Ransomware activity down 11% worldwide in Q3, but rise expected
LockBit increased its share of the landscape even as attacks declined, while new groups have capitalised on the fall of Conti


A new report has found that global ransomware activity dropped throughout the third quarter as the order of dominant groups in the landscape shifted, but that businesses should expect a surge by threat actors in Q4 to exploit consumer trends.
RELATED RESOURCE

How to reduce the risk of phishing and ransomware
Top security concerns and tips for mitigation
The number of ransomware attacks in Q3 2022 was down 10.5% on Q2, according to the latest report by cyber security firm Digital Shadows. This was driven in part by the sudden cessation of activity by the Conti group, as well as a reorganisation of leading groups over July and August.
LockBit 3.0, the latest strain by the LockBit group of threat actors, consolidated its lead across the landscape in Q3, accounting for 35.1% of all activity across the period, compared to 32.8% in Q2. The group's rise, even as its overall activity declined, has been matched by the growth of a number of new groups, including Black Basta, Hive Leaks, and Alphv, which account for 9%, 8%, and 7% of activity respectively.
Digital Shadows suggests that these groups have directly taken advantage of the gap in the market left by Conti, which after threatening to overthrow the Costa Rican government in May, apparently shut down in June. The group’s website has disappeared, and a drop off in activity right at the end of Q2 has been linked directly to the group’s apparent cessation of attacks.
Groups that bucked the trend with increased activity across the period include ‘AvosLocker’ (up 50%) and Hive Leaks (up 80.8%). The latter operates the Hive payload, which was singled out by Microsoft in Q3 for its sophisticated functions, and for being written in the programming language Rust, which is becoming a popular programming language for hacker groups.
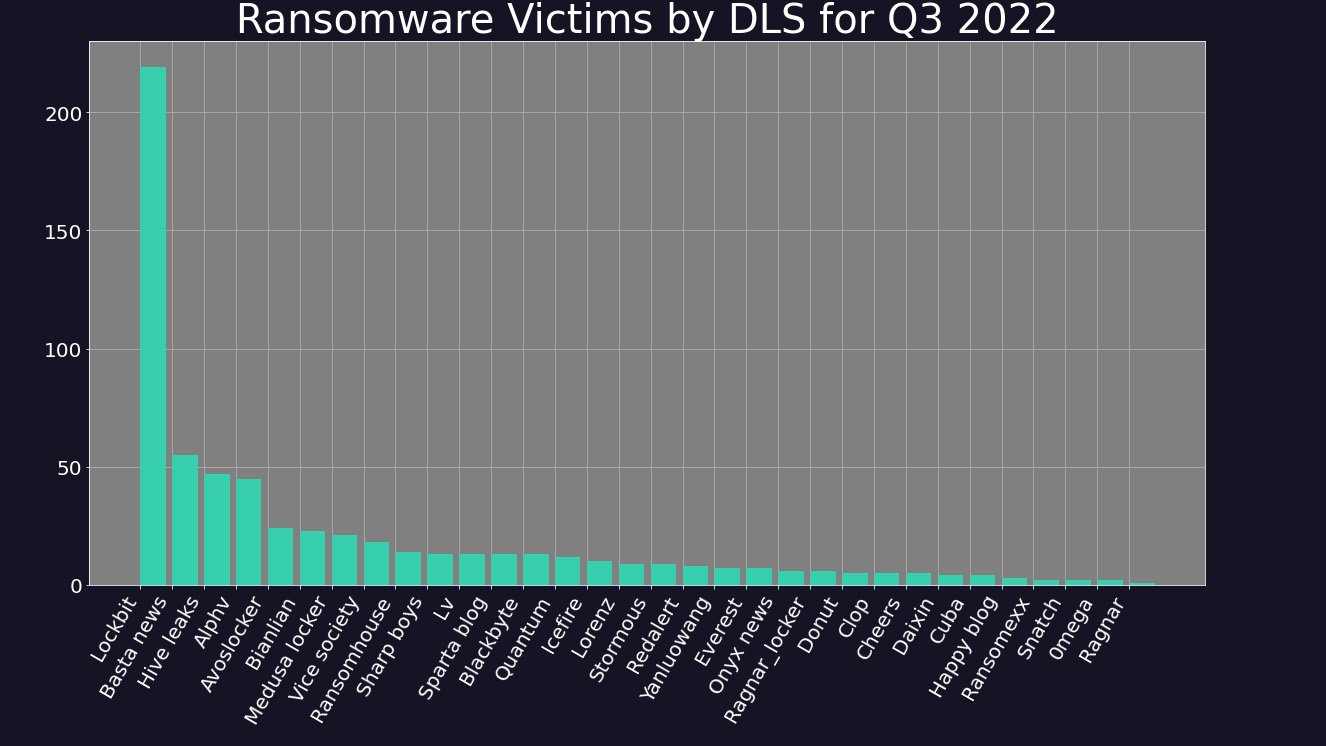
Some within the cyber security community have suggested that Hive is composed of former Conti actors, or is even a continuation of the same group. Investigative journalist and cyber crime expert Brian Krebs tweeted that attacks on Costa Rica appeared to have been committed by Hive, but that “with Conti apparently in the process of rebranding, it could just as well be the same criminals involved.”
However, Emisoft threat analyst Brett Callow subsequently tweeted a screenshot from Hive’s website that states “we are not related with Conti”. No evidence yet links any emerging group with Conti.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Around 39% of all attacks across Q3 were made against victims within the United States, reflective of the consolidation of wealthy companies within the country. France and Spain followed, with the UK the fourth most targeted in the same period, accounting for 4.8% of victims. This marks a fall from the UK’s third place in Q2, and appears to have been driven by a surge in attacks in France and Spain, including Hive's attack on French telco giant Altice in August.
Indeed, while almost all countries saw decreased ransomware attacks in Q3, France, Spain and Israel saw rises. Spain was an outlier, with a 66% rise in ransomware activity across the quarter tied to a surge by the group ‘Sparta Blog.’
The industrial goods and services sector remained the most targeted sector throughout the period, recording nearly double the attacks of the technology sector, the next most targeted. As the war in Ukraine drags on, attacks on supply chains and critical national infrastructure (CNI) continue to rise, and state-backing of ransomware attacks will continue to increase such action.
Bracing for a rise in Q4
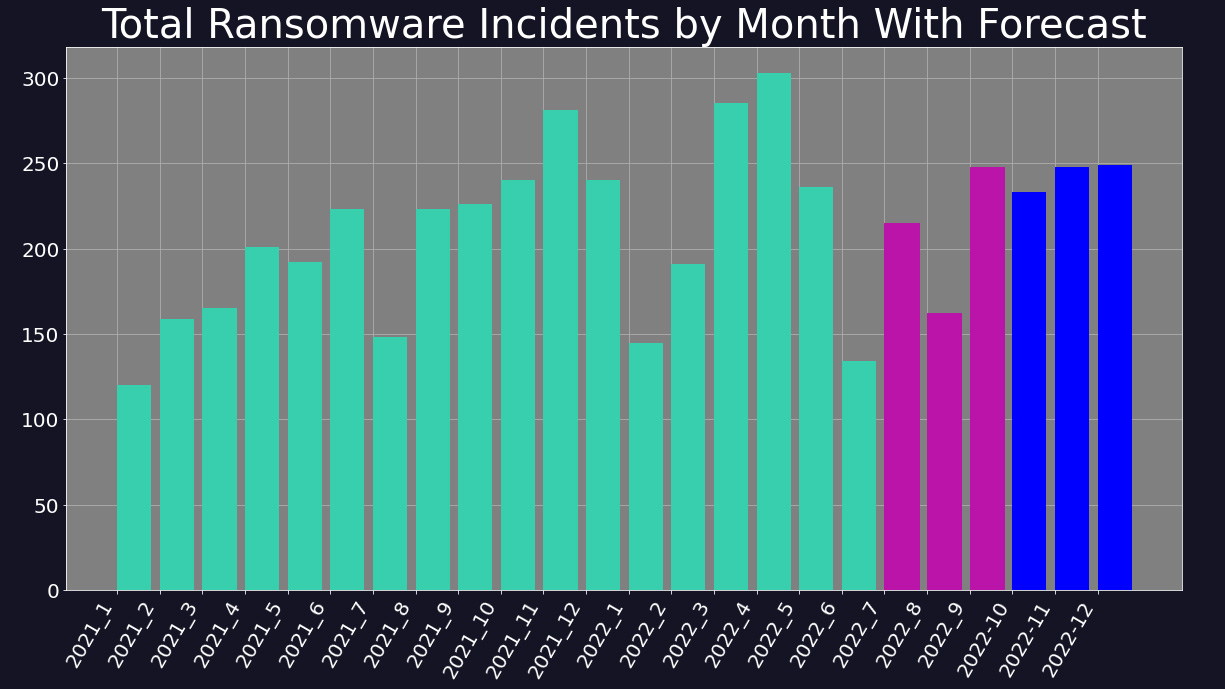
Digital Shadows forecasts a rise in activity in Q4 2022. This is not unusual, as commercial events such as Black Friday and Cyber Monday often coincide with an increase in malicious activity online, while online shopping around Christmas is exploited by threat actors with phishing campaigns.
After falling prey to a distributed denial of service (DDoS) attack in August, which took down its website for several days, the LockBit group vowed to be ‘more aggressive’ and stated that it was recruiting new members. This may be linked to the increase of attacks at the end of Q3, and indeed the LockBit group saw its highest ever share of international ransomware activity at 40%.
Concerns have also been raised due to the alleged leak of a LockBit 3.0 ‘builder’ in September. If legitimate, this would allow rival threat actors to create their own version of LockBit ransomware, and as such the leak could precede a spike in use of the highly-effective malware throughout Q4 and beyond.

Rory Bathgate is Features and Multimedia Editor at ITPro, overseeing all in-depth content and case studies. He can also be found co-hosting the ITPro Podcast with Jane McCallion, swapping a keyboard for a microphone to discuss the latest learnings with thought leaders from across the tech sector.
In his free time, Rory enjoys photography, video editing, and good science fiction. After graduating from the University of Kent with a BA in English and American Literature, Rory undertook an MA in Eighteenth-Century Studies at King’s College London. He joined ITPro in 2022 as a graduate, following four years in student journalism. You can contact Rory at rory.bathgate@futurenet.com or on LinkedIn.
-
 Cleo attack victim list grows as Hertz confirms customer data stolen
Cleo attack victim list grows as Hertz confirms customer data stolenNews Hertz has confirmed it suffered a data breach as a result of the Cleo zero-day vulnerability in late 2024, with the car rental giant warning that customer data was stolen.
By Ross Kelly
-
 Lateral moves in tech: Why leaders should support employee mobility
Lateral moves in tech: Why leaders should support employee mobilityIn-depth Encouraging staff to switch roles can have long-term benefits for skills in the tech sector
By Keri Allan
-
 Cleo attack victim list grows as Hertz confirms customer data stolen – and security experts say it won't be the last
Cleo attack victim list grows as Hertz confirms customer data stolen – and security experts say it won't be the lastNews Hertz has confirmed it suffered a data breach as a result of the Cleo zero-day vulnerability in late 2024, with the car rental giant warning that customer data was stolen.
By Ross Kelly
-
 ‘Phishing kits are a force multiplier': Cheap cyber crime kits can be bought on the dark web for less than $25 – and experts warn it’s lowering the barrier of entry for amateur hackers
‘Phishing kits are a force multiplier': Cheap cyber crime kits can be bought on the dark web for less than $25 – and experts warn it’s lowering the barrier of entry for amateur hackersNews Research from NordVPN shows phishing kits are now widely available on the dark web and via messaging apps like Telegram, and are often selling for less than $25.
By Emma Woollacott
-
 Healthcare systems are rife with exploits — and ransomware gangs have noticed
Healthcare systems are rife with exploits — and ransomware gangs have noticedNews Nearly nine-in-ten healthcare organizations have medical devices that are vulnerable to exploits, and ransomware groups are taking notice.
By Nicole Kobie
-
 Alleged LockBit developer extradited to the US
Alleged LockBit developer extradited to the USNews A Russian-Israeli man has been extradited to the US amid accusations of being a key LockBit ransomware developer.
By Emma Woollacott
-
 February was the worst month on record for ransomware attacks – and one threat group had a field day
February was the worst month on record for ransomware attacks – and one threat group had a field dayNews February 2025 was the worst month on record for the number of ransomware attacks, according to new research from Bitdefender.
By Emma Woollacott
-
 CISA issues warning over Medusa ransomware after 300 victims from critical sectors impacted
CISA issues warning over Medusa ransomware after 300 victims from critical sectors impactedNews The Medusa ransomware as a Service operation compromised twice as many organizations at the start of 2025 compared to 2024
By Solomon Klappholz
-
 Warning issued over prolific 'Ghost' ransomware group
Warning issued over prolific 'Ghost' ransomware groupNews The Ghost ransomware group is known to act fast and exploit vulnerabilities in public-facing appliances
By Solomon Klappholz
-
 The Zservers takedown is another big win for law enforcement
The Zservers takedown is another big win for law enforcementNews LockBit has been dealt another blow by law enforcement after Dutch police took 127 of its servers offline
By Solomon Klappholz