Malware
Discover expert analysis on malware with news, features and insights from the team at IT Pro.
-
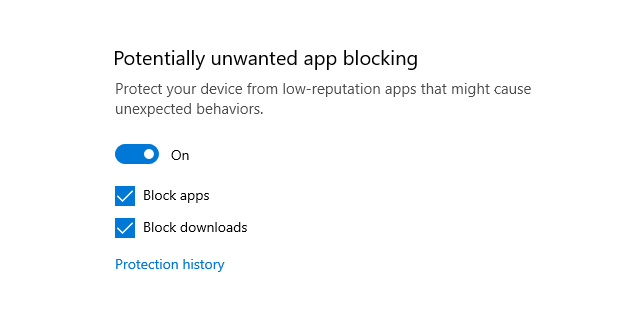
Windows 10 to start blocking potentially unwanted apps by default
News Previously, users who wanted to use the blocking feature had to turn it on in the App & browser control settings
By Sabina Weston Published
News -

Hackers turning to 'exotic' languages for next-gen malware, report warns
News Coding languages such as Go, Rust, Nim and DLang are allowing malware authors to avoid signature detection and add layers of obfuscation
By Keumars Afifi-Sabet Published
News -

CISA warns of disguised malware on hacked Pulse Secure devices
News CISA lists several tasks administrators can complete to boost security
By Rene Millman Published
News -

The five essentials from your endpoint security partner
Whitepaper Empower your MSP business to operate efficiently
By ITPro Published
Whitepaper -

New malware uses search engine ads to target pirate gamers
News MosaicLoader uses advanced obfuscation techniques to avoid detection
By Danny Bradbury Published
News -

Hackers abuse single bit change in Intel CPU register to evade detection
News Palo Alto Networks discovers that Trap Flag is being abused to notify malware it is being analyzed
By Rene Millman Published
News -

TA551/Shathak threat research
Whitepaper A detailed report on the cyber crime group and its attacks
By ITPro Published
Whitepaper -

Indexsinas SMB worm is targeting Windows servers vulnerable to EternalBlue
News The self-propagating vulnerability remains a threat despite being patched years ago
By Rene Millman Published
News -

Western Digital to provide recovery services for hacked NAS drives
News Users affected by the cyber attack will be able to upgrade to a new My Cloud device
By Sabina Weston Published
News -

Android devs must now provide personal details and use 2FA
News Google sets out stricter requirements for Play Store developers to limit malicious apps uploaded to the Android marketplace
By Keumars Afifi-Sabet Published
News -

Western Digital NAS drive owners told to unplug their devices after malware attacks
News Company confirms spate of factory resets were triggered remotely
By Sabina Weston Published
News -

Weekly threat roundup: Windows, Chrome, VMware
News Pulling together the most dangerous and pressing flaws that businesses need to patch
By Keumars Afifi-Sabet Published
News