BRATA malware has evolved to target online banking across Europe, researchers warn
The new variant can now access SMS, GPS, and device control to better steal financial data


An Android malware strain, known for its attacks on the Google Play store, has been spotted targeting the login pages of online banks, in what experts believe is a long-term shift in strategy by its developers.
The Brazilian Remote Access Tool (BRATA) first surfaced in 2018, targeting Android users with fake antivirus apps and similar security software in an effort to steal credentials.
RELATED RESOURCE

The Total Economic Impact™ of Mimecast
Cost savings and business benefits enabled by using Mimecast with Microsoft 365
FREE DOWNLOAD
However, new attacks suggest the group behind the malware has pivoted towards targeting financial institutions directly, attempting to put fake login pages in front of users trying to access online banking services.
The new variant has been flagged by the cyber security organisation Cleafy, who provided screenshots of a phishing page new to BRATA that mimics the login field for a prominent bank, asking users to input their PIN and client number.
“They usually focus on delivering malicious applications targeted to a specific bank for a couple of months, and then moving to another target,” Cleafy explained in a blog post on the discovery.
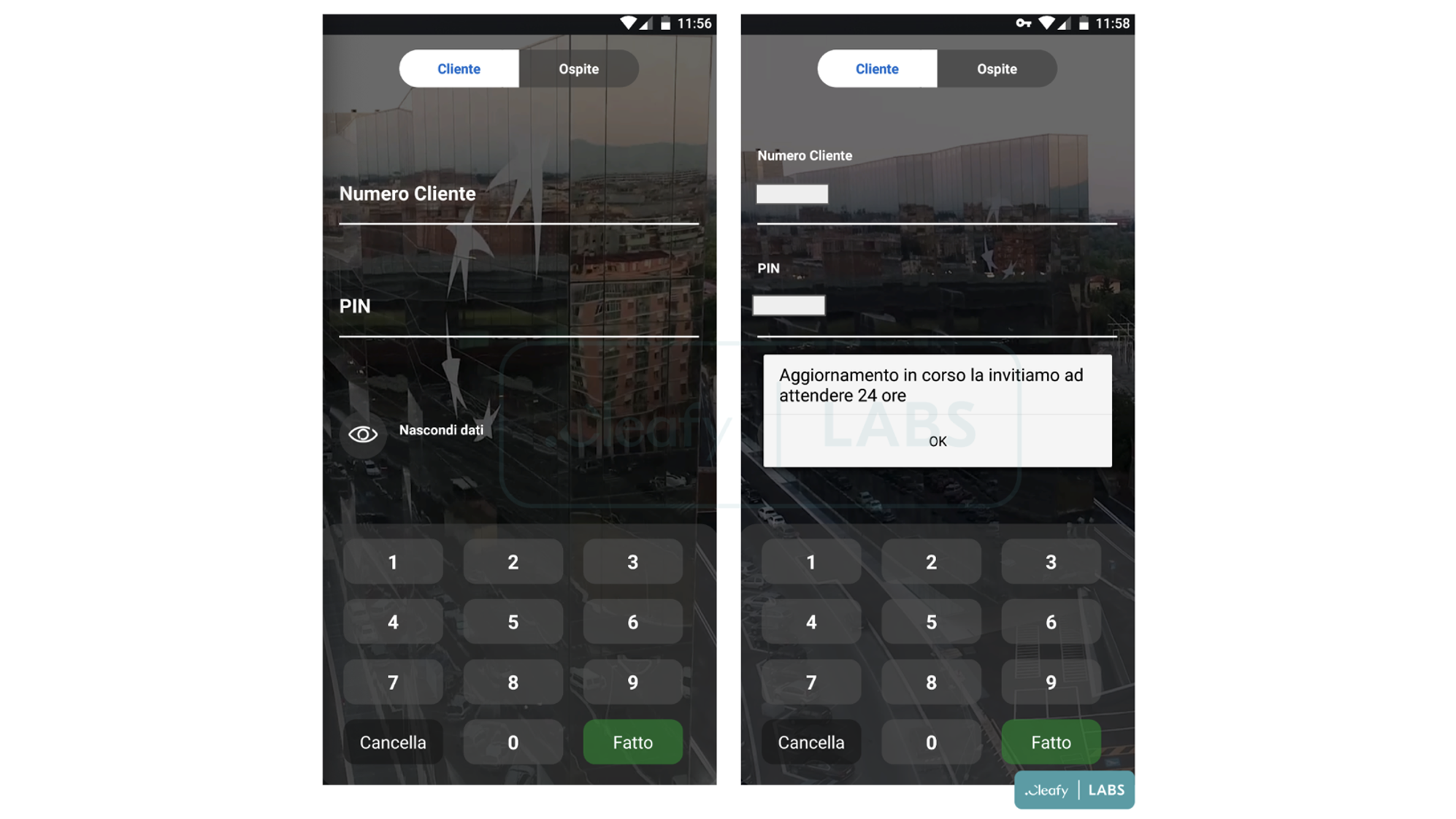
Moves to socially engineer the customers of specific banks indicate that BRATA’s threat actors are curating their pool of targets. Formerly localised to South America, efforts to steal financial information have resulted in a shift in focus towards users across mainland Europe and the UK, with Italy-based Cleafy first discovering the variant through increased activity across the region.
The evolution has also seen the introduction of new features, which allow the strain to seek permissions over SMS, GPS, and device management. Additionally, on install an event-logger plugin labelled 'unrar.jar' is downloaded from the BRATA command and control (C2) infrastructure. Cleafy expressed concerns that these additions “could be used to perform a complete Account Takeover (ATO) attack”.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
At time of writing, targeted devices do not appear to be exchanging information with the threat actors behind the malware, and that this may indicate that the newest variant BRATA.A is still undergoing development, according to researchers.
However, the organisation has already identified a separate SMS stealer app connected to the BRATA C2 infrastructure, also targeting users in mainland Europe and the UK. With threat actors testing out new attack vectors linked by a common framework, there are fears that, once active, this variant could prove effective at taking over users’ financial accounts.
For this reason, Cleafy has assigned BRATA an Advanced Persistent Threat (APT) status, which they define as “an attack campaign in which criminals establish a long-term presence on a targeted network to steal sensitive information".
As malware evolves to deceive in more sophisticated ways, it is important that users keep up to date with threat prevention tactics, and only download apps from trusted sources.

Rory Bathgate is Features and Multimedia Editor at ITPro, overseeing all in-depth content and case studies. He can also be found co-hosting the ITPro Podcast with Jane McCallion, swapping a keyboard for a microphone to discuss the latest learnings with thought leaders from across the tech sector.
In his free time, Rory enjoys photography, video editing, and good science fiction. After graduating from the University of Kent with a BA in English and American Literature, Rory undertook an MA in Eighteenth-Century Studies at King’s College London. He joined ITPro in 2022 as a graduate, following four years in student journalism. You can contact Rory at rory.bathgate@futurenet.com or on LinkedIn.
-
 Should AI PCs be part of your next hardware refresh?
Should AI PCs be part of your next hardware refresh?AI PCs are fast becoming a business staple and a surefire way to future-proof your business
By Bobby Hellard Published
-
 Westcon-Comstor and Vectra AI launch brace of new channel initiatives
Westcon-Comstor and Vectra AI launch brace of new channel initiativesNews Westcon-Comstor and Vectra AI have announced the launch of two new channel growth initiatives focused on the managed security service provider (MSSP) space and AWS Marketplace.
By Daniel Todd Published
-
 Have I Been Pwned owner Troy Hunt’s mailing list compromised in phishing attack
Have I Been Pwned owner Troy Hunt’s mailing list compromised in phishing attackTroy Hunt, the security blogger behind data-breach site Have I Been Pwned, has fallen victim to a phishing attack targeting his email subscriber list.
By Jane McCallion Published
-
 LinkedIn has become a prime hunting ground for cyber criminals – here’s what you need to know
LinkedIn has become a prime hunting ground for cyber criminals – here’s what you need to knowNews Cyber criminals are flocking to LinkedIn to conduct social engineering campaigns, research shows.
By Solomon Klappholz Published
-
 Phishing campaign targets developers with fake CrowdStrike job offers
Phishing campaign targets developers with fake CrowdStrike job offersNews Victims are drawn in with the promise of an interview for a junior developer role at CrowdStrike
By Solomon Klappholz Published
-
 Iranian hackers targeted nuclear expert, ported Windows infection chain to Mac in a week
Iranian hackers targeted nuclear expert, ported Windows infection chain to Mac in a weekNews Fresh research demonstrates the sophistication and capability of state-sponsored threat actors to compromise diverse targets
By Richard Speed Published
-
 Malware being pushed to businesses by search engines remains a pervasive threat
Malware being pushed to businesses by search engines remains a pervasive threatNews High-profile malvertising campaigns in recent months have surged
By Ross Kelly Published
-
 CISA: Phishing campaign targeting US federal agencies went undetected for months
CISA: Phishing campaign targeting US federal agencies went undetected for monthsNews Threat actors used legitimate remote access software to maliciously target federal employees
By Rory Bathgate Published
-
 Google Ads malvertising campaign prompts questions around Search security
Google Ads malvertising campaign prompts questions around Search securityNews A leading security researcher has called into question why Google still allows malware links to top search results
By Rory Bathgate Published
-
 Uber hacked via basic smishing attack
Uber hacked via basic smishing attackNews The self-taught hacker impersonated an IT worker to gain an Uber employee's password, obtaining broad access to internal systems and posting taunting messages
By Rory Bathgate Published