person had encountered an infected individual; government vaccine approvals and economic recovery fueled by the vaccine; and sign-up forms to receive the vaccine, information updates, and vaccine shipment delivery.
According to a Proofpoint blog post, the BEC attack campaigns were far more targeted. They reportedly gave information on a bogus merger/acquisition and were sent directly to senior executives in the affected organizations.
Researchers first noted the attacks in early December 2019. These emails projected that COVID-19 vaccines would fuel the world's economic recovery. The email claimed to be from an executive asking the recipient for their cooperation in a foreign company’s confidential acquisition. It alleged that this is an opportune moment to acquire, as in the "midst of every crisis lies a great opportunity."
This month, hackers sent hundreds of messages over four days that targeted dozens of industries in the US and Canada. The emails urged the potential victims to click a link to "confirm their email to receive the vaccine.” The goal of this phishing campaign was to steal Microsoft 365 login credentials.
“This campaign was notable because it capitalized on the recent government approval of vaccines and the rush to receive it. Specifically, the email talks about "Government approval of the COVID-19 vaccine" and provides a link where one can supposedly register to receive it. At the time of this campaign, the vaccine in the United States was still available to first responders and doctors on the front lines,” said researchers.
On January 11, researchers observed another small (under 100 emails) BEC email campaign targeting various US industries. This email only briefly mentions the COVID-19 vaccine but adds urgency - a common BEC technique - to the follow-up request: "Please give me your personal number."
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
“This attempt to increase the stress by giving the recipient less time to think about their response and allowing the attacker to pivot outside of a protected ecosystem,” said researchers.
Two other campaigns abused the World Health Organization logo and name to spread trojans and keyloggers and the DHL brand to steal email login credentials. Both used news on COVID-19 vaccines to lure victims into clicking on malicious links.
Rene Millman is a freelance writer and broadcaster who covers cybersecurity, AI, IoT, and the cloud. He also works as a contributing analyst at GigaOm and has previously worked as an analyst for Gartner covering the infrastructure market. He has made numerous television appearances to give his views and expertise on technology trends and companies that affect and shape our lives. You can follow Rene Millman on Twitter.
-
 DocuWare CEO Michael Berger on the company’s rapid growth
DocuWare CEO Michael Berger on the company’s rapid growthNews ChannelPro sat down with DocuWare CEO Michael Berger to discuss the company's rapid growth and channel strategy.
By Bobby Hellard Published
-
 Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up sting
Seized database helps Europol snare botnet customers in ‘Operation Endgame’ follow-up stingNews Europol has detained several people believed to be involved in a botnet operation as part of a follow-up to a major takedown last year.
By Emma Woollacott Published
-
 Phishing emails target victims with fake vaccine passport offer
Phishing emails target victims with fake vaccine passport offerNews Scammers could steal victims’ personal information and never deliver the illegal goods, Fortinet warns
By Rene Millman Published
-
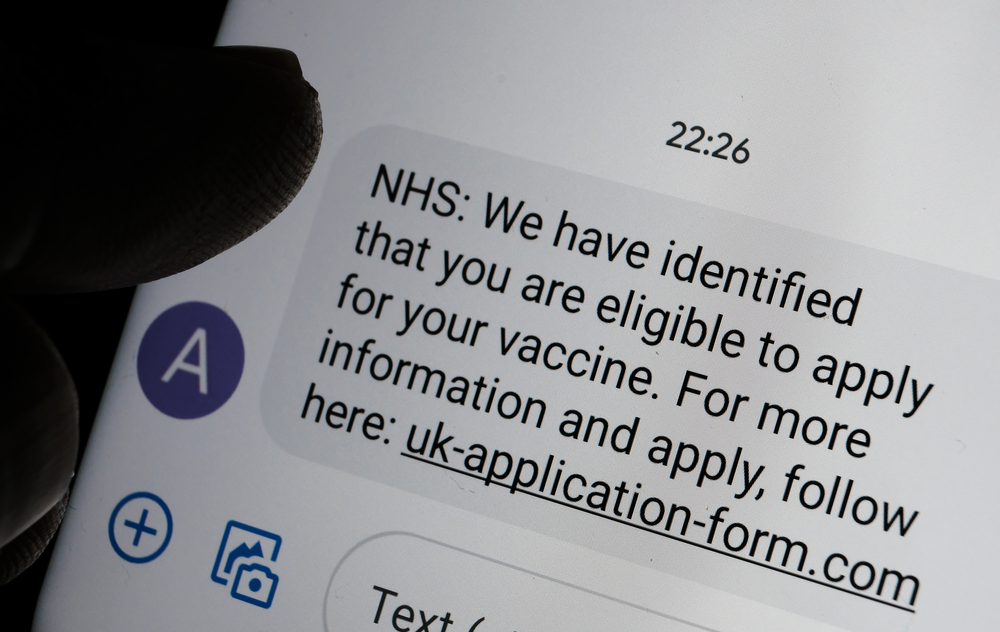 COVID-related phishing fuels a 15-fold increase in NCSC takedowns
COVID-related phishing fuels a 15-fold increase in NCSC takedownsNews The NCSC recorded a significant jump in the number of attacks using NHS branding to lure victims
By Bobby Hellard Published
-
 COVID vaccine passports will fail unless government wins public trust, ICO warns
COVID vaccine passports will fail unless government wins public trust, ICO warnsNews Data watchdog's chief Elizabeth Denham warns that it’s not good enough to claim ‘this is important, so trust us’
By Keumars Afifi-Sabet Published
-
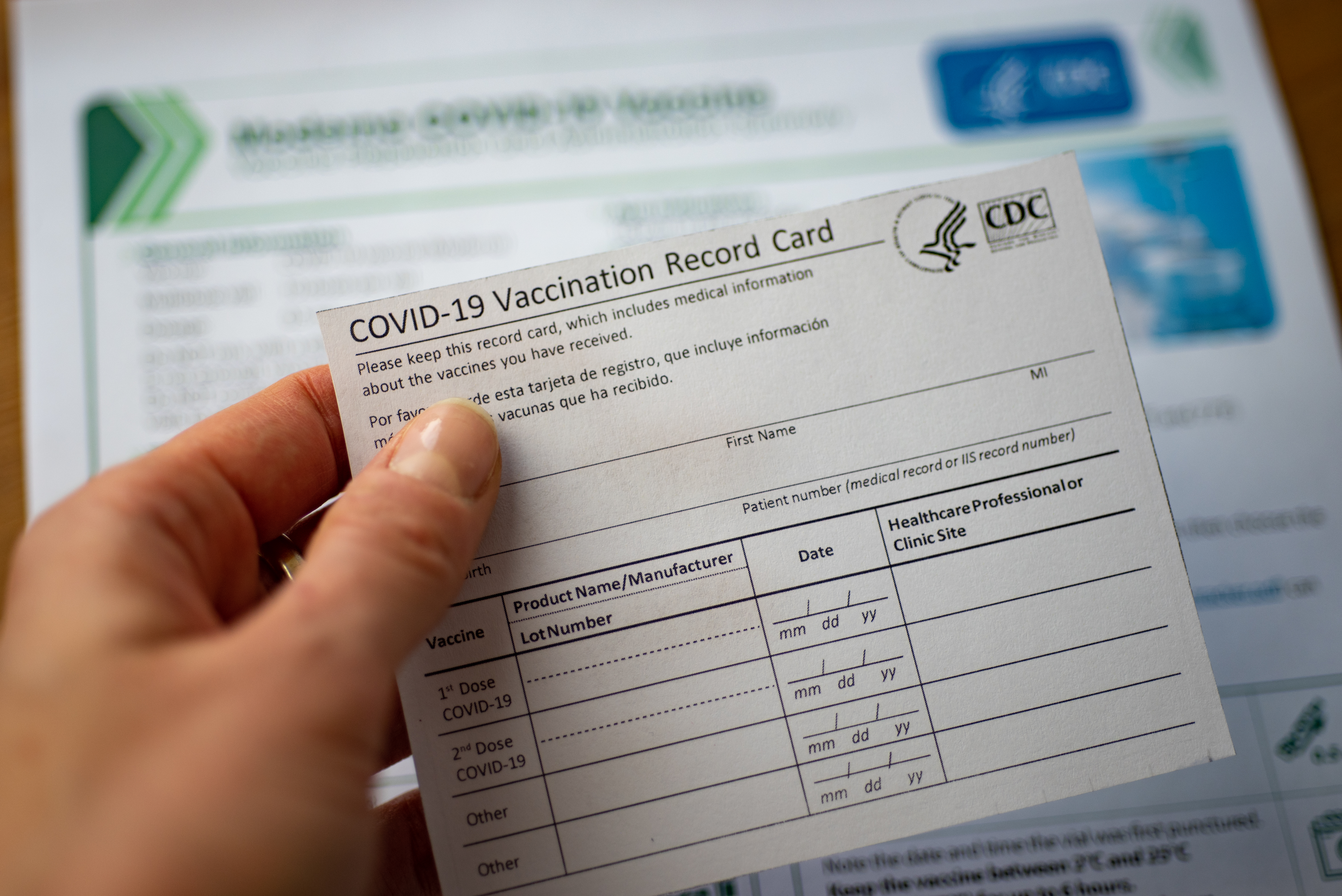 Fake COVID vaccination certificates available on the dark web
Fake COVID vaccination certificates available on the dark webNews Fast-growing market emerges for people wanting quick vaccine proof to travel abroad
By Rene Millman Published
-
 Cyber security firm saw attacks rise by 20% during 2020
Cyber security firm saw attacks rise by 20% during 2020News Trend Micro found attackers also heavily targeted VPNs
By Danny Bradbury Published
-
 Website problems slow coronavirus vaccine rollout
Website problems slow coronavirus vaccine rolloutNews Florida is the epicenter of website issues, as patients struggle with malfunctioning sites and hackers
By Danny Bradbury Published
-
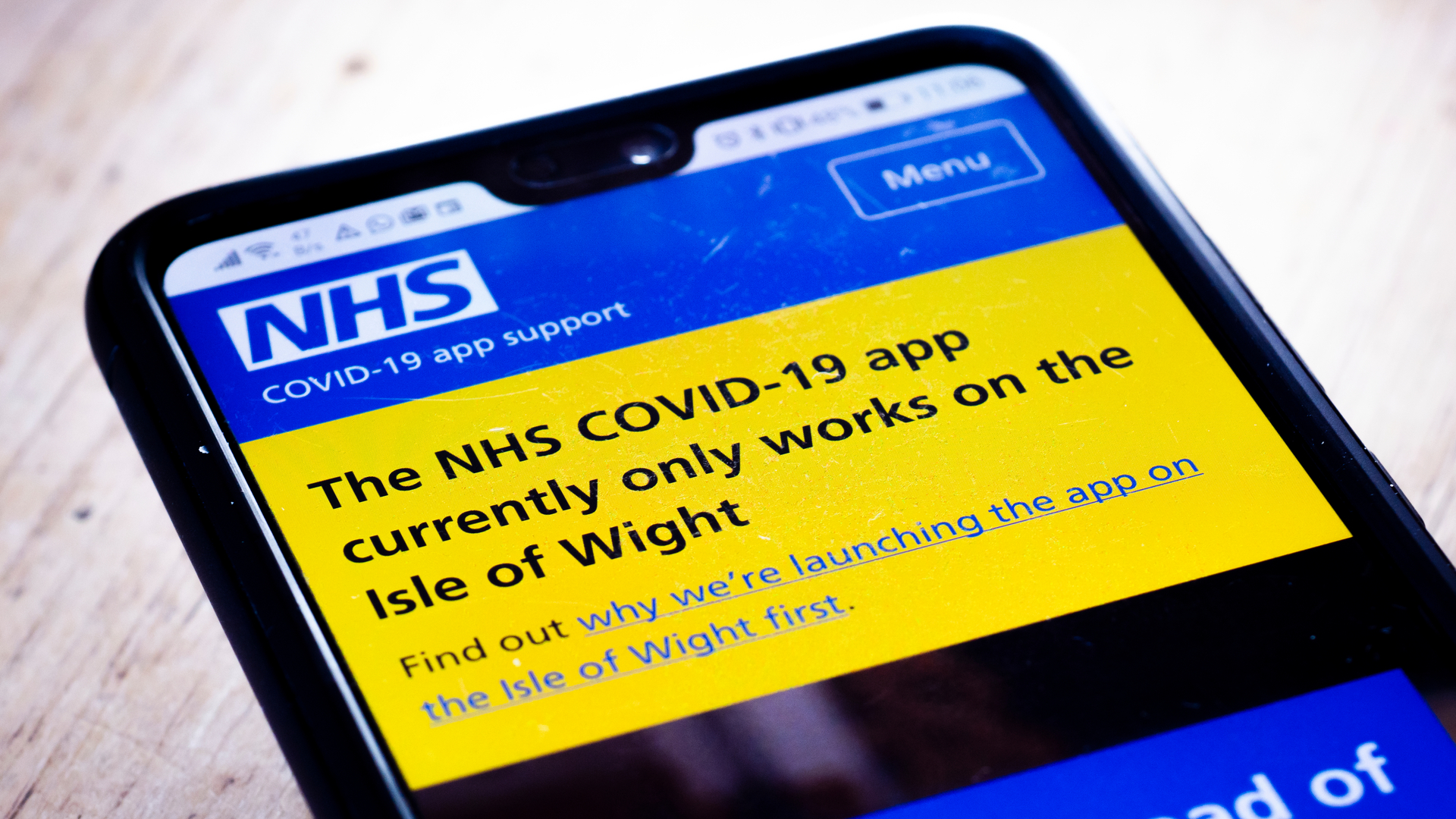 NHS COVID-19 app failed to ask users to self-isolate due to 'software glitch'
NHS COVID-19 app failed to ask users to self-isolate due to 'software glitch'News The bug is the latest in a long line of errors and glitches to plague the government's contact-tracing app
By Keumars Afifi-Sabet Published
-
 How businesses were left to scramble over data collection for coronavirus contact tracing
How businesses were left to scramble over data collection for coronavirus contact tracingIn-depth The lack of sufficient advice has opened the door for third-party tech firms to normalise massive-scale data harvesting
By Keumars Afifi-Sabet Published