Microsoft exposes BulletProofLink 'phishing as a service' criminal enterprise
The sophisticated outfit handles everything from template design to web hosting and credentials processing
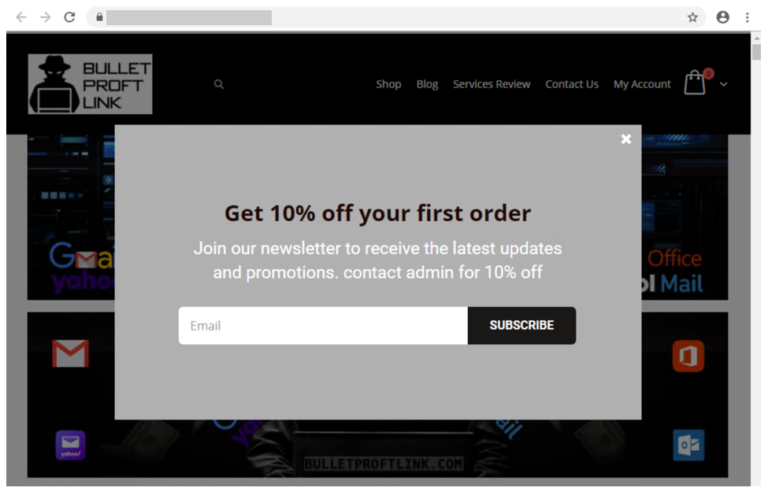

Microsoft has revealed the inner workings of a highly sophisticated phishing as a service (PhaaS) criminal enterprise that hosts and distributes tools and services for use in a customer's phishing campaigns.
BulletProofLink follows the legitimate software as a service (SaaS) business subscription model but engages in the end-to-end development and distribution of tools to run phishing campaigns, according to Microsoft. The services are said to include tools for creating false sign-in pages, web hosting, and credential redistribution.
While standard phishing kits offer email templates and site templates for a one-off payment, PhaaS is a subscription-based model that offers these services as a baseline. Customers can pay for a host of additional services in a modular way, including email delivery, site hosting, credential theft, and services that redistribute those stolen credentials to customers automatically.
BulletProofLink’s clients engage in these services to harvest user credentials, rather than to distribute malware or ransomware strains. The operators also keep a copy of the credentials all customers steal through their campaigns, which they resell at a later stage.
“It’s worth noting that some PhaaS groups may offer the whole deal - from template creation, hosting, and overall orchestration, making it an enticing business model for their clientele,” said the Microsoft 365 Defender threat intelligence team.
“These phishing service providers host the links and pages and attackers who pay for these services simply receive the stolen credentials later on. Unlike in certain ransomware operations, attackers do not gain access to devices directly and instead simply receive untested stolen credentials.”
Microsoft researchers dug deep into the templates, services, and pricing structures offered by BulletProofLink operators, which appear to have been active since 2018. They also maintain multiple sites under several aliases including BulletPoftLink and Anthrax, alongside YouTube and Vimeo pages with instructional adverts, as well as promotional content hosted on external forums.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
The operation attempts to mimic the behaviour of legitimate businesses, including registration and sign-in pages and an online store, the latter of which can be used by other hackers to advertise their own services for a monthly subscription fee. The group even boasts of a 10% welcome discount for customers who subscribe to BulletProofLink’s newsletter.
RELATED RESOURCE

The business guide to ransomware
Everything you need to know to keep your company afloat
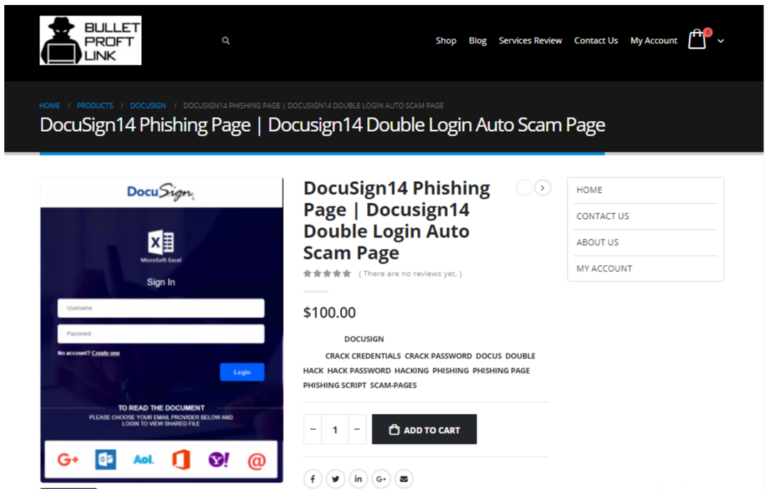
As a core component of the business, the operators offer more than 100 templates, with clients free to control other elements of the phishing operation themselves or use the full suite of BulletProofLinks services. For example, they might only buy the template and manage the flow of password collection independently by registering their own landing pages, or they can let BulletProofLink handle everything.
The monthly services offered vary in price from $50 dollars to $800 dollars, with most fees paid using Bitcoin. The operators also provide customer support services for all new and existing clients.
This operation echoes the ransomware as a service (RaaS) phenomenon, which features many of the same structures and processes of a legitimate software company. This is also true for the way the organisation monetises data, according to Microsoft.
The standard practice with ransomware attacks involves cyber criminals exfiltrating data and threatening to post it publicly while also encrypting devices locally and demanding ransom, as a means of ‘double extortion’.
PhaaS operations follow a similar workflow in terms of stolen credentials, with BulletProofLink maintaining a log of all information stolen as part of phishing campaigns. On top of the subscription fees they receive, they resell these credentials to other organisations at a later stage for an additional sum, with victims being exposed twice.

Keumars Afifi-Sabet is a writer and editor that specialises in public sector, cyber security, and cloud computing. He first joined ITPro as a staff writer in April 2018 and eventually became its Features Editor. Although a regular contributor to other tech sites in the past, these days you will find Keumars on LiveScience, where he runs its Technology section.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published