Sponsored by ANY.RUN
New Loader Masquerades as Antivirus to Deliver SSLoad
A new malware loader, PhantomLoader, disguises itself as an antivirus software module to deliver the evasive SSLoad malware, bypassing traditional security measures.

ANY.RUN, a leading provider of malware analysis and threat intelligence solutions, shared a technical analysis of a recent attack involving PhantomLoader being used to deliver SSLoad. SSLoad is a Rust-based malware known for its evasive and stealthy techniques.
In this attack, PhantomLoader is cleverly disguised as a legitimate module of an antivirus software, 360 Security Total, making it particularly difficult for traditional security tools to detect.
Overview of technical analysis
The analysis session ran inside ANY.RUN’s sandbox demonstrates how the drop and execution of PhantomLoader occurs, after which it decrypts and launches SSLoad.
Distribution via phishing emails
In many cases, PhantomLoader enters the system through phishing emails. These emails often contain malicious Office documents that initiate the infection process.
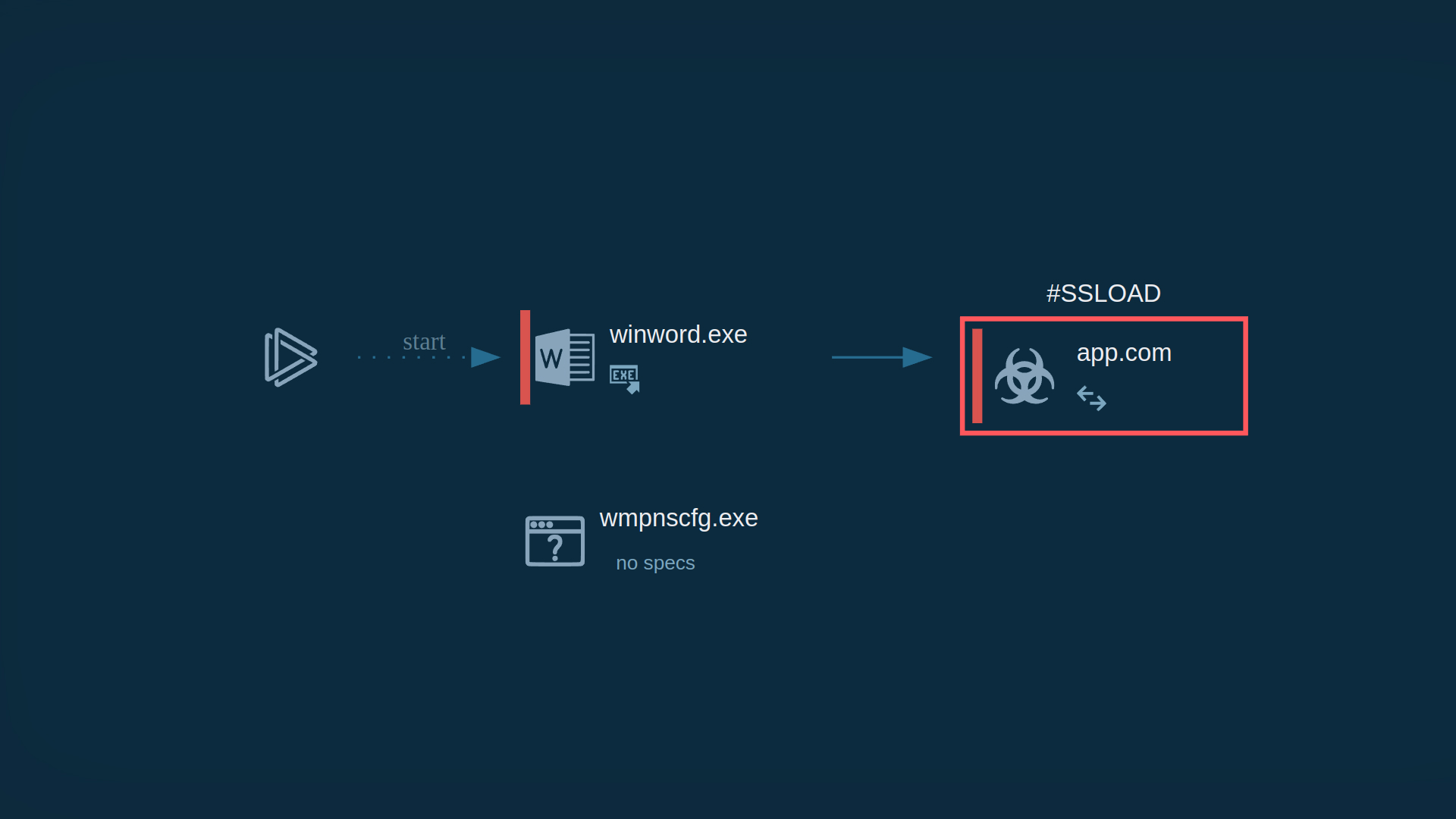
The ANY.RUN sandbox shows how Word document is used to deliver SSLoad
In this analysis, experts observed a suspicious Word document leading to the execution of a new process named “app.com,” triggered by “WINWORD.exe.” This process signifies the execution of a malicious macro embedded within the document.

Process details of the malicious Word document
Once the malicious document is opened, it executes a macro, leading to the creation of the suspicious process “app.com.”
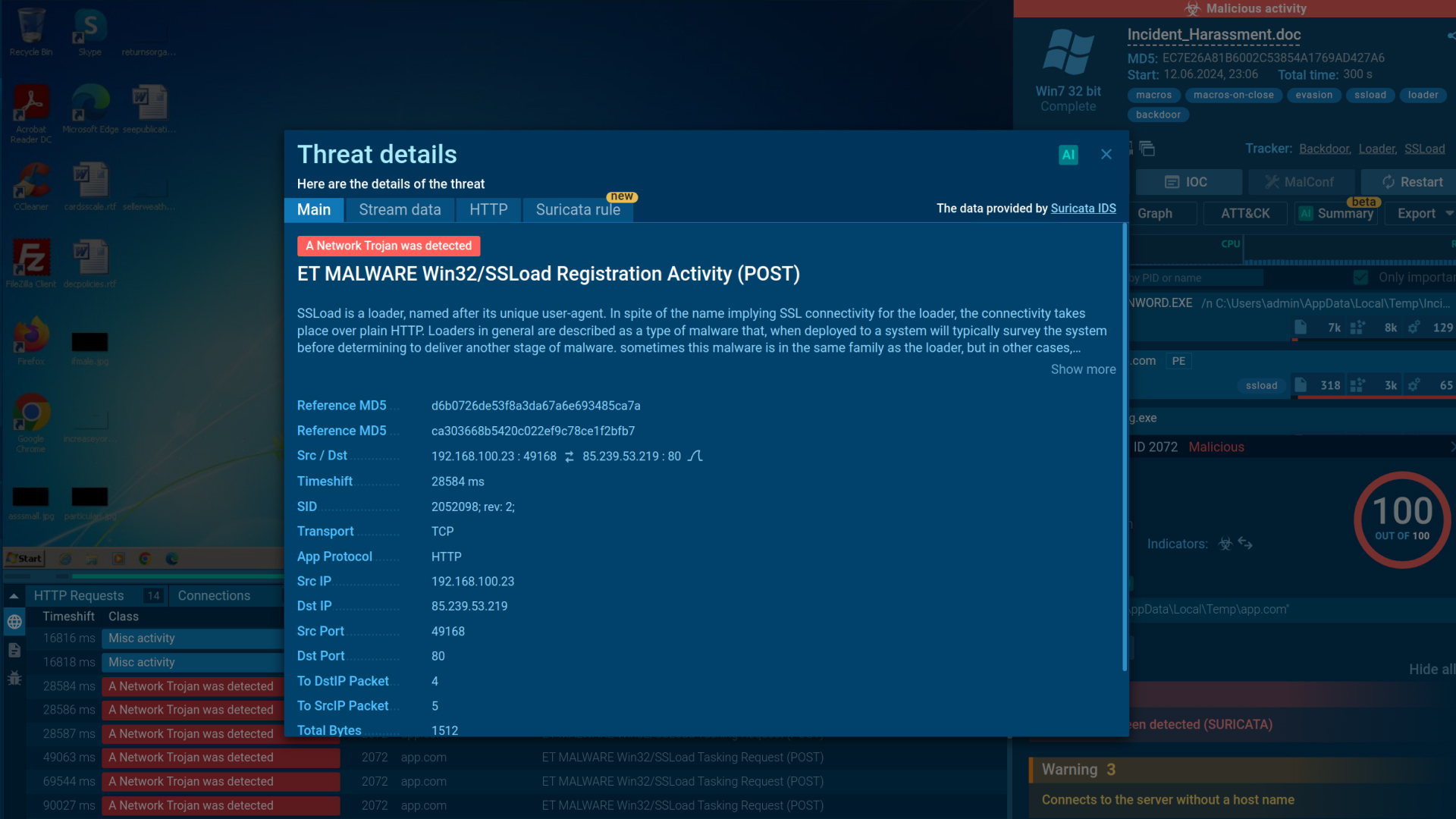
SSLoad malware detected by Suricata rule inside ANY.RUN’s sandbox
From here, PhantomLoader decrypts and launches SSLoad.
How PhantomLoader delivers SSLoad
PhantomLoader is a highly deceptive loader that uses advanced techniques to deliver SSLoad, making it difficult to detect. Disguised as a legitimate 32-bit module called PatchUp.exe for 360 Total Security, it bypasses security defenses by appearing as trusted software.
Self-modifying techniques
PhantomLoader uses self-modifying code techniques to conceal its true intentions. After it has successfully infiltrated the system, the loader decrypts an embedded code stub, which, in turn, decrypts SSLoad. By doing this in multiple steps, it hides the malicious payload until the last moment, making it much harder for traditional antivirus systems to catch it during the early stages of execution.
Execution of SSLoad
Once decrypted, SSLoad is delivered into the system's memory, ready to carry out its malicious activities. At this point, SSLoad begins employing its various evasion techniques.
SSLoad: A stealthy and evasive malware
SSLoad, the rust-based malware delivered by PhantomLoader, is particularly evasive. Once installed, it employs a variety of anti-debugging and anti-emulation tactics to hide its presence on the system.
Anti debugging techniques
One such method is its inspection of the Process Environment Block (PEB) to check the "BeingDebugged" flag, which would reveal if the process is currently under investigation by a debugger.
If the malware detects such monitoring, it may terminate itself or change its behavior to avoid being analyzed, effectively thwarting early detection attempts.
Anti-emulation tactics
SSLoad is also equipped with anti-emulation techniques to evade sandbox environments commonly used by security professionals. For instance, it looks for unusual functions like “MpVmp32Entry,” a function that only exists in modified versions of certain system libraries, which are often utilized in virtualized environments.
If this function is detected, the malware recognizes that it is operating in a virtual environment and can adjust its behavior to avoid detection.
String decryption and concealing C2 communication
ANY.RUN experts also detected that SSLoad uses multiple layers of string decryption to conceal its communication with command-and-control (C2) servers.
These advanced techniques make it challenging for security tools to detect the threat until it has already compromised a system.
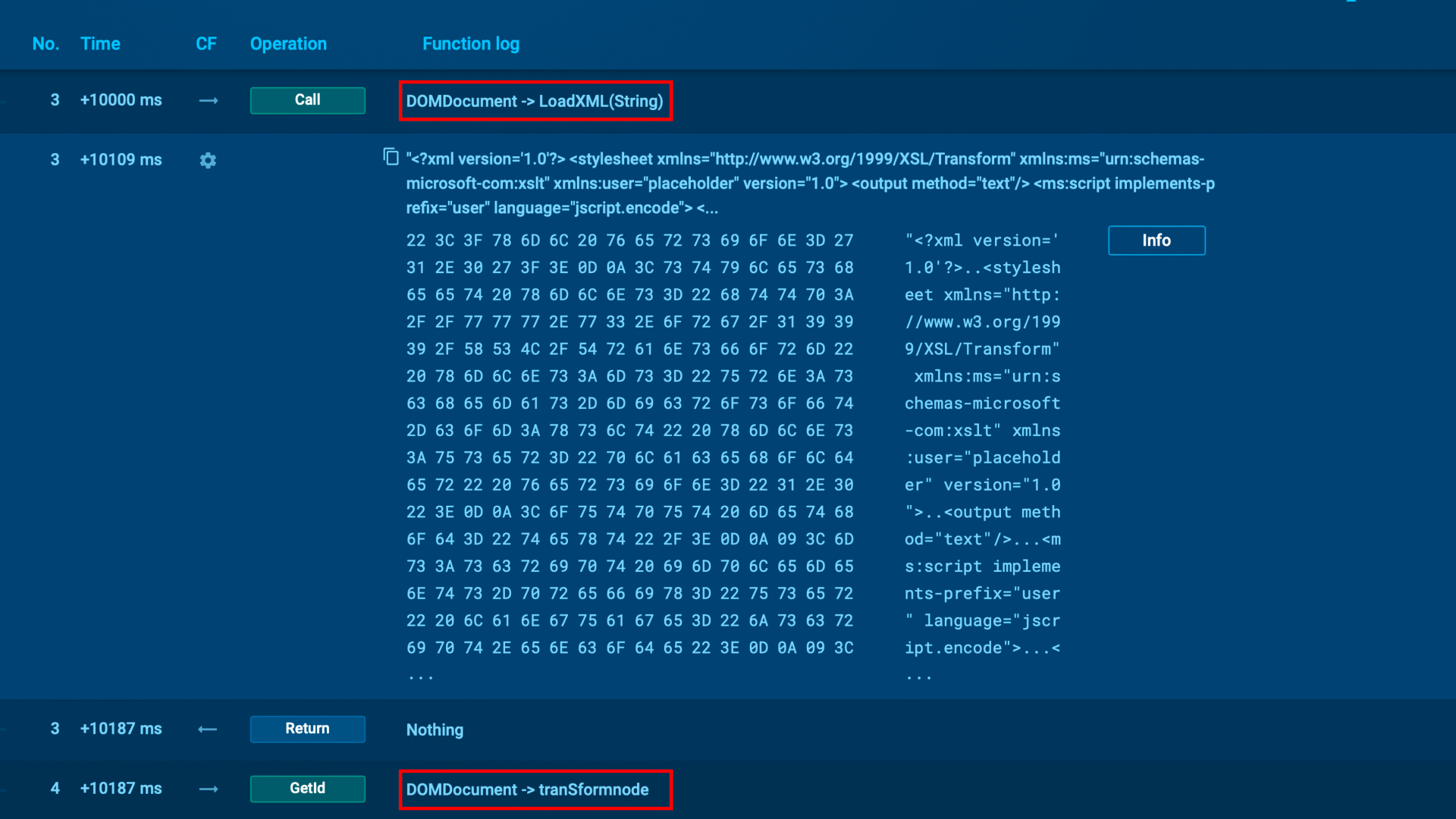
XML String load and execution demonstrated in ANY.RUN’s sandbox
Key Findings from ANY.RUN’s Analysis
- PhantomLoader disguises itself as a legitimate antivirus module: This deception allows it to evade detection while delivering SSLoad.
- Phishing emails remain a primary delivery method: Malicious Office documents initiate the infection chain.
- Advanced encryption and anti-analysis techniques: Both PhantomLoader and SSLoad employ sophisticated methods to remain hidden on infected systems.
Read the Full Analysis
For more details on how PhantomLoader and SSLoad operate, as well as indicators of compromise (IOCs) and technical breakdowns, read the full report on ANY.RUN’s blog.
Get Started with ANY.RUN's Interactive Sandbox
Interested in analyzing malware like PhantomLoader and SSLoad in a safe environment? Sign up for a 14-day free trial of ANY.RUN’s interactive sandbox to see how it can enhance your organization’s cybersecurity defenses.
Start your 14-day free trial now
Copyright Disclaimer: All rights to the illustrations and other images used in this article belong to ANYRUN-FZCO.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
ITPro is a global business technology website providing the latest news, analysis, and business insight for IT decision-makers. Whether it's cyber security, cloud computing, IT infrastructure, or business strategy, we aim to equip leaders with the data they need to make informed IT investments.
For regular updates delivered to your inbox and social feeds, be sure to sign up to our daily newsletter and follow on us LinkedIn and Twitter.
-
 Should AI PCs be part of your next hardware refresh?
Should AI PCs be part of your next hardware refresh?AI PCs are fast becoming a business staple and a surefire way to future-proof your business
By Bobby Hellard Published
-
 Westcon-Comstor and Vectra AI launch brace of new channel initiatives
Westcon-Comstor and Vectra AI launch brace of new channel initiativesNews Westcon-Comstor and Vectra AI have announced the launch of two new channel growth initiatives focused on the managed security service provider (MSSP) space and AWS Marketplace.
By Daniel Todd Published
