Microsoft under fire for “negligent” security practices in scathing critique by industry exec
Microsoft took more than 90 days to issue a partial fix for a critical Azure vulnerability, researchers found


Tenable CEO Amit Yoran has accused Microsoft of "negligent practices” for its response to security vulnerabilities in a scathing critique of the tech giant.
Yoran criticized Microsoft’s alleged “lack of transparency” regarding data breaches and security vulnerabilities, suggesting that the company has deliberately kept customers in the dark.
This criticism focuses specifically on the tech giant’s response to a recent Chinese-backed cyber espionage campaign which targeted senior US government officials.
The incident enabled threat actors to access officials’ emails, and at the time Microsoft said the attack was part of a targeted campaign against the US.
Last week, US senator Ron Wyden penned a letter calling Microsoft “negiligent” in its response to the attacks and called on the Justice Department to investigate whether the company’s approach broke the law.
Yoran echoed Wyden’s comments in his broadside against the firm, claiming that the company’s track record on security is “even worse than we thought”.
“Microsoft’s lack of transparency applies to breaches, irresponsible security practices, and to vulnerabilities, all of which expose their customers to risks they are deliberately kept in the dark about,” he said.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
RELATED RESOURCE
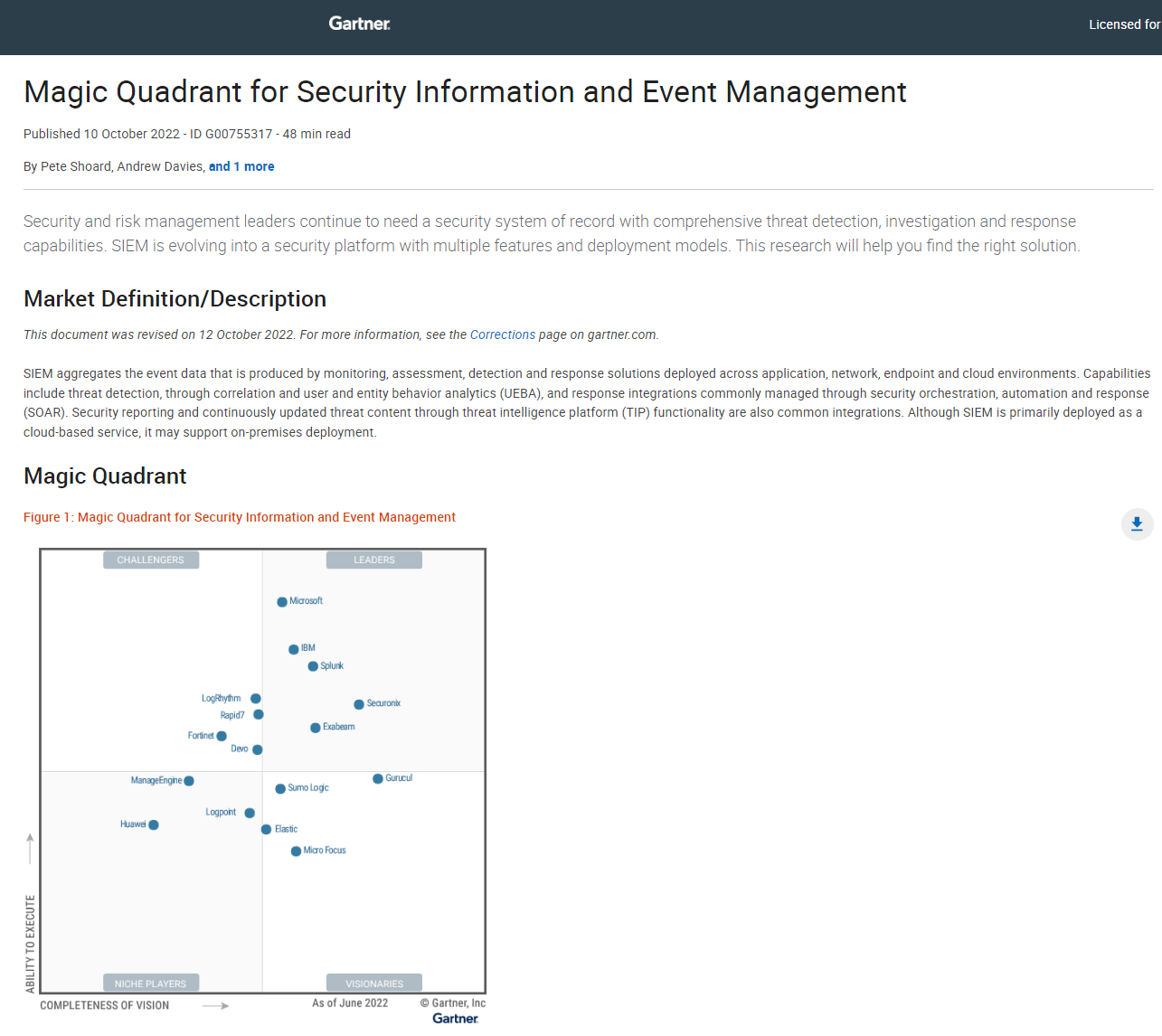
Magic quadrant for Security Information and Event Management (SIEM)
This report assesses the current SIEM solutions in the market, looking at threat detection and response capabilities.
“What you hear from Microsoft is ‘just trust us’, but what you get back is very little transparency and a culture of toxic obfuscation.
“How can a CISO, board of directors, or executive team believe that Microsoft will do the right thing given the fact patterns and current behaviors? Microsoft’s track record puts us all at risk. And it’s even worse than we thought,” Yoran added.
In March this year, Tenable researchers uncovered a vulnerability in Microsoft’s Azure platform that would enable attackers to access applications and sensitive data, such as authentication secrets.
Yoran pointed to this incident as an example of Microsoft’s alleged negligent practices, noting that it took more than 90 days to implement a “partial fix” after researchers notified the firm.
“To give you an idea of how bad this is, our team very quickly discovered authentication secrets to a bank,” Yoran said. “They were so concerned about the seriousness and the ethics of the issue that we immediately notified Microsoft.”
“Did Microsoft quickly fix the issue that could effectively lead to the breach of multiple customers' networks and services? Of course not. They took more than 90 days to implement a partial fix – and only for new applications loaded in the service.”
Is Microsoft truly ‘negligent’?
Yoran’s public criticism of Microsoft raises questions over the company’s approach to security in recent years. According to data from Google Project Zero, Microsoft products have accounted for around 42.5% of all zero days discovered since 2014.
While these statistics might raise eyebrows, the scale of Microsoft’s global footprint does indeed put things into perspective. Microsoft software is used by more than 1.4 billion people globally, including millions of organizations such as US government departments.
Within that context, Microsoft being responsible for a significant volume of zero days doesn’t point to outright negligence, but more of a byproduct of its size and scope of integration within organizations.
Jake Moore, global cyber security advisor at ESET, told ITPro that although the firm may seem to be turning a blind eye to known vulnerabilities, critics must remember that updates from vendors large and small are all known to cause issues, not just Microsoft’s.
“Keeping systems completely secure is a challenging role, if not impossible, but it is best approached using as many layers of defense as possible,” he said.
“Zero days naturally need vital attention but when attackers strike it can be relentless and often on large swathes making patches that much more difficult to produce, control, and distribute.”
However, Moore added that the length of time between vulnerability disclosure and remediation in the Tenable research should be a cause for concern for organisations.
“Over 100 days is naturally concerning for clients but this is yet another important reminder that no one single security measure will protect entities on their own and multiple defenses are required to remain best protected.”

Ross Kelly is ITPro's News & Analysis Editor, responsible for leading the brand's news output and in-depth reporting on the latest stories from across the business technology landscape. Ross was previously a Staff Writer, during which time he developed a keen interest in cyber security, business leadership, and emerging technologies.
He graduated from Edinburgh Napier University in 2016 with a BA (Hons) in Journalism, and joined ITPro in 2022 after four years working in technology conference research.
For news pitches, you can contact Ross at ross.kelly@futurenet.com, or on Twitter and LinkedIn.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published
-
 Hackers are targeting Ivanti VPN users again – here’s what you need to know
Hackers are targeting Ivanti VPN users again – here’s what you need to knowNews Ivanti has re-patched a security flaw in its Connect Secure VPN appliances that's been exploited by a China-linked espionage group since at least the middle of March.
By Emma Woollacott Published
-
 Broadcom issues urgent alert over three VMware zero-days
Broadcom issues urgent alert over three VMware zero-daysNews The firm says it has information to suggest all three are being exploited in the wild
By Solomon Klappholz Published
-
 Nakivo backup flaw still present on some systems months after firms’ ‘silent patch’, researchers claim
Nakivo backup flaw still present on some systems months after firms’ ‘silent patch’, researchers claimNews Over 200 vulnerable Nakivo backup instances have been identified months after the firm silently patched a security flaw.
By Solomon Klappholz Published
-
 Everything you need to know about the Microsoft Power Pages vulnerability
Everything you need to know about the Microsoft Power Pages vulnerabilityNews A severe Microsoft Power Pages vulnerability has been fixed after cyber criminals were found to have been exploiting unpatched systems in the wild.
By Solomon Klappholz Published
-
 Vulnerability management complexity is leaving enterprises at serious risk
Vulnerability management complexity is leaving enterprises at serious riskNews Fragmented data and siloed processes mean remediation is taking too long
By Emma Woollacott Published
-
 A critical Ivanti flaw is being exploited in the wild – here’s what you need to know
A critical Ivanti flaw is being exploited in the wild – here’s what you need to knowNews Cyber criminals are actively exploiting a critical RCE flaw affecting Ivanti Connect Secure appliances
By Solomon Klappholz Published
-
 Researchers claim an AMD security flaw could let hackers access encrypted data
Researchers claim an AMD security flaw could let hackers access encrypted dataNews Using only a $10 test rig, researchers were able to pull off the badRAM attack
By Solomon Klappholz Published
-
 The threat prevention buyer's guide
The threat prevention buyer's guideWhitepaper Find the best advanced and file-based threat protection solution for you
By ITPro Published