Researchers uncover 'mysterious' Windows rootkit being actively exploited since 2016
Experts at Kaspersky say the rootkit was found embedded inside the firmware image of legacy Asus and Gigabyte motherboards

A mysterious and powerful rootkit has been uncovered that is said to have remained hidden and exploited in attacks since 2016.
Dubbed ‘CosmicStrand’, Kaspersky researchers said the UEFI rootkit was found on a number of victims’ machines across China, Russia, Iran, and Vietnam.
The malicious rootkit was found on Asus and Gigabyte motherboards that shared the H81 chipset, released between 2013 and 2015, indicating there may be a common vulnerability across this equipment which has largely been discontinued.
UEFI malware is not too common, but there has been a slight increase in attacks in recent years, with more research uncovering campaigns such as MoonBounce and LoJax.
Kaspersky predicts attacks of this nature will increase in the years to come, as does the US government which, in February 2022, published a report detailing how the rise of UEFI malware was “an alarming trend” and such attacks seen in the wild “were previously only theoretical”.
Rootkits are an attractive tool for attackers because they are particularly difficult to locate and research, being embedded inside a motherboard’s firmware image. Because of this, they afford attackers significant capabilities thanks to a low risk of detection. It's likely that the computer will be infected with the rootkit forever, the report read.
The researchers were unable to determine how the victims initially became infected, but previous research from Qihoo360 on an early variant discovered in 2017 alleged that a victim may have bought an infected motherboard from a second-hand merchant, though this has not been confirmed.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
The researchers added that creating a rootkit of this quality is especially difficult, largely because a UEFI execution context terminates before Windows is loaded, making it harder for the UEFI code to be transposed into Windows.
The experts suggested it’s even more intriguing that the victims seemed to be private individuals, not tied to any organisation or industry, given the technical expertise required to build it.
Typically developers of malware would target high-value individuals in order to exfiltrate information, or deploy payloads such as ransomware in financially-driven campaigns.
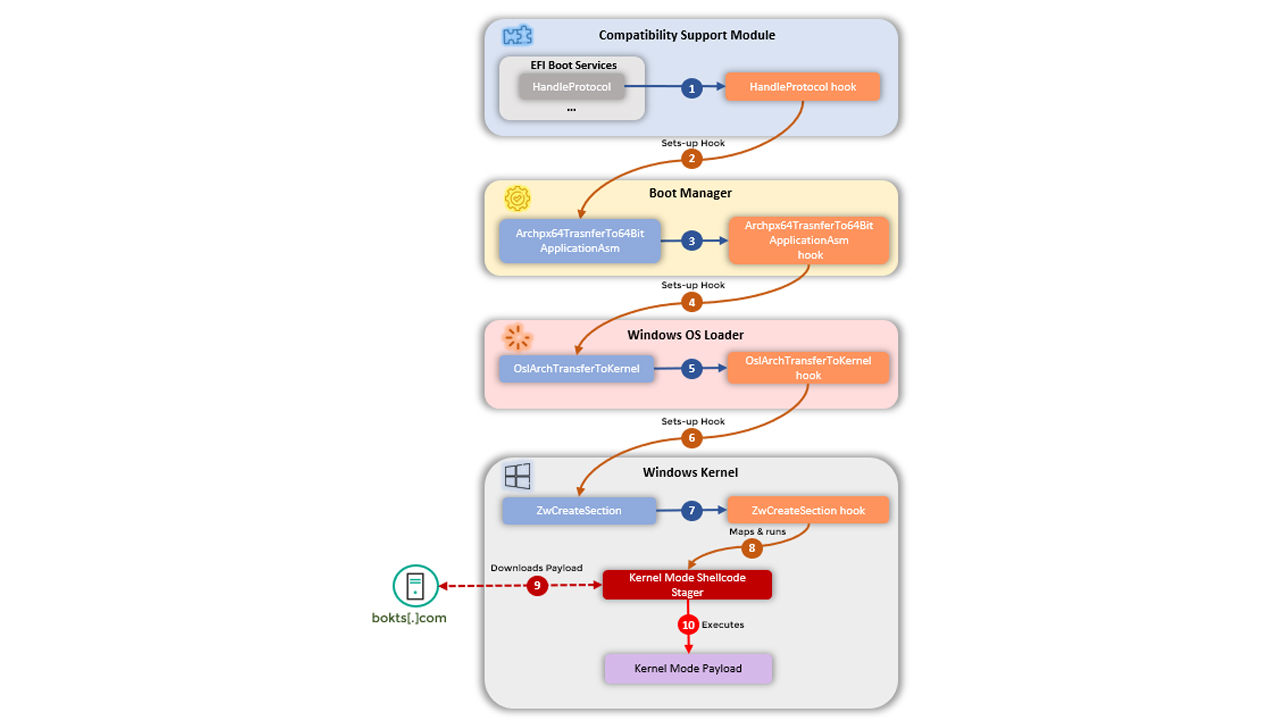
The kernel-level implant deploys a malicious component in Windows every time the operating system (OS) loads. After the infection chain is complete and the implant is connected to the cyber criminal’s C2 infrastructure, attackers can then feed malicious code to assemble into shellcode.
Kaspersky said it was able to capture and analyse an example of this shellcode but it believes many more exist that it wasn’t able to find.
From its analysis, the code appeared to attempt to create a new user on the victim’s machine. The researchers said it can be inferred from the shellcodes that they might be stagers for attacker-supplied portable executables - a Windows file format that wraps executable code, dynamic link libraries (DLLs) and other code for later use.
RELATED RESOURCE

The researchers said they are not certain regarding whom or what group they can attribute the attack to, but there is evidence to suggest a Chinese-speaking threat actor could be behind it.
The main reason Kaspersky believes a Chinese-speaking attacker could be behind it is the similarity in some code snippets between CosmicStrand and the MyKings botnet. Found in 2020 by ESET, the researchers said at the time they noticed several artefacts showing the Chinese language.
CosmicStrand and MyKings use the same MBR rootkit to establish persistence, both generate network packets in the same way and the API hashing code is also identical. The algorithm used here has only been observed twice by Kaspersky - in MoonBounce and xTalker - both of which are tied to Chinese-speaking threat actors, it said.
“The multiple rootkits discovered so far evidence a blind spot in our industry that needs to be addressed sooner rather than later,” said the researchers.
“The most striking aspect of this report is that this UEFI implant seems to have been used in the wild since the end of 2016… this discovery begs a final question: if this is what the attackers were using back then, what are they using today?”

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published