Researchers warn of spear-phishing exploit in Google Docs
Hackers have found a way to use Google's comment function to dupe victims into clicking on malicious links


Threat actors have found an exploit in a Google Docs comment feature that uses Google's own automated email notification function to send malicious links.
Email security specialists Avanan said it had notified Google of the flaw on 3 January after noticing a spike in usage over December 2021.
The attack involves hackers using their own Google accounts to create a Google Doc, to which they simply invite a target using the comments section with the '@' function. This automatically sends a notification email to the intended target's inbox, informing them that another user has commented on a document and mentioned them. The email is from Google, and so it is difficult to tell whether the message is malicious.
However, the comment on the email can be loaded with a malicious link for phishing sites or malware, and there appears to be no filtering mechanisms in place, according to Avanan. What's more, the hackers email address isn't shown in the notification; the recipient will only see a name, making it very easy to impersonate a victim's colleagues or friends.
The exploit is very simple to execute and has been available since the Autumn of 2020. Google has attempted to mitigate the problem but are yet to fully close it off, partly due to the fact it requires its own email service to work.
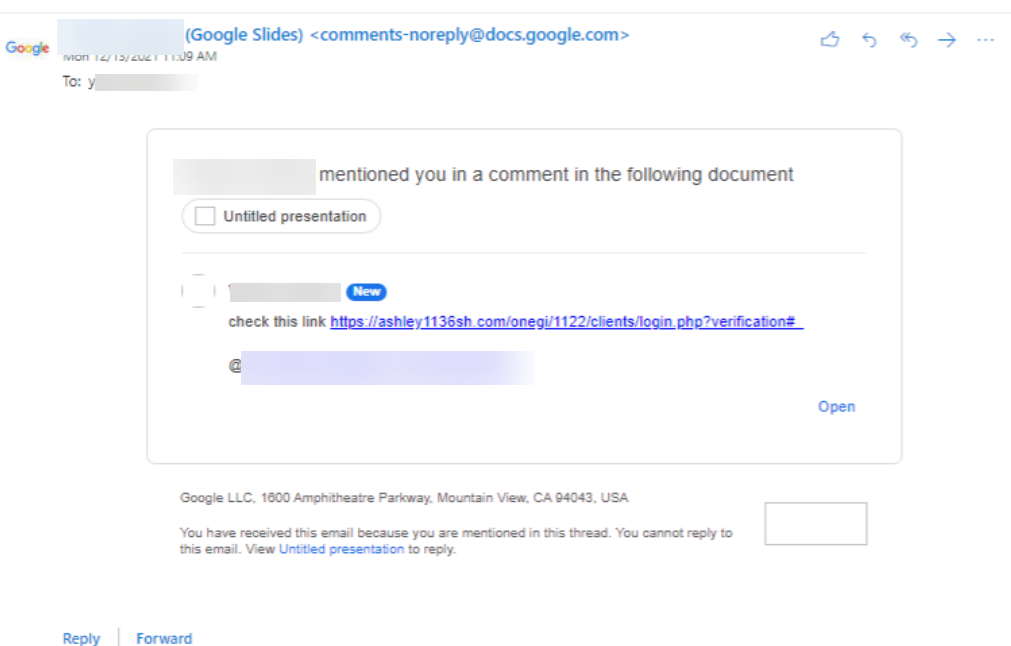
Attackers also aren't required to share the document with their targets, as simply messaging them is enough to trigger the email alert. Avanan suggests that the same techniques work on Google Slides and other collaboration tools within the Google's Workspace suite.
Outlook users appear to be the favoured targets, according to Avanan, but it's believed the exploit has used over 100 Google accounts and has already attacked 500 inboxes across 30 different organisations.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
To protect yourself, and your organisation, Avanan recommends avoiding clicking on links in emails, deploying stricter file-sharing rules across Google Workspace, and using an Internet security service from a trusted vendor, particularly one that features phishing URL protection.
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.
-
 Cyber resilience in the UK: learning to take the punches
Cyber resilience in the UK: learning to take the punchesColumn UK law now puts resilience at the centre of cybersecurity strategies – but is legislation simply catching up with enterprise understanding that resilience is more than just an IT issue?
-
 CISPE claims European Commission gave Broadcom a ‘blank cheque to raise prices, lock-in, and squeeze customers’ with VMware deal
CISPE claims European Commission gave Broadcom a ‘blank cheque to raise prices, lock-in, and squeeze customers’ with VMware dealNews Cloud providers have issued a formal response to the General Court of the European Union after the Commission defended its approval of the deal
-
 A strategic approach to security: Intelligent, collaborative, and efficient
A strategic approach to security: Intelligent, collaborative, and efficientwhitepaper How your security fabric can address the challenges of new tech investment
-
 Anticipate, prevent, and minimize the impact of business disruptions
Anticipate, prevent, and minimize the impact of business disruptionsWhitepaper Nine best practices for building operational resilience
-
 Thwart cyberthreats fast with security operations + AI Ops
Thwart cyberthreats fast with security operations + AI OpsWhitepaper How automated collaboration saves the day
-
 Three steps to transforming security operations
Three steps to transforming security operationsWhitepaper How to be more agile, effective, collaborative, and scalable
-
 Top ten ways to anticipate, eliminate, and defeat cyber threats like a boss
Top ten ways to anticipate, eliminate, and defeat cyber threats like a bossWhitepaper Improve your cyber resilience and vulnerability management while speeding up response times
-
 Automation antidotes for the top poisons in cyber security management
Automation antidotes for the top poisons in cyber security managementWhitepaper How orchestration and collaboration tools can provide a healthy defense against the most serious threats
-
 A prudent approach to major security incidents
A prudent approach to major security incidentsWhitepaper Establish an effective strategy across four phases
-
 Cybercriminals are resilient. How about you?
Cybercriminals are resilient. How about you?Whitepaper Stay ahead of those agile bad actors
