Log4Shell: New numbers reveal the scale of the critical software exploit
Researchers detail how much the Log4J vulnerability is being exploited and who is being targeted the most


The scale of the threat associated with the recently discovered Log4Shell vulnerability has been quantified for the first time, with nearly 1 million attack attempts launched in just 72 hours following the critical vulnerability's disclosure on 9 December.
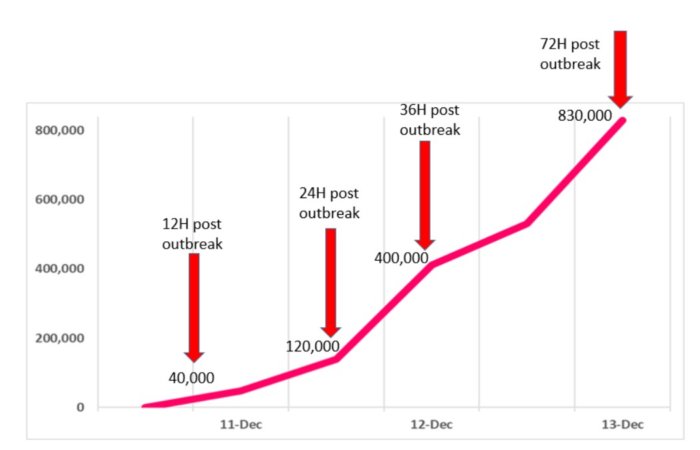
Experts from Check Point Research published observations from early vulnerability scans on Tuesday, which revealed attempts to exploit systems vulnerable to Log4Shell increased from 40,000 in the immediate 12-hour period following disclosure, to 830,000 attempts after just three days.
Researchers said the vulnerability "is clearly one of the most serious vulnerabilities on the internet in recent years, and the potential for damage is incalculable". The security community is still scrambling to fully understand the attack surface for Log4Shell, the RCE vulnerability in the log4j Java logging component revealed last week.
"The number of combinations of how to exploit it give the attacker many alternatives to bypass newly introduced protections," researchers said. "It means that one layer of protection is not enough, and only multi-layered security posture would provide a resilient protection. Three days after the outbreak, we are summing up what we see until now, which is clearly a cyber pandemic that hasn’t seen its peak yet."
The industry has banded together to share quick fixes and easy ways to remediate issues in the enterprise, but research has shown attackers are finding new ways to exploit the vulnerability.
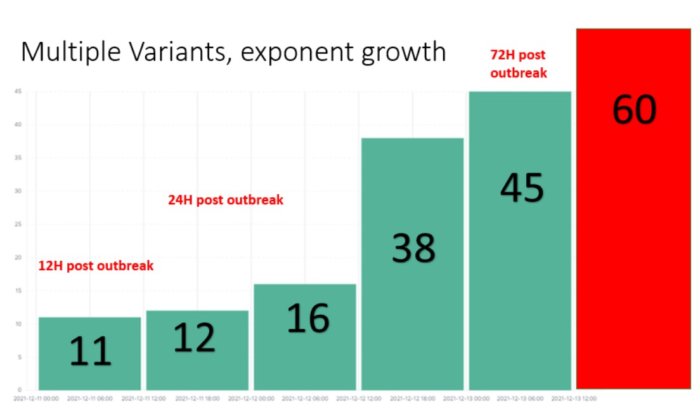
Check Point Research said it has seen a steady increase in exploit evolutions over the course of 72 hours since Log4Shell's discovery, with more than 60 different methods already in use.
Findings from their investigation are said to resemble a cyber pandemic, in which attacks spread quickly and evolve continually to break through attempted fixes.
Get the ITPro daily newsletter
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Who is most vulnerable to Log4Shell?
The investigation also looked at corporate exposure to Log4Shell and concluded that a global average of 40% of all networks across the world could be vulnerable to log4j flaws.
Australia and New Zealand were found to be the most exposed at 46.2% of all corporate networks, with Europe close behind with 42.2%. Asia and North America are the least exposed at 37.7% and 36.4% respectively.
Value-added resellers and the education sectors were found to be particularly vulnerable compared to other industries, with around half of all organisations across the two sectors thought to be affected.
Unlike with the COVID-19 pandemic, the retail and hospitality sectors are thought to be the least affected, with around a quarter of organisations exposed to log4j-based attacks.
RELATED RESOURCE

Modernise endpoint protection and leave your legacy challenges behind
The risk of keeping your legacy endpoint security tools
There is significant pressure felt by security teams across the globe to fully patch the vulnerability. Upgrading to the latest version of the log4j library, version 2.15.0, is so far the best mitigation against the flaw.
Also this week, the US' Cybersecurity and Infrastructure Security Agency (CISA) told all federal agencies they had until 24 December to patch systems and protect them from Log4Shell.
It follows a recent increase in focus on patch management across the US public sector, led by CISA, after the agency issued deadlines to all federal departments in November to patch a 300-strong list of major cyber security vulnerabilities. The first deadline passed weeks later but CISA declined to confirm to IT Pro if all federal agencies had met the requirements in time.
Check Point Research said it thinks the vulnerability in the log4j library "will stay with us for years to come" due to the complexity in patching it and the ease in which attackers can exploit it.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.
-
 Should AI PCs be part of your next hardware refresh?
Should AI PCs be part of your next hardware refresh?AI PCs are fast becoming a business staple and a surefire way to future-proof your business
By Bobby Hellard Published
-
 Westcon-Comstor and Vectra AI launch brace of new channel initiatives
Westcon-Comstor and Vectra AI launch brace of new channel initiativesNews Westcon-Comstor and Vectra AI have announced the launch of two new channel growth initiatives focused on the managed security service provider (MSSP) space and AWS Marketplace.
By Daniel Todd Published
-
 Hackers are targeting Ivanti VPN users again – here’s what you need to know
Hackers are targeting Ivanti VPN users again – here’s what you need to knowNews Ivanti has re-patched a security flaw in its Connect Secure VPN appliances that's been exploited by a China-linked espionage group since at least the middle of March.
By Emma Woollacott Published
-
 Broadcom issues urgent alert over three VMware zero-days
Broadcom issues urgent alert over three VMware zero-daysNews The firm says it has information to suggest all three are being exploited in the wild
By Solomon Klappholz Published
-
 Nakivo backup flaw still present on some systems months after firms’ ‘silent patch’, researchers claim
Nakivo backup flaw still present on some systems months after firms’ ‘silent patch’, researchers claimNews Over 200 vulnerable Nakivo backup instances have been identified months after the firm silently patched a security flaw.
By Solomon Klappholz Published
-
 Everything you need to know about the Microsoft Power Pages vulnerability
Everything you need to know about the Microsoft Power Pages vulnerabilityNews A severe Microsoft Power Pages vulnerability has been fixed after cyber criminals were found to have been exploiting unpatched systems in the wild.
By Solomon Klappholz Published
-
 Vulnerability management complexity is leaving enterprises at serious risk
Vulnerability management complexity is leaving enterprises at serious riskNews Fragmented data and siloed processes mean remediation is taking too long
By Emma Woollacott Published
-
 A critical Ivanti flaw is being exploited in the wild – here’s what you need to know
A critical Ivanti flaw is being exploited in the wild – here’s what you need to knowNews Cyber criminals are actively exploiting a critical RCE flaw affecting Ivanti Connect Secure appliances
By Solomon Klappholz Published
-
 Researchers claim an AMD security flaw could let hackers access encrypted data
Researchers claim an AMD security flaw could let hackers access encrypted dataNews Using only a $10 test rig, researchers were able to pull off the badRAM attack
By Solomon Klappholz Published
-
 The threat prevention buyer's guide
The threat prevention buyer's guideWhitepaper Find the best advanced and file-based threat protection solution for you
By ITPro Published