Cloud Security
Discover expert analysis on cloud security with news, features and insights from the team at IT Pro.
-

Solution Brief: Find Known and Unknown Threats Faster
Download Now
By ITPro Published
-

AWS eBook: Evolve Your Cloud Security on AWS
Download Now
By ITPro Published
-
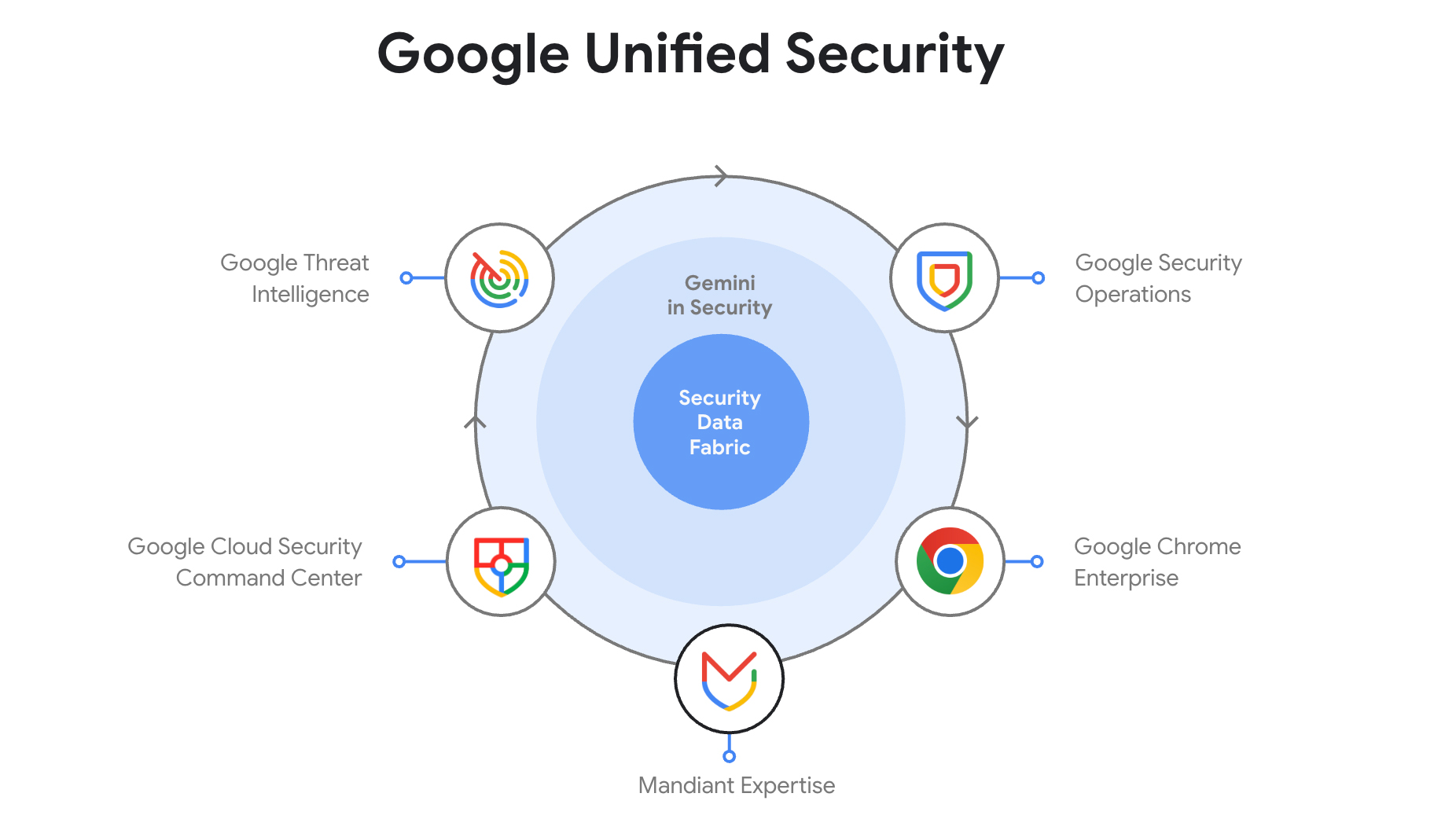
Google Cloud wants to tackle cyber complexity – here's how it plans to do it
News Google Unified Security will combine all the security services under Google’s umbrella in one combined cloud platform
By Rory Bathgate Published
News -

Enterprise AI is surging, but is security keeping up?
News Enterprise AI workloads have skyrocketed globally and so has scrutiny from security teams
By Solomon Klappholz Published
News -

AI is putting your cloud workloads at risk
News Many AI deployments are defined by risky misconfigurations and access controls
By George Fitzmaurice Published
News -

The Wiz acquisition stakes Google's claim as the go-to hyperscaler for cloud security
Analysis The Wiz acquisition could have monumental implications for the cloud security sector, with Google raising the stakes for competitors and industry vendors.
By Ross Kelly Published
Analysis -

Google confirms Wiz acquisition in record-breaking $32 billion deal
News Google has confirmed plans to acquire cloud security firm Wiz in a deal worth $32 billion.
By Nicole Kobie Published
News -

US Cloud case studies: Healthcare
Whitepaper Save money, improve service quality, and address critical IT issues
By ITPro Published
Whitepaper -

US Cloud case studies: Financial
Whitepaper The #1 Microsoft Support Alternative
By ITPro Published
Whitepaper -

The Microsoft Unified Support replacement
Whitepaper Save 30% - 50% on a true comparable replacement for Microsoft Unified Support
By ITPro Published
Whitepaper -
Azure cost optimization
Whitepaper Eight-week service offering built to help businesses achieve annual cost savings on Azure Cloud Service
By ITPro Published
Whitepaper -

What is a secure web gateway (SWG) and next-gen SWG?
Explainer Implemented correctly, a SWG can keep businesses shielded from malicious traffic and firmly enforce secure policies
By Max Slater-Robins Published
Explainer