Microsoft releases analysis of Web3 'ice phishing' attack
New phishing method targets an immature technology stack on the next generation of the internet


Microsoft’s 365 Defender Research Team has detailed the latest strain of phishing attacks designed to target the nascent technology underpinning Web3 – the so-called decentralised third generation of the internet.
Dubbed ‘ice phishing’, the attack method involves hijacking the normal approval process that handles the secure transaction of tokens, such as cryptocurrency, over a blockchain.
Ice phishing was first observed by Microsoft between November and December 2021 when the Badger DAO platform was hacked and $121 million worth of users’ assets were stolen.
Badger DAO is a platform that allows users to deposit Bitcoin and earn interest on their deposits using a variety of yield farming strategies. It uses a decentralised finance (DeFi) protocol called Badger and currently has $978 million total volume locked, according to Microsoft.
The Ethereum blockchain, on which the Badger DAO attack occured, hosts cryptocurrencies that use the ERC-20 standard to create and issue smart contracts that can be then used to securely transfer assets over the blockchain.
This standard can be seen as a set of functions that, when executed, facilitate a blockchain transaction. One of these functions is to initiate a smart contract that moves assets on behalf of the user.
The owner of the asset is automatically approved to make the transaction but they can also delegate approval to additional entities such as smart contracts. It's this process that ice phishing aims to exploit.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
How ice phishing works
Historical methods of stealing assets from secured cryptocurrency wallets have typically relied on social engineering to deceive users into relinquishing their private keys to the attacker, allowing them to access their wallet and drain the funds.
RELATED RESOURCE

Modernise your server infrastructure for speed and security
Infrastructure lifecycle automation paves the way for an adaptive, resilient organisation
Ice phishing does not involve stealing a user’s private keys. Instead, it involves tricking a user into signing a transaction that delegates approval of the user’s tokens to the attacker.
In the case of the Badger DAO attack, the platform’s front-end infrastructure was compromised which allowed the attacker to inject malicious code into the Badger smart contract front end. This code requested users to sign transactions granting ERC-20 approvals to the attacker’s account.
As is often the case with these types of platforms, the user interface (UI) for Badger DAO does not show enough information to indicate whether a transaction has been tampered with, according to Microsoft.
Attackers both compromise these platforms’ infrastructures and leverage the basic UI to fool users into granting transaction approval to the attacker’s wallet.
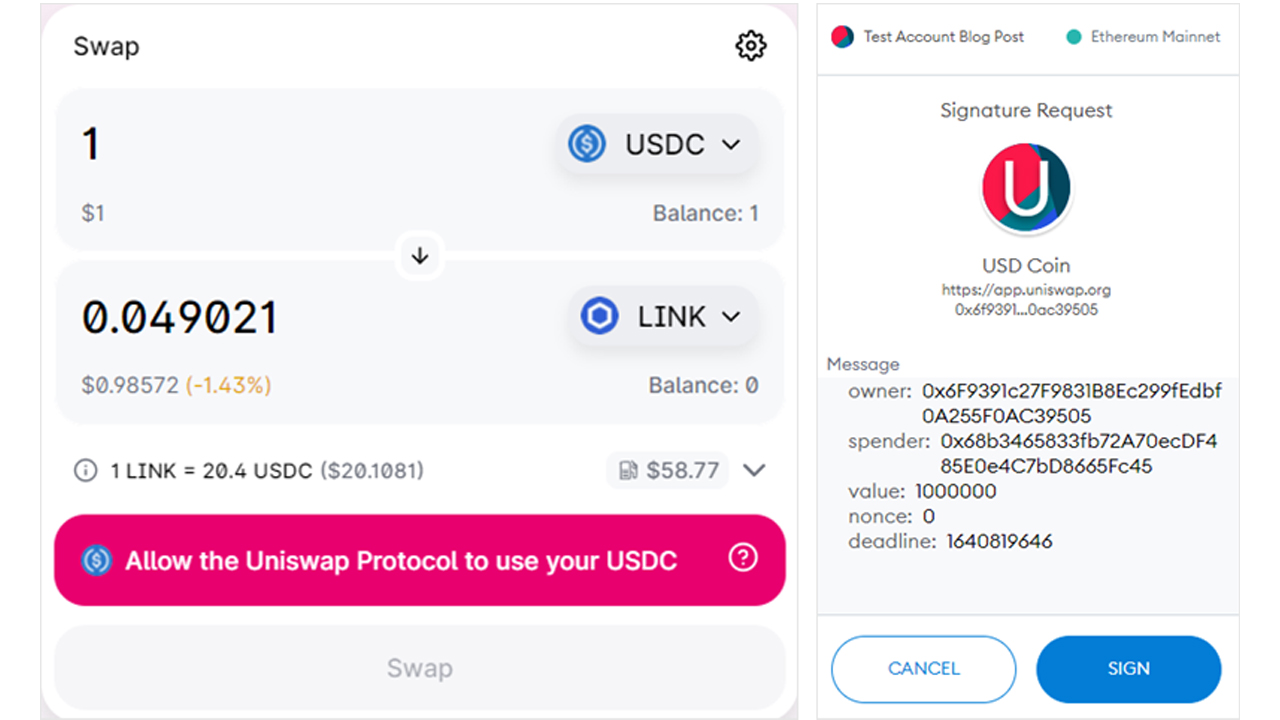
Using a transaction on the Uniswap platform – a decentralised token exchange allowing users to swap Ethereum-based cryptocurrency tokens for other tokens – as an example, Microsoft showed the typical UI presented to the user, and how the information needed to determine if a transaction has been tampered with is usually hidden.
In the above example, the user isn’t able to determine if the ‘spender’ - the account to be authorised - is the router owned by the platform or an address owned by an attacker.
“Once the approval transaction has been signed, submitted, and mined, the spender can access the funds,” said Microsoft. “In case of an ice phishing attack, the attacker can accumulate approvals over a period of time and then drain all victim’s wallets quickly.
“This is exactly what happened with the Badger DAO attack that enabled the attacker to drain millions of US dollars in November-December 2021.”
Future Web3 risks
Microsoft said the Web3 stack is still in its infancy and as such, bears risks for users. The Badger DAO attack was significant and one of the largest hacks of its kind in terms of the number of assets stolen.
Attacks like these are likely to continue, said Microsoft, though transactions of this kind, on the blockchain, are public which makes investigating the incidents easier.
Identifying such attacks is possible and can even be automated. A public blockchain also allows investigators to see how much has been stolen – something that is typically difficult in traditional, web2-based phishing attacks.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Bigger salaries, more burnout: Is the CISO role in crisis?
Bigger salaries, more burnout: Is the CISO role in crisis?In-depth CISOs are more stressed than ever before – but why is this and what can be done?
By Kate O'Flaherty Published
-
 Cheap cyber crime kits can be bought on the dark web for less than $25
Cheap cyber crime kits can be bought on the dark web for less than $25News Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott Published