Are your business's mobile devices secure enough?
Businesses have never had access to so many mobile devices – nor as many ways to lose sensitive data.
The business world is going increasingly mobile. Laptops have long outsold desktop computers, and by 2015, IDC predicts that sales of tablets will have overtaken desktop PCs, too. For the IT manager this is both a blessing and a curse.
It's a blessing in the sense that staff can work more flexibly than ever before, reading emails on a compact tablet whilst travelling between meetings or using a touchscreen laptop to literally flick through presentations at a client's office; it's a curse because your business data is now stored on more devices than ever before, providing greater opportunity for thieves to get their hands on it.
That not only carries the risk of financial loss, but of a customer backlash and even regulatory action if your security was found to be inadequate. The Information Commissioner's Office (ICO) routinely fines organisations five- or six-figure sums for data breaches resulting from lost or stolen devices.
Here, we're going to show you how to secure the critical data stored on your mobile Windows devices, and how you can track and remotely wipe devices that have been stolen or mislaid.
Secure sign-in
It goes without saying that employees must be forced to log in to their device with some form of user authentication, whether that be the traditional password, fingerprint reader, smartcard solution or one of the new Windows 8 options aimed at mobile devices.
Many companies deploying PCs, laptops and tablets to their workforce will have a password policy mandated by Group Policy. This, for example, may mean that users are forced to renew their password every 90 days or use a minimum number of characters in their passwords.
Organisations deploying Windows 8 tablet devices may want to review their password policy to ensure it covers new sign-in solutions, such as Picture Passwords, especially on devices without access to a physical keyboard, where entering a strong password could be cumbersome using the onscreen keyboard. Picture Passwords allow users to access the device by tapping or swiping gestures on a digital photo of their choosing. They could, for example, have a photo of their family, and tap on each child in alphabetical order to unlock their device.

According to Microsoft's research, a Picture Password with only three gestures offers equivalent security to a conventional five or six character password, and has the added benefits of being far easier to remember and quicker to enter for users with touchscreen devices.
Windows 8 also introduces the concept of virtual smartcards, where instead of carrying around a physical smartcard, the user's credentials are stored on the laptop's Trusted Platform Module (TPM) chip. Users still have to enter a PIN to access the device, as they would with an ordinary smartcard reader, but should they lose the device, they can contact their IT administrator and have the virtual smartcard revoked immediately, preventing any unauthorised access to the device.
Data encryption
Preventing unauthorised access to a device requires more than a good password policy. Even without the user's password, thieves can still access data on stolen devices by physically removing hard disks or solid-state drives and accessing their contents on another computer unless those drives are encrypted.
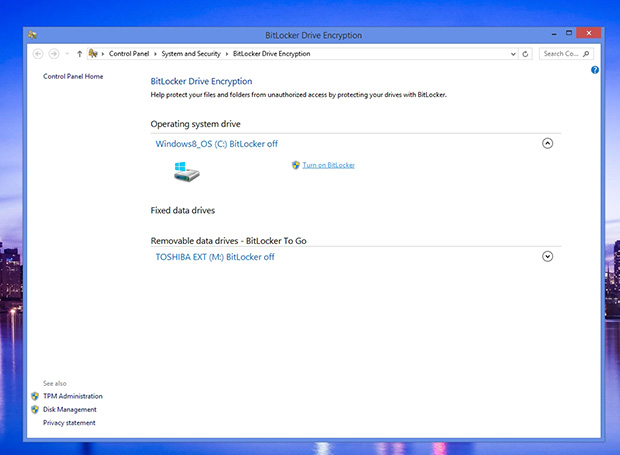
There are many third-party encryption solutions available, including those provided by HP and its partners. Windows 7 and 8 both have their own built-in encryption technology, BitLocker, which can be used to protect system drives and external disks that are plugged into the company's PCs.
IT administrators can apply Group Policy to BitLocker to ensure, for example, that employees can't copy data to USB thumb drives without first ensuring the drive is encrypted, preventing one of the most common and costly methods of accidental data loss. Administrators have access to recovery keys, should the user forget their password. BitLocker can also be used in conjunction with other security measures, such as smartcards, to ensure that unauthorised users don't get access to sensitive data.
Tracking and recovering stolen devices
If a device is lost, there's no need to write it off immediately if it's fitted with tracking technology. HP's Tracking and Recovery Service uses a combination of Wi-Fi and GPS receivers (on compatible devices) to locate missing devices. IT administrators can track devices using an online map and view current and historical location data, providing information that could allow the employee/company to retrieve the missing equipment, or provide accurate location data to the police in the event of a suspected theft.
If the device cannot be recovered immediately, HP Tracking and Recovery allows the IT department to remotely wipe the device, ensuring that sensitive data cannot be accessed by thieves. IT administrators can choose to wipe individual files, directories, user data or the entire disk, providing the flexibility to manage the risk of each situation.
Advanced optional features include geofencing, which sends alerts to IT administrators if a company laptop is detected outside of a predefined boundary, such as leaving the office or even the country. This allows companies to react proactively to unauthorised movements, rather than waiting for a theft to be reported.
Tracking and data deletion commands are handled by a software agent installed on each PC. HP recommends that the agent is preloaded within the "Persistence Module" on the BIOS. This ensures that the software agent is restored, even if thieves attempt to delete the software.
The HP Tracking and Recovery Service is not only useful for anti-theft measures, it can also help with asset management. The agent can collect information on the laptop's hardware and the software installed on the machine, alerting administrators if any unauthorised or unlicensed software is found on the PC.
With all these features combined, companies minimise their risk of suffering from the theft of critical information, have a full audit log to prove to regulators that they took the necessary steps to secure stolen devices, and greatly reduce the risk of fines for unlicensed software being installed on company PCs by employees.
The right balance
With the appropriate security measures in place, there's no reason why companies can't reap the full benefits of the new wave of mobile devices. Touchscreen laptops, tablets and hybrid devices provide all manner of opportunities for employees to find creative new ways of working. Companies need not fear having their sensitive data scattered across a vast range of mobile devices, provided that those devices are secured, encrypted and able to be wiped the moment that something goes wrong.
For more advice on transforming your business, visit HP BusinessNow
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Barry Collins is an experienced IT journalist who specialises in Windows, Mac, broadband and more. He's a former editor of PC Pro magazine, and has contributed to many national newspapers, magazines and websites in a career that has spanned over 20 years. You may have seen Barry as a tech pundit on television and radio, including BBC Newsnight, the Chris Evans Show and ITN News at Ten.
-
 Asus ZenScreen Fold OLED MQ17QH review
Asus ZenScreen Fold OLED MQ17QH reviewReviews A stunning foldable 17.3in OLED display – but it's too expensive to be anything more than a thrilling tech demo
By Sasha Muller
-
 How the UK MoJ achieved secure networks for prisons and offices with Palo Alto Networks
How the UK MoJ achieved secure networks for prisons and offices with Palo Alto NetworksCase study Adopting zero trust is a necessity when your own users are trying to launch cyber attacks
By Rory Bathgate
-
 A DevOps guide to the Salesforce platform
A DevOps guide to the Salesforce platformWhitepaper Learn how to ship code faster, safer, and with agility.
By ITPro
-
 Google will cull out-of-date Play store apps in bid to improve Android security
Google will cull out-of-date Play store apps in bid to improve Android securityNews The rules will take effect later this year and could see unsupported apps de-listed from the store
By Connor Jones
-
 HP reveals Microsoft licensing management service for SMBs
HP reveals Microsoft licensing management service for SMBsNews The company wants to make it easier for small businesses to manage their cloud-based subscriptions
By Zach Marzouk
-
 Tech giants lobby US to fund chip production
Tech giants lobby US to fund chip productionNews Industry heavyweights ask Congress for $50 billion in chip manufacturing subsidies
By Mike Brassfield
-
 HP Pro c640 Chromebook review: Nailing the basics
HP Pro c640 Chromebook review: Nailing the basicsReviews While it’s a pleasure to type with, this device is let down by several serious weaknesses
By Keumars Afifi-Sabet
-
 The IT Pro Products of the Year 2019: All the year’s best hardware
The IT Pro Products of the Year 2019: All the year’s best hardwareBest Our favourite equipment from the past 12 months
By ITPro
-
 Android phones vulnerable to advanced SMS phishing attacks
Android phones vulnerable to advanced SMS phishing attacksNews Researchers discover an attack vector that could once be only imagined in a "high-tech spy movie"
By Connor Jones
-
 Android vs iOS: Which mobile OS is right for you?
Android vs iOS: Which mobile OS is right for you?Vs We look at design, security, compatibility and more to see which OS best fits your business
By Keumars Afifi-Sabet
