Could Python in Excel be a boon for cryptocurrency miners?
Free Python compute resource on offer via Microsoft 365 beta preview – what could possibly go wrong?


Microsoft has unveiled Python in Excel, which allows a user to execute Python calculations using Azure Container instances. Has the company learned nothing from the Azure Pipelines cryptomining fiasco?
On the surface, giving Excel users the power to natively combine Python and Excel analytics in the same workbook is a good idea.
CATCH UP ON THE NEWS
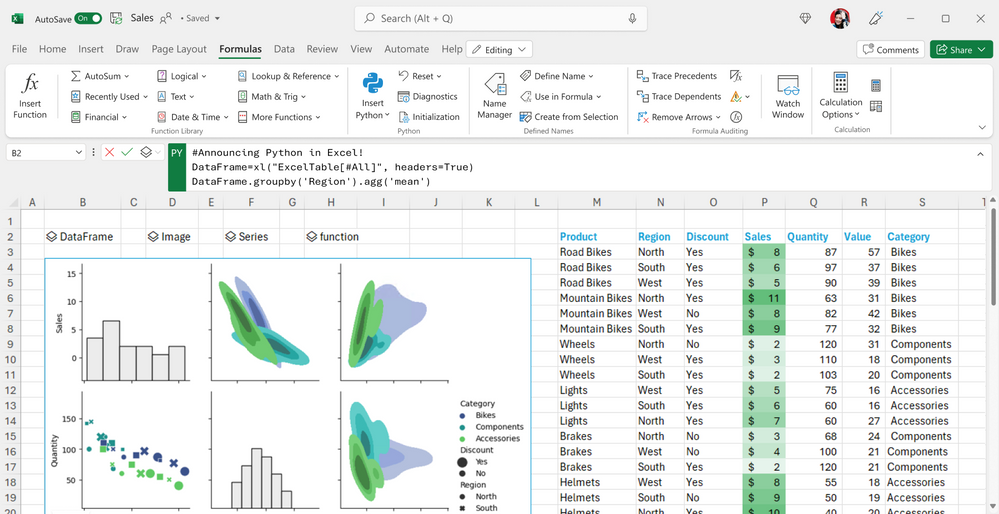
Typing Python into a cell, running calculations in the cloud, and receiving results in the worksheet is handy, where complex calculations and visualizations could otherwise stress a spreadsheet. As long, of course, as you have a robust connection, and you don’t mind beaming your work to the cloud.
Unless we’re very much mistaken, however, it doesn’t take a huge leap of the imagination to spot the potential for abuse. After all, one needs only look to Microsoft’s recent past to see how people have exploited a certain naivete to mine cryptocurrency.
Microsoft cryptomining abuse: Is this a case of history repeating itself?
At first glance, the implementation – currently a public preview in the Excel beta channel – looks secure. The Python code runs on a hypervisor in isolated containers built on Azure Container instances. It doesn’t have network or access to the local computer. It can’t get hold of a user token or access the user’s Microsoft 365 account.
However, Excel performs calculations and executes Python in the Microsoft Cloud, which is where the problems could begin.
AZURE PIPELINES: WHAT HAPPENED?

We’re still waiting for Microsoft to clarify what steps it’s taken to prevent such abuse, but the firm certainly has form when it comes to cryptominers abusing its resources. It gave away free compute with Azure Pipelines several years ago, largesse which was soon abused.
It eventually dissuaded Azure Piplines cryptominers by asking users to apply for a free grant of concurrent pipelines. This request took days to process. Even attackers willing to surrender their details were forced to wait, thus ruling out automated attacks.
Cryptocurrency mining is easily accomplished in Python; you just need hefty computational power to generate the relevant hashcode – which is where the Microsoft Cloud comes in.
Sign up today and you will receive a free copy of our Future Focus 2025 report - the leading guidance on AI, cybersecurity and other IT challenges as per 700+ senior executives
Bitcoin mining, for example, is relatively simple to run in Python, although you’d need network access to synchronize transactions. Microsoft has stated the code will not have network access, but it’s not hard to imagine a threat actor finding a workaround and using Microsoft’s cloud resources for at least part of the process.
The new Excel feature requires only a Microsoft 365 account. No additional setup is required. And although workbooks from the internet or untrusted sources are subject to extra checks, there appears to be no restriction on the code you run other than the content of the Anaconda Distribution for Python, on which the system is based.
Mitigating abuse when using Python in Excel
Microsoft is keen to emphasize the security measures it’s taken, detailing this in a dedicated page on its site, Promising enterprise-level security and container isolation, however, means little if somebody decides to execute Python code in the Microsoft Cloud for nefarious purposes. There’s also scope for abuse via excessive compute usage, for example.
RELATED RESOURCE
Building intelligent, resilient and sustainable supply chain
Discover the exponential performance that's unlocked when you connect the processes, applications, and data that run your supply chain.
We’re really hoping we’re wrong here, though, and Microsoft has a well thought-out mitigation strategy. Because, after all, Python in Excel makes use of the Anaconda distribution, which includes libraries for data manipulation and modelling – we can’t imagine it being too difficult to set it a challenge that could cause issues.
The company has also published a list of registry settings so IT admins (or anyone with access) can disable all security warnings for Python in Excel. One such instruction is: “Use this command to disable all security warnings. This is the default setting for Python in Excel”. But hey – this is all beta code, right?
Based on the information available at the time of writing, there appear to be no guardrails to prevent excessive resource usage.
READ MORE

Microsoft will need to ensure these are in place or face another Azure Pipelines incident, where cyber criminals abuse good intentions – and perhaps naivete.
There’s every chance Microsoft will make changes to this feature between now and general availability. The company has also warned that, although the preview is bundled with a user’s Microsoft 365 subscription, “after the Preview, some functionality will be restricted without a paid license”. This could be a critical line of defense.
ITPro contacted Microsoft to learn how it intended to dissuade abuse of its new Python in Excel service, but didn't receive a reply at the time of writing. This article will be updated when a spokesperson reaches back.

Do you want to make your voice heard as an IT decision maker? The ITPro Network is a select group of senior IT professionals who contribute to ITPro’s unique content through interviews, opinion, podcast appearances and more.
Members also get access to monthly group chats and other exclusive content and events. Interested? Fill out this form to apply.
(Please note we cannot accept applications from vendors at this time).

Richard Speed is an expert in databases, DevOps and IT regulations and governance. He was previously a Staff Writer for ITPro, CloudPro and ChannelPro, before going freelance. He first joined Future in 2023 having worked as a reporter for The Register. He has also attended numerous domestic and international events, including Microsoft's Build and Ignite conferences and both US and EU KubeCons.
Prior to joining The Register, he spent a number of years working in IT in the pharmaceutical and financial sectors.
-
 Microsoft 365 price hikes have landed the tech giant in hot water
Microsoft 365 price hikes have landed the tech giant in hot waterNews Australian regulators have filed a lawsuit against Microsoft for allegedly misleading users over Microsoft 365 pricing changes.
-
 Microsoft Office 2016 and 2019 are heading for the scrapheap next month – but there could be a lifeline for those unable to upgrade
Microsoft Office 2016 and 2019 are heading for the scrapheap next month – but there could be a lifeline for those unable to upgradeNews The tech giant has urged Office 2016 and Office 2019 users to upgrade before the deadline passes
-
 Salesforce says ‘Microsoft’s anticompetitive tying of Teams' harmed business in triumphant response to EU concessions agreement
Salesforce says ‘Microsoft’s anticompetitive tying of Teams' harmed business in triumphant response to EU concessions agreementNews Microsoft has agreed to make versions of its Office solutions suite available without Teams – and at a reduced price
-
 Microsoft justifies 365 price increases after MP concerns
Microsoft justifies 365 price increases after MP concernsNews Microsoft’s UK VP of external affairs has defended the tech giant's price increases
-
 Microsoft is ending support for the Remote Desktop app – here are three alternatives you can try instead
Microsoft is ending support for the Remote Desktop app – here are three alternatives you can try insteadNews Microsoft has announced plans to end support for its Remote Desktop application in just over two months.
-
 Everything you need to know about the Microsoft outage
Everything you need to know about the Microsoft outageNews After a day of chaos, the worst of the Microsoft outage appears to have passed, but some problems still remain
-
 Microsoft's huge AI spending has investors worried – now the company is changing its financial reporting to highlight successes
Microsoft's huge AI spending has investors worried – now the company is changing its financial reporting to highlight successesNews The move comes as investors want more evidence that Microsoft’s AI investment will pay off
-
 Zoom wants to take on Google and Microsoft with its own Docs
Zoom wants to take on Google and Microsoft with its own DocsNews Zoom Docs arrives loaded with generative AI – and the company hopes to mount a serious challenge against industry heavyweights

